Introduction
In today’s fast-paced digital world, businesses are undergoing significant changes. Digital transformation is no longer just a buzzword; it’s a necessity. Companies are adopting new technologies to streamline operations, enhance customer experiences, and stay competitive. However, as organizations embrace these digital initiatives, they often overlook a critical aspect: cybersecurity. This oversight can lead to severe consequences.The role of cybersecurity in digital transformation cannot be overstated.
As businesses shift to digital platforms, they expose themselves to various cyber threats. These threats can compromise sensitive data and disrupt operations. Therefore, integrating cybersecurity into your digital transformation strategy is essential for success.

Image: Digital Transformation
When I first started my journey in digital transformation, I was excited about the possibilities. We implemented new software and cloud services that promised to enhance efficiency. However, we soon realized that our cybersecurity measures were lagging behind. A minor breach nearly cost us valuable client information and damaged our reputation. This experience taught me that the role of cybersecurity in digital transformation is not just about protection; it’s about enabling growth.
As we dive deeper into this topic, we’ll explore the risks associated with digital change and how robust cybersecurity measures can safeguard your initiatives. We’ll also discuss best practices for securing digital initiatives and fostering a culture of cybersecurity within your organization.
Understanding the role of cybersecurity in digital transformation is crucial for any business looking to thrive in the digital age. Cybersecurity isn’t just an IT issue; it’s a business imperative. You can’t afford to overlook security when implementing new technologies. In fact, doing so could jeopardize all the benefits you aim to achieve through digital transformation.As we move forward, let’s examine what digital transformation entails and why cybersecurity is critical during this process.
What is Digital Transformation?
Digital transformation refers to the process of integrating digital technology into all areas of a business. This shift fundamentally changes how businesses operate and deliver value to customers. It’s not just about adopting new tools; it’s about rethinking your entire business model.
In my experience, digital transformation involves several key components:
- Technology Adoption: This includes cloud computing, artificial intelligence, and data analytics. These technologies enable businesses to operate more efficiently and make data-driven decisions.
- Cultural Change: Successful digital transformation requires a shift in company culture. Employees must embrace new ways of working and be open to change.
- Customer Experience: Enhancing customer interactions through digital channels is a primary goal. Businesses aim to provide seamless experiences that meet customer expectations.
- Operational Efficiency: Digital tools can streamline processes, reduce costs, and increase productivity.
However, as organizations embark on this journey, they must recognize the role of cybersecurity in digital transformation. With every new technology adopted, there comes an increased risk of cyber threats. For example, when we implemented a new customer relationship management (CRM) system, we saw immediate benefits in managing client interactions. But we also faced challenges regarding data security.

Image: A team discussing Digital Transformation Strategies
The importance of cybersecurity in digital change cannot be ignored. Each technology you adopt can create vulnerabilities that hackers may exploit. For instance, when our company moved to cloud storage solutions, we had to rethink our security protocols. We realized that securing our digital initiatives was just as crucial as the technology itself.
Moreover, many organizations fail to understand that the role of cybersecurity in digital transformation extends beyond just protecting data; it also involves maintaining trust with customers. A single breach can lead to loss of business and damage to your brand reputation.
As businesses continue to evolve digitally, they must prioritize cybersecurity from the outset. This means incorporating security measures into every phase of the transformation process—from planning and implementation to ongoing management.In summary, digital transformation is more than just technology adoption; it’s a holistic approach that requires careful consideration of security implications. As we explore the next section, we will discuss why cybersecurity is critical during this transformative journey.
Why is Cybersecurity Critical in Digital Transformation?
As organizations embrace digital transformation, they often encounter a myriad of challenges. One of the most pressing issues is cybersecurity. The rapid integration of digital technologies can expose businesses to various vulnerabilities. Understanding the role of cybersecurity in digital transformation is essential for safeguarding assets and ensuring continuity.
When we embarked on our digital transformation journey, we quickly realized that the risks were not just theoretical. Cyber threats became more sophisticated, targeting our newly adopted technologies. For instance, after launching an online service platform, we experienced several phishing attempts aimed at our employees. This was a wake-up call about the importance of cybersecurity in digital change.
Increased Attack Surfaces
Digital transformation often leads to an expanded attack surface. As businesses adopt cloud services, mobile applications, and IoT devices, they inadvertently create more entry points for cybercriminals. Each new technology can introduce vulnerabilities if not properly secured. In my experience, we had to conduct thorough risk assessments to identify potential weaknesses in our systems.
Common Cyber Threats
Several common cyber threats arise during digital transformation:
- Phishing Attacks: These attacks trick employees into revealing sensitive information.
- Ransomware: Malicious software that encrypts data and demands payment for its release.
- Data Breaches: Unauthorized access to sensitive data can lead to significant financial and reputational damage.
