Introduction
In today’s interconnected business landscape, the reliance on third-party vendors is more prevalent than ever. While these partnerships can drive innovation and efficiency, they also introduce significant risks that can jeopardize your organization’s security and reputation. This is where the importance of monitoring and managing third-party vendors comes into play.
Have you ever considered how a vendor’s failure could impact your business? Imagine this: a trusted supplier experiences a data breach, exposing sensitive customer information. Suddenly, your company faces not only financial losses but also damage to its reputation.
This scenario is all too common in today’s digital age, underscoring the need for robust vendor risk management strategies.In my early entrepreneurial days, I underestimated the risks associated with third-party vendors. I thought that as long as contracts were in place, everything would be fine.
However, my experience taught me that effective vendor management goes far beyond paperwork. It requires ongoing vigilance, clear communication, and proactive measures to mitigate risks. This blog post will explore the critical aspects of vendor risk management, including how to identify risks, implement effective strategies, and leverage technology for better oversight.
We’ll discuss the importance of building strong relationships with vendors and understanding regulatory considerations that affect your business. By the end of this article, you’ll have a comprehensive understanding of how to effectively monitor and manage third-party vendors, ensuring that your organization remains secure and resilient in an ever-changing environment.
Let’s dive in and discover how to turn potential weaknesses into strengths through effective vendor risk management.
What Is Vendor Risk Management?
Vendor risk management is a crucial part of any business strategy today. It involves identifying, assessing, and mitigating risks that come from working with third-party vendors. In my experience, managing these relationships effectively can make or break a company. When I first started my business, I didn’t pay enough attention to this area. I learned the hard way that neglecting vendor risk can lead to significant issues down the line.
When we talk about monitoring and managing third-party vendors, we’re really discussing how to keep our businesses safe. Every vendor relationship carries some level of risk. This could be financial instability, compliance failures, or even cybersecurity threats. For instance, I once partnered with a vendor who seemed reliable at first.
However, they faced a data breach that compromised customer information. This incident taught me the importance of thorough vendor risk management. The primary goal of vendor risk management is to protect your business from potential threats. It’s about ensuring that your vendors meet certain standards and that their practices align with your company’s values and requirements. By actively monitoring and managing third-party vendors, you can reduce the likelihood of disruptions and maintain a strong reputation.
Key Components of Vendor Risk Management
- Risk Identification: The first step is to identify what risks your vendors might pose. This includes evaluating their financial health, operational capabilities, and compliance with regulations. For example, if a vendor has a history of financial instability, this could be a red flag.
- Risk Assessment: After identifying potential risks, the next step is assessing their impact on your business. This is where third-party security assessments come into play. These assessments help you understand how vulnerable your business might be if something goes wrong with a vendor.
- Risk Mitigation: Once you’ve assessed the risks, it’s time to develop strategies to mitigate them. This could involve setting up clear contracts that outline expectations or implementing regular check-ins to monitor vendor performance.
- Continuous Monitoring: The world of business is always changing, and so are the risks associated with vendors. Regularly revisiting your vendor relationships is key to effective monitoring and managing third-party vendors.
Why Is Vendor Risk Management Important?
The importance of vendor risk management cannot be overstated. A single weak link in your supply chain can lead to significant losses—both financially and in terms of reputation. For instance, if a vendor fails to comply with industry regulations, your company could face legal repercussions.
In my early days as an entrepreneur, I underestimated this aspect of my business. I thought that as long as I had contracts in place, everything would be fine. However, when one vendor experienced a cyberattack, it not only affected their operations but also ours. We lost customers and faced backlash on social media.
By implementing robust vendor risk management practices, you can avoid such pitfalls. It builds trust with your customers and partners by showing that you take security seriously.
In summary, understanding what vendor risk management entails is essential for any business today. By focusing on monitoring and managing third-party vendors, you can safeguard your organization against potential threats and ensure long-term success.
Why Are Your Vendors a Weak Link?
When we think about the vulnerabilities in our businesses, we often focus on internal processes. However, one of the most significant weak links can actually be our vendors. Understanding why monitoring and managing third-party vendors is essential begins with recognizing the common vulnerabilities that exist within vendor relationships.