Understanding these threats is crucial for developing effective security strategies. The role of cybersecurity in digital transformation is to mitigate these risks through proactive measures.

Image: Statistics on Cyber threats faced by Businesses
Regulatory Compliance
Another critical aspect is regulatory compliance. Many industries are subject to strict regulations regarding data protection. Failing to comply can result in hefty fines and legal repercussions. By prioritizing cybersecurity, organizations can ensure they meet these requirements while also protecting their customers’ data.
In our case, we had to align our digital initiatives with GDPR regulations when expanding into European markets. This involved not only securing our systems but also implementing transparent data handling practices.
Building Trust with Customers
Finally, cybersecurity plays a vital role in building trust with customers. In today’s digital landscape, consumers are increasingly aware of data privacy issues. A single security breach can erode customer confidence and lead to loss of business. By demonstrating a commitment to cybersecurity, companies can foster trust and loyalty among their clients.
The importance of the role of cybersecurity in digital transformation cannot be overstated. It’s not just about protecting technology; it’s about safeguarding your entire business ecosystem. As we move forward, let’s explore the specific risks associated with digital transformation and how organizations can address them effectively.
What Are the Risks Associated with Digital Transformation and Cybersecurity?
Digital transformation offers numerous benefits, but it also comes with significant risks. As organizations integrate new technologies, they expose themselves to various vulnerabilities that can lead to severe consequences. Understanding these risks is crucial for any business aiming to succeed in the digital age. This is where the role of cybersecurity in digital transformation becomes paramount.
Expanded Attack Surfaces
One of the most significant risks associated with digital transformation is the expanded attack surface. As businesses adopt cloud services, mobile applications, and IoT devices, they create more entry points for cybercriminals. Each new technology can introduce vulnerabilities if not properly secured. In my experience, when we shifted to a cloud-based infrastructure, we had to reassess our entire security framework. This reassessment highlighted the critical nature of cybersecurity in digital change.
Data Breaches
Data breaches are another major risk during digital transformation. When companies move sensitive information to digital platforms, they become targets for hackers. A single breach can expose confidential data and lead to financial losses and reputational damage. For example, after implementing a new customer database system, we experienced a minor breach that compromised some client information. It was a stark reminder of the role of cybersecurity in digital transformation.
Ransomware Attacks
Ransomware attacks are on the rise, particularly during periods of rapid digital change. Cybercriminals use this malicious software to encrypt data and demand payment for its release. These attacks can cripple operations and lead to significant downtime. In our organization, we had a close call with ransomware when an employee inadvertently clicked on a malicious link. Fortunately, our cybersecurity protocols were robust enough to prevent a full-scale attack.
Insider Threats
Insider threats pose another risk during digital transformation. Employees with access to sensitive information can inadvertently or intentionally compromise security. This risk is heightened when organizations implement new systems without proper training or oversight. We learned this lesson the hard way when an employee mistakenly shared sensitive data due to a lack of understanding about our new tools.
Compliance Issues
Regulatory compliance is yet another area of concern. Many industries have strict regulations regarding data protection and privacy. Non-compliance can result in hefty fines and legal repercussions. By prioritizing cybersecurity in your digital initiatives, you can ensure compliance while protecting your customers’ data—a vital aspect of the role of cybersecurity in digital transformation.

Image: Compliance with Data protection regulations.
Reputation Damage
Lastly, the reputational damage caused by security incidents cannot be overlooked. In today’s digital landscape, consumers are more aware of data privacy issues than ever before. A single breach can erode customer confidence and lead to loss of business. By demonstrating a commitment to cybersecurity through effective measures, companies can foster trust among their clients.
In summary, understanding the risks associated with digital transformation is essential for any organization looking to thrive in the digital age. The integration of new technologies brings challenges that must be addressed through robust cybersecurity measures. As we continue this journey, let’s explore how cybersecurity supports digital transformation efforts effectively.
How Does Cybersecurity Support Digital Transformation?
As organizations navigate the complexities of digital transformation, cybersecurity emerges as a vital ally. Rather than being an afterthought, the role of cybersecurity in digital transformation should be integrated into every stage of the process. By doing so, businesses can not only protect their assets but also enable innovation and growth.
Enabling Secure Digital Initiatives
Cybersecurity plays a crucial role in enabling secure digital initiatives. When businesses adopt new technologies, they must ensure that these tools are protected from cyber threats. For instance, when we launched a new e-commerce platform, we made cybersecurity a top priority. We implemented multi-factor authentication and encryption protocols to safeguard customer data. This proactive approach allowed us to focus on growth while knowing that our systems were secure.
Risk Management
Effective risk management is another way cybersecurity supports digital transformation. Organizations need to identify potential vulnerabilities and assess their impact on operations. By conducting regular security audits and penetration testing, businesses can uncover weaknesses before they are exploited. In my experience, we established a dedicated security team that regularly evaluated our systems. This commitment to identifying risks enhanced our overall security posture and reinforced cybersecurity in digital change.
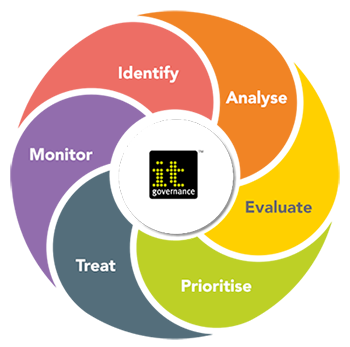
Image: Risk Management | IT governance
Compliance Assurance
Compliance with regulations is critical during digital transformation. Many industries face stringent data protection laws that require organizations to implement robust security measures. By prioritizing cybersecurity, companies can ensure they meet these regulations while protecting sensitive information.
For example, when we expanded our services into new markets, we invested in compliance training for our staff to ensure everyone understood the legal requirements. This step not only safeguarded our data but also demonstrated our commitment to the role of cybersecurity in digital transformation.
Building Customer Trust
Another significant benefit of integrating cybersecurity into digital transformation is building customer trust. Consumers are increasingly concerned about how their data is handled. By implementing strong security measures, businesses can reassure clients that their information is safe. For instance, after enhancing our security protocols, we noticed a marked increase in customer confidence and engagement with our services.
Fostering Innovation
Contrary to the belief that cybersecurity stifles innovation, it can actually foster it. When employees feel secure in their digital environment, they are more likely to explore new ideas and solutions. In our organization, after implementing comprehensive cybersecurity training programs, we saw a surge in innovative projects proposed by team members. They felt empowered to experiment with new technologies without the fear of compromising security.
Continuous Improvement
Lastly, cybersecurity supports continuous improvement in digital transformation efforts. As threats evolve, so must your security strategies. Regularly updating your security measures ensures that you stay ahead of potential attacks. We adopted an agile approach to cybersecurity, allowing us to quickly adapt to new threats and challenges as they arose.
In summary, the role of cybersecurity in digital transformation is multifaceted and essential for success. By enabling secure digital initiatives, managing risks effectively, ensuring compliance, building customer trust, fostering innovation, and promoting continuous improvement, organizations can navigate their digital journeys confidently. As we move forward, let’s delve into best practices for securing digital initiatives effectively.
What Are Best Practices for Securing Digital Initiatives?
As organizations embark on their digital transformation journeys, implementing best practices for cybersecurity is essential. These practices not only protect sensitive data but also ensure the success of digital initiatives. Understanding the role of cybersecurity in digital transformation helps businesses create a robust security framework that mitigates risks effectively.
1. Conduct Regular Risk Assessments
One of the first steps in securing digital initiatives is conducting regular risk assessments. This process involves identifying vulnerabilities within your systems and evaluating the potential impact of various threats. In my experience, we established a routine where our security team conducted quarterly assessments. This proactive approach allowed us to address vulnerabilities before they could be exploited, reinforcing the importance of cybersecurity in digital change.
2. Implement Secure-by-Design Principles
Adopting secure-by-design principles means incorporating security measures from the outset of any digital initiative. This approach ensures that security is not an afterthought but a fundamental component of the development process. For instance, when we developed a new mobile application, we integrated encryption and secure coding practices from day one. This commitment to security helped us avoid costly fixes later on and highlighted the role of cybersecurity in digital transformation.
Image Placeholder 2: An infographic illustrating secure-by-design principles.
3. Strengthen Authentication and Access Controls
Strong authentication and access controls are critical for protecting sensitive data. Implementing multi-factor authentication (MFA) adds an extra layer of security, making it more difficult for unauthorized users to gain access. In our organization, we mandated MFA for all employees accessing sensitive systems. This simple yet effective measure significantly reduced our risk of unauthorized access and reinforced cybersecurity in digital change.
4. Train Employees on Cybersecurity Awareness
Employees are often the first line of defense against cyber threats. Providing comprehensive training on cybersecurity awareness can empower your team to recognize and respond to potential threats effectively. We implemented a series of workshops and online courses to educate our staff about phishing attacks, password management, and safe browsing practices. This investment in employee training not only enhanced our security posture but also emphasized the role of cybersecurity in digital transformation.

Image: Employees Participating in a cybersecurity training session
5. Establish Incident Response Plans
Having a well-defined incident response plan is crucial for minimizing damage during a cybersecurity incident. This plan should outline the steps to take when a breach occurs, including communication protocols and recovery procedures. After experiencing a minor data breach, we realized the importance of having a clear plan in place. Our incident response plan enabled us to act quickly, minimizing downtime and protecting our reputation.