Common Vulnerabilities in Vendor Relationships
- Lack of Transparency: Many vendors may not fully disclose their practices, especially regarding security protocols. This lack of transparency can leave your business exposed to risks. For example, I once worked with a vendor who didn’t share their data protection policies. Later, I discovered they were not compliant with industry standards, which put my customer data at risk.
- Financial Instability: A vendor’s financial health directly impacts your business. If a vendor is struggling financially, they may cut corners or reduce service quality. I’ve seen companies lose critical services because their vendors declared bankruptcy unexpectedly. Regular financial assessments can help you gauge a vendor’s stability.
- Operational Risks: Vendors often have their own operational challenges that can affect your business. This could include staffing issues or supply chain disruptions. For instance, during the pandemic, many vendors faced delays due to workforce shortages or shipping issues. This highlighted the importance of having backup plans in place.
- Cybersecurity Threats: Cyberattacks are on the rise, and vendors can be prime targets. If a vendor gets hacked, it can lead to data breaches that affect your organization too. I learned this firsthand when a trusted vendor suffered a cyberattack, exposing sensitive information about my customers. This incident reinforced my commitment to monitoring and managing third-party vendors closely.
Statistics Highlighting Vendor Risks
The statistics surrounding vendor-related risks are alarming. According to a study by Ponemon Institute, 59% of organizations experienced a data breach caused by a third-party vendor in the past year. This statistic emphasizes the need for effective vendor risk management strategies.
Moreover, Gartner reports that by 2025, 70% of organizations will be unable to effectively manage third-party risk without implementing advanced technologies for monitoring and assessment. This shows that as our reliance on vendors increases, so does the necessity for robust risk management practices.
The Ripple Effect of Vendor Weakness
The impact of a weak vendor relationship goes beyond immediate losses. It can damage your brand reputation and customer trust. If customers learn that you’re working with unreliable vendors, they might question your judgment and commitment to quality.
For example, when my business faced backlash due to a vendor’s failure to meet compliance standards, it took months to regain customer trust. I realized then how crucial it is to vet vendors thoroughly and maintain ongoing assessments.
Understanding why your vendors can be a weak link is vital for any business looking to thrive in today’s competitive landscape. By recognizing common vulnerabilities and actively monitoring and managing third-party vendors, you can protect your organization from potential threats and ensure long-term success.
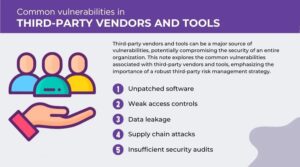
Image: Common vulnerabilities in Third party vendors and tools
How to Identify Risks in Vendor Relationships
Identifying risks in vendor relationships is a critical step in monitoring and managing third-party vendors effectively. Without a clear understanding of potential threats, businesses can find themselves vulnerable to unexpected challenges. In this section, we’ll explore how to pinpoint these risks and the essential factors to consider.
What Are the Key Risks Associated with Third-Party Vendors?
- Financial Risks: One of the most significant risks is financial instability. If a vendor is facing economic difficulties, it could impact their ability to deliver services or products. I learned this lesson when a key supplier suddenly raised prices due to financial strain, squeezing our budget unexpectedly. Regular financial assessments can help you stay ahead of these issues.
- Operational Risks: Vendors may have their own operational challenges that can affect your business. This includes issues like staffing shortages, supply chain disruptions, or even natural disasters. For instance, during a recent hurricane season, one of my vendors faced significant delays due to flooding. This taught me the importance of having contingency plans in place.
- Compliance Risks: Compliance with industry regulations is crucial. If a vendor fails to meet these standards, your organization could face legal repercussions. I once partnered with a vendor who didn’t comply with data protection laws. When regulators came knocking, it was my company that faced the consequences. Conducting thorough compliance checks during the onboarding process can help mitigate this risk.
- Cybersecurity Risks: Cybersecurity threats are more prevalent than ever, and vendors can be easy targets for hackers. A breach at a vendor can lead to data leaks affecting your organization as well. I experienced this firsthand when a trusted vendor suffered a cyberattack, exposing sensitive customer data linked to my business. This incident underscored the need for rigorous third-party security assessments.