6. Monitor Systems Continuously
Continuous monitoring of your systems is essential for identifying potential threats in real time. Implementing advanced security tools that provide alerts for suspicious activities can help organizations respond swiftly to incidents. We invested in a Security Information and Event Management (SIEM) system that allowed us to monitor network traffic and detect anomalies proactively.
7. Collaborate with Third-Party Vendors Carefully
Many organizations rely on third-party vendors for various services, which can introduce additional risks. It’s crucial to assess the security practices of these vendors before partnering with them. We established a vendor assessment process that evaluates their security measures and compliance with industry standards. This diligence ensures that our partners align with our commitment to the role of cybersecurity in digital transformation.
Implementing best practices for securing digital initiatives is vital for any organization undergoing digital transformation. By conducting regular risk assessments, adopting secure-by-design principles, strengthening authentication measures, training employees, establishing incident response plans, monitoring systems continuously, and collaborating carefully with vendors, businesses can create a robust cybersecurity framework.
Fostering a Culture of Cybersecurity: Enhancing the Role of Cybersecurity in Digital Transformation?
Creating a culture of cybersecurity within an organization is essential for ensuring the success of digital transformation initiatives. A strong cybersecurity culture empowers employees to recognize and respond to threats while prioritizing security in their daily activities. Understanding the role of cybersecurity in digital transformation is key to fostering this culture.
1. Leadership Commitment
The first step in fostering a culture of cybersecurity is securing commitment from leadership. When executives prioritize cybersecurity, it sends a clear message to the entire organization about its importance. In my experience, we made cybersecurity a regular topic in our executive meetings. This commitment not only highlighted its significance but also ensured that resources were allocated for training and security initiatives.
2. Comprehensive Training Programs
Training employees on cybersecurity best practices is vital for building awareness and skills. Organizations should implement comprehensive training programs that cover topics such as phishing prevention, password management, and data protection. We adopted a blended learning approach that included online courses and hands-on workshops. This engaging format helped reinforce the importance of cybersecurity in digital change and ensured that employees felt equipped to handle potential threats.
3. Encourage Open Communication
Encouraging open communication about cybersecurity issues fosters a sense of shared responsibility among employees. Create channels where team members can report suspicious activities without fear of repercussions. When we established an anonymous reporting system, we noticed an increase in reported incidents, allowing us to address potential threats more swiftly. This transparency reinforces the role of cybersecurity in digital transformation, as everyone feels invested in protecting the organization.
4. Recognize and Reward Good Practices
Recognizing and rewarding employees who demonstrate good cybersecurity practices can motivate others to follow suit. Consider implementing a recognition program that highlights individuals or teams who contribute to enhancing security. In our organization, we introduced monthly awards for employees who reported phishing attempts or completed training modules. This initiative not only boosted morale but also reinforced the importance of cybersecurity across the board.
5. Integrate Cybersecurity into Daily Operations
To foster a culture of cybersecurity, organizations must integrate security practices into daily operations. This means making security considerations part of every project and decision-making process. For example, during our project planning sessions, we now include discussions about potential security implications and necessary safeguards. This proactive approach ensures that cybersecurity in digital change becomes second nature to all team members.
6. Provide Resources and Tools
Equipping employees with the right resources and tools is essential for maintaining a strong cybersecurity posture. Ensure that staff have access to updated software, secure communication channels, and guidelines for safe online behavior. We implemented tools like password managers and secure file-sharing services to help our team manage sensitive information securely.
7. Foster Continuous Learning
Cyber threats are constantly evolving, making continuous learning essential for maintaining a strong security culture. Encourage employees to stay informed about the latest trends and threats through ongoing training and professional development opportunities. We established a monthly newsletter that shares updates on emerging threats and best practices, keeping everyone engaged and informed about the role of cybersecurity in digital transformation.
Fostering a culture of cybersecurity is crucial for organizations undergoing digital transformation. By securing leadership commitment, providing comprehensive training, encouraging open communication, recognizing good practices, integrating security into daily operations, providing resources, and promoting continuous learning, businesses can create an environment where cybersecurity thrives.
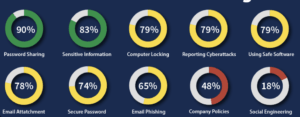
Image: Employee Cybersecurity Awareness benchmarking.
What Technologies Enhance Cybersecurity in Digital Transformation?
As organizations embrace digital transformation, leveraging the right technologies is crucial for enhancing cybersecurity. These technologies not only protect sensitive data but also support the overall goals of digital initiatives. Understanding the role of cybersecurity in digital transformation allows businesses to choose the best tools and practices to secure their environments effectively.
Image Placeholder 1: A visual representation of various cybersecurity technologies.
1. Artificial Intelligence and Machine Learning
Artificial intelligence (AI) and machine learning (ML) are transforming the cybersecurity landscape. These technologies can analyze vast amounts of data to identify patterns and detect anomalies that may indicate a security threat. For instance, we implemented an AI-driven security platform that monitored our network traffic in real time.
This system significantly reduced our response times to potential threats and highlighted the importance of cybersecurity in digital change.AI can also automate routine security tasks, allowing IT teams to focus on more strategic initiatives. By leveraging AI, organizations can enhance their threat detection capabilities and improve overall security posture.
2. Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) solutions play a vital role in providing a comprehensive view of an organization’s security status. SIEM systems collect and analyze data from various sources, enabling organizations to detect, investigate, and respond to incidents effectively. In our organization, implementing a SIEM solution allowed us to centralize our security monitoring efforts.
With real-time alerts and detailed reports, we could quickly identify suspicious activities and take action before they escalated. This capability is essential for understanding the role of cybersecurity in digital transformation as it provides visibility into potential threats across the entire network.
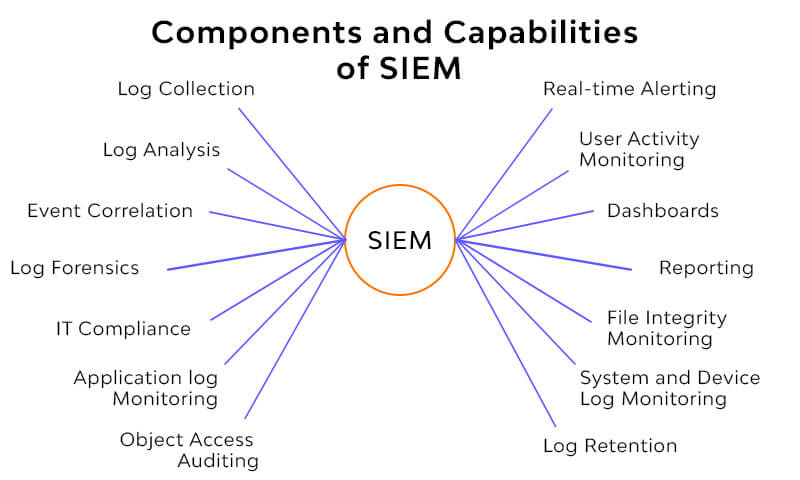
Image: Components and Capabilities of SIEM
3. Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of verification before accessing sensitive systems. This technology is particularly effective at preventing unauthorized access, even if passwords are compromised. We mandated MFA for all employees accessing critical applications, which greatly reduced our risk of data breaches.By implementing MFA, organizations can enhance their security measures significantly and reinforce the importance of cybersecurity in digital change.
4. Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) solutions focus on monitoring and securing endpoints—such as laptops, desktops, and mobile devices—against cyber threats. EDR tools provide real-time visibility into endpoint activities, allowing organizations to detect suspicious behavior quickly.In our company, adopting EDR technology helped us identify potential threats on employee devices before they could spread across the network. This proactive approach is crucial for maintaining a strong security posture during digital transformation efforts.
5. Cloud Security Solutions
As businesses increasingly migrate to cloud environments, robust cloud security solutions become essential. These solutions help protect data stored in the cloud from unauthorized access and breaches. We utilized cloud access security brokers (CASBs) to monitor user activities across our cloud applications.
By implementing these tools, we ensured that our cloud initiatives were secure while still benefiting from the flexibility and scalability that cloud services offer. This highlights the role of cybersecurity in digital transformation, especially as organizations adopt cloud technologies.
6. Data Encryption
Data encryption is a fundamental practice for protecting sensitive information both at rest and in transit. By encrypting data, organizations can ensure that even if it falls into the wrong hands, it remains unreadable without the proper decryption keys.
During our digital transformation journey, we prioritized data encryption across all platforms, reinforcing our commitment to safeguarding customer information. This practice not only protects data but also demonstrates a proactive approach to cybersecurity in digital change.
7. Threat Intelligence Platforms
Threat intelligence platforms provide organizations with valuable insights into emerging threats and vulnerabilities. By staying informed about the latest cyber threats, businesses can adapt their security strategies accordingly. We integrated a threat intelligence solution that aggregated data from various sources, helping us anticipate potential attacks before they occurred.This proactive approach is essential for understanding the role of cybersecurity in digital transformation, as it enables organizations to stay ahead of evolving threats.
Leveraging advanced technologies is critical for enhancing cybersecurity during digital transformation efforts. By implementing AI and ML solutions, SIEM systems, MFA, EDR tools, cloud security solutions, data encryption practices, and threat intelligence platforms, organizations can create a robust security framework that supports their digital initiatives.
How to Measure Success in Cybersecurity During Digital Transformation?
Measuring the success of cybersecurity efforts during digital transformation is essential for ensuring that your initiatives are effective and resilient. By establishing clear metrics and benchmarks, organizations can assess their cybersecurity posture and make informed decisions about future investments. Understanding the role of cybersecurity in digital transformation helps businesses create a framework for evaluating their security strategies.
1. Define Key Performance Indicators (KPIs)
The first step in measuring success is defining Key Performance Indicators (KPIs) that align with your organization’s goals. KPIs should focus on both the effectiveness of security measures and the overall impact on business operations. For example, we established KPIs such as the number of detected threats, incident response times, and employee training completion rates. These metrics provided a comprehensive view of our cybersecurity performance.By regularly reviewing these KPIs, organizations can understand how well they are managing risks associated with digital transformation and highlight the role of cybersecurity in digital transformation.
2. Conduct Regular Security Audits
Regular security audits are critical for assessing the effectiveness of your cybersecurity measures. These audits help identify vulnerabilities and gaps in your security framework. In our organization, we conducted annual audits that evaluated our systems against industry standards and best practices. This process not only highlighted areas for improvement but also reinforced our commitment to cybersecurity in digital change.
By addressing findings from these audits, organizations can enhance their security posture and ensure that they are effectively protecting their digital initiatives.
3. Track Incident Response Metrics
Tracking incident response metrics is essential for understanding how quickly and effectively your organization can respond to security incidents. Key metrics to monitor include the time taken to detect incidents, the time to contain them, and the overall recovery time. In our experience, we found that reducing our incident response time significantly improved our ability to mitigate threats.By continuously monitoring these metrics, organizations can evaluate the effectiveness of their incident response plans and highlight the role of cybersecurity in digital transformation.
4. Measure Employee Awareness and Engagement
Employee awareness is a critical component of any successful cybersecurity strategy. Measuring employee engagement through training completion rates and assessments can provide insights into how well your team understands security protocols. We implemented regular phishing simulations to test our employees’ awareness of potential threats.The results helped us identify areas where additional training was needed, reinforcing the importance of cybersecurity in digital change as employees became more vigilant against threats.
5. Assess Compliance with Regulations
Compliance with industry regulations is another important metric to monitor during digital transformation. Organizations should regularly assess their adherence to relevant data protection laws and standards. We established a compliance checklist that included GDPR, HIPAA, and other applicable regulations.By ensuring compliance, organizations not only protect sensitive data but also demonstrate their commitment to the role of cybersecurity in digital transformation.
6. Evaluate Third-Party Risk Management
As businesses increasingly rely on third-party vendors, assessing third-party risk management is crucial for measuring cybersecurity success. Organizations should evaluate the security practices of their vendors to ensure they align with their own standards. We developed a vendor assessment program that included security questionnaires and audits before partnering with any third party.This diligence helped us mitigate risks associated with third-party relationships and reinforced cybersecurity in digital change throughout our supply chain.
7. Analyze Threat Intelligence Data
Collecting and analyzing threat intelligence data can provide valuable insights into the effectiveness of your cybersecurity measures. By monitoring emerging threats and vulnerabilities, organizations can adapt their strategies accordingly. We integrated threat intelligence feeds into our security operations, allowing us to stay informed about potential risks.This proactive approach enabled us to adjust our defenses based on real-time data, underscoring the role of cybersecurity in digital transformation as we navigated an evolving threat landscape.
Measuring success in cybersecurity during digital transformation requires a multifaceted approach. By defining KPIs, conducting regular audits, tracking incident response metrics, measuring employee awareness, assessing compliance, evaluating third-party risk management, and analyzing threat intelligence data, organizations can gain valuable insights into their security posture.
What Are the Future Trends in Cybersecurity for Digital Transformation?
As digital transformation continues to evolve, so too does the landscape of cybersecurity. Organizations must stay ahead of emerging trends to effectively protect their digital initiatives. Understanding the role of cybersecurity in digital transformation is crucial for anticipating future challenges and opportunities. Here, we will explore some key trends that are shaping the future of cybersecurity.
Image Placeholder 1: A visual representation of future trends in cybersecurity.
1. Increased Use of Artificial Intelligence (AI)
Artificial intelligence (AI) is set to play a pivotal role in the future of cybersecurity. Organizations are increasingly leveraging AI and machine learning algorithms to enhance threat detection and response capabilities. These technologies can analyze vast amounts of data, identify patterns, and predict potential threats before they occur.
In our organization, we have started exploring AI-driven security solutions that automate routine tasks and provide real-time insights into network activities. This shift not only improves efficiency but also reinforces cybersecurity in digital change by allowing teams to focus on more strategic initiatives.
2. Zero Trust Architecture
The Zero Trust security model is gaining traction as organizations recognize the need for more robust security frameworks. This approach operates on the principle that no user or device should be trusted by default, regardless of whether they are inside or outside the network perimeter. Instead, continuous verification is required before granting access to sensitive resources.We began implementing a Zero Trust model by segmenting our network and requiring multi-factor authentication for all users. This proactive strategy helps mitigate risks associated with insider threats and external attacks, emphasizing the role of cybersecurity in digital transformation.
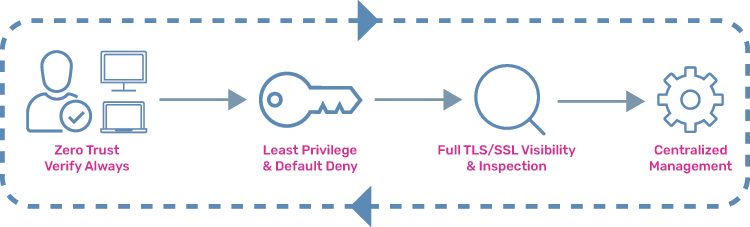
Image: The Zero Trust model
3. Enhanced Focus on Cloud Security
As more organizations migrate to cloud environments, the demand for advanced cloud security solutions will continue to grow. Businesses must ensure that their cloud services are protected against unauthorized access and data breaches. This includes implementing robust identity and access management (IAM) practices and utilizing encryption for data at rest and in transit.
In our transition to cloud-based applications, we prioritized cloud security by adopting a Cloud Access Security Broker (CASB) to monitor user activities and enforce security policies. This focus on cloud security underscores cybersecurity in digital change as organizations embrace flexible and scalable solutions.
4. Integration of DevSecOps
The integration of security into the DevOps process—known as DevSecOps—is becoming increasingly important as organizations strive for faster deployment cycles without sacrificing security. By embedding security practices within the development lifecycle, teams can identify vulnerabilities early and address them before they reach production.
We adopted a DevSecOps approach by involving our security team in planning and development phases. This collaboration ensures that security is prioritized throughout the process, reinforcing the role of cybersecurity in digital transformation.
5. Growing Importance of Cybersecurity Training
As cyber threats become more sophisticated, ongoing employee training will be critical for maintaining a strong security posture. Organizations must invest in regular training programs that keep employees informed about emerging threats and best practices.We have implemented a continuous learning program that includes simulations, workshops, and updates on current trends in cybersecurity. This commitment to employee education emphasizes cybersecurity in digital change as every team member becomes an active participant in protecting the organization.
6. Rise of Quantum Computing
While still in its infancy, quantum computing has the potential to revolutionize cybersecurity by offering unprecedented processing power. However, it also poses new risks, particularly regarding encryption methods currently used to protect sensitive data.Organizations must begin preparing for a future where quantum computing could break traditional encryption algorithms.
We are actively researching quantum-resistant encryption methods to ensure our data remains secure as technology evolves, highlighting the role of cybersecurity in digital transformation.
7. Increased Regulatory Scrutiny
As cyber threats continue to escalate, regulatory bodies are likely to impose stricter compliance requirements on organizations across various industries. Businesses must stay informed about evolving regulations related to data protection and privacy.In our organization, we have established a compliance team dedicated to monitoring regulatory changes and ensuring adherence to relevant laws. This proactive approach not only mitigates legal risks but also reinforces our commitment to cybersecurity in digital change.
Understanding future trends in cybersecurity is essential for organizations undergoing digital transformation. By embracing AI technologies, adopting Zero Trust architectures, focusing on cloud security, integrating DevSecOps practices, prioritizing employee training, preparing for quantum computing challenges, and staying compliant with regulations, businesses can effectively navigate the evolving cybersecurity landscape.
As we conclude this comprehensive exploration of cybersecurity’s role in digital transformation, let’s summarize key takeaways and insights gained throughout this journey.
Conclusion: Embracing Cybersecurity as a Catalyst for Digital Success
In today’s rapidly evolving digital landscape, organizations must recognize that cybersecurity is not just an IT concern; it is a fundamental component of successful digital transformation. As we have explored throughout this article, the role of cybersecurity in digital transformation is multifaceted and critical for safeguarding assets, maintaining customer trust, and enabling innovation.
Key Takeaways
- Integration is Essential: Cybersecurity should be integrated into every stage of the digital transformation process. From planning and implementation to ongoing management, security must be a priority.
- Understanding Risks: Organizations must be aware of the risks associated with digital change, including expanded attack surfaces, data breaches, and insider threats. By understanding these risks, businesses can implement effective strategies to mitigate them.
- Best Practices Matter: Adopting best practices—such as conducting regular risk assessments, implementing secure-by-design principles, and providing employee training—can significantly enhance an organization’s security posture.
- Fostering a Security Culture: Building a culture of cybersecurity within the organization is crucial. Leadership commitment, open communication, and recognition of good practices help create an environment where security is a shared responsibility.
- Leveraging Technology: Embracing advanced technologies like AI, SIEM systems, MFA, and cloud security solutions enhances an organization’s ability to detect and respond to threats effectively.
- Measuring Success: Establishing clear metrics and KPIs allows organizations to assess their cybersecurity efforts continuously. Regular audits and employee engagement assessments provide valuable insights into performance.
- Staying Ahead of Trends: As the cybersecurity landscape evolves, organizations must stay informed about emerging trends such as Zero Trust architecture, DevSecOps integration, and quantum computing challenges.
Looking Ahead
As we move forward in this digital age, organizations that prioritize cybersecurity will not only protect their assets but also unlock new opportunities for growth and innovation. By embracing cybersecurity in digital change, businesses can navigate the complexities of digital transformation with confidence.In conclusion, cybersecurity should be viewed as a catalyst for success rather than a barrier to progress. By integrating robust security measures into their digital initiatives, organizations can create a secure foundation that supports their long-term goals.

Image: A secure CyberSecurity Future.
FAQ Section
1. What is the role of cybersecurity in digital transformation?
The role of cybersecurity in digital transformation is to protect sensitive data and systems as organizations adopt new technologies. It ensures that digital initiatives are secure, safeguarding against cyber threats that can compromise operations and customer trust.
2. How can businesses mitigate risks during digital change?
Businesses can mitigate risks during digital change by conducting regular risk assessments, implementing strong security measures (like multi-factor authentication and encryption), and fostering employee awareness through comprehensive training programs. Understanding cybersecurity in digital change is essential for developing effective strategies.
3. What are common cybersecurity threats faced during digital transformation?
Common cybersecurity threats faced during digital transformation include:
- Phishing Attacks: Attempts to trick employees into revealing sensitive information.
- Ransomware: Malicious software that encrypts data and demands payment for its release.
- Data Breaches: Unauthorized access to sensitive data, leading to potential financial and reputational damage.
- Insider Threats: Risks from employees who may intentionally or unintentionally compromise security.
4. Why is a secure-by-design approach important?
A secure-by-design approach is important because it integrates security measures from the outset of any project. This proactive strategy reduces vulnerabilities and ensures that security is a fundamental component of the development process, reinforcing the role of cybersecurity in digital transformation.
5. How can organizations train employees on cybersecurity best practices?
Organizations can train employees on cybersecurity best practices through:
- Comprehensive Training Programs: Offering workshops, online courses, and hands-on simulations.
- Regular Updates: Keeping staff informed about emerging threats and best practices.
- Phishing Simulations: Testing employees’ ability to recognize phishing attempts and reinforcing awareness.
6. What technologies are essential for enhancing cybersecurity?
Essential technologies for enhancing cybersecurity include:
- Artificial Intelligence (AI): For threat detection and response automation.
- Security Information and Event Management (SIEM): For centralized monitoring of security events.
- Multi-Factor Authentication (MFA): To add an extra layer of security for user access.
- Endpoint Detection and Response (EDR): To monitor and secure endpoints against threats.
- Cloud Security Solutions: To protect data stored in cloud environments.
7. How do you measure the effectiveness of cybersecurity strategies?
The effectiveness of cybersecurity strategies can be measured by:
- Defining Key Performance Indicators (KPIs) related to security performance.
- Conducting regular security audits to identify vulnerabilities.
- Tracking incident response metrics like detection and recovery times.
- Assessing employee awareness through training completion rates and engagement.
8. What future trends should organizations be aware of regarding cybersecurity?
Organizations should be aware of several future trends in cybersecurity, including:
- Increased use of AI for threat detection and response.
- Adoption of Zero Trust architecture to enhance security protocols.
- Greater focus on cloud security as more businesses migrate to cloud environments.
- Integration of DevSecOps practices to embed security into the development lifecycle.
- The potential impact of quantum computing on encryption methods.
9. How does cloud computing affect cybersecurity during digital transformation?
Cloud computing affects cybersecurity by introducing new vulnerabilities that require robust security measures. Organizations must ensure that their cloud services are protected against unauthorized access, data breaches, and compliance issues, highlighting the importance of the role of cybersecurity in digital transformation.
10. What steps should be taken to ensure third-party vendors are secure?
To ensure third-party vendors are secure, organizations should:
- Conduct thorough assessments of vendors’ security practices before entering partnerships.
- Implement a vendor risk management program that includes regular audits and compliance checks.
- Ensure that vendors adhere to the same cybersecurity standards as the organization, reinforcing overall security efforts.