The Role of Third-Party Security Assessments
Conducting third-party security assessments is vital for identifying risks in vendor relationships. These assessments involve evaluating a vendor’s security posture and practices to ensure they align with your organization’s standards.
- Initial Assessment Criteria: When onboarding a new vendor, it’s essential to establish clear criteria for evaluation. This includes reviewing their security policies, compliance certifications, and incident response plans. I always ask potential vendors for documentation that proves their commitment to security.
- Ongoing Evaluation Methods: Risk assessment isn’t a one-time task; it should be continuous. Regularly scheduled assessments can help you identify new risks as they arise. For example, I set up quarterly reviews with my vendors to discuss any changes in their operations or security measures.
- Reporting and Remediation Strategies: After conducting assessments, it’s crucial to have a clear reporting structure in place. If risks are identified, there should be established remediation strategies that outline how issues will be addressed promptly.
Building Strong Relationships for Better Risk Identification
Open communication with your vendors is essential for effective risk identification. Building strong relationships allows for transparent discussions about potential vulnerabilities. For instance, I make it a point to have regular check-ins with my vendors beyond formal assessments. These conversations often reveal insights that formal reports might miss—like upcoming changes in their operations or potential challenges they foresee.
Identifying risks in vendor relationships is an ongoing process that requires diligence and proactive measures. By focusing on financial stability, operational capabilities, compliance adherence, and cybersecurity practices while implementing effective third-party security assessments, you can significantly enhance your ability to monitor and manage third-party vendors effectively.

Image: Five Best Practices for Effective Vendor Risk Management
What Are Effective Strategies for Monitoring and Managing Third-Party Vendors?
Effective strategies for monitoring and managing third-party vendors are essential to safeguarding your business. By implementing structured processes, you can minimize risks and ensure that your vendors meet your standards. Here are some key strategies I’ve found invaluable in my experience.
1. Establish Clear Vendor Contracts and Guidelines
The foundation of a successful vendor relationship lies in clear contracts. These documents should outline expectations, responsibilities, and compliance requirements. When I first started working with vendors, I often relied on generic contracts. However, I quickly learned that specific terms tailored to each vendor’s role can prevent misunderstandings.
For example, include clauses that specify security protocols and data handling procedures. This not only sets clear expectations but also provides a framework for accountability. If a vendor fails to meet these standards, you have documented evidence to address the issue.
2. Implement Continuous Risk Monitoring
Once you have established contracts, continuous risk monitoring is crucial. This involves regularly reviewing vendor performance and compliance with agreed-upon standards. I recommend setting up a schedule for these evaluations—quarterly or bi-annually works well.
During these reviews, assess key performance indicators (KPIs) that matter most to your business. This could include delivery times, quality of service, and adherence to security protocols. By keeping a close eye on these metrics, you can identify potential issues before they escalate.
3. Conduct Regular Security Assessments
Regular third-party security assessments are vital for identifying vulnerabilities in vendor relationships. These assessments should be comprehensive and cover various aspects of security practices.
- Initial Assessment: When onboarding a new vendor, conduct a thorough security assessment to evaluate their current practices. This should include reviewing their cybersecurity policies, incident response plans, and past breach history.
- Ongoing Evaluations: After the initial assessment, schedule regular follow-ups to ensure that the vendor maintains high-security standards. For instance, I conduct annual security audits with my critical vendors to ensure compliance with evolving regulations.
- Documentation: Keep detailed records of all assessments and findings. This documentation not only helps in tracking improvements but also serves as evidence if any disputes arise.
4. Foster Open Communication
Building strong relationships with your vendors is essential for effective monitoring and managing third-party vendors. Open communication fosters transparency and trust. I make it a point to have regular check-ins with my vendors beyond formal assessments.
These conversations often reveal insights that formal reports might miss—like upcoming changes in their operations or potential challenges they foresee. Encourage vendors to share any concerns or changes in their operations that could impact your business. This proactive approach can help you address issues before they become significant problems.
5. Develop Incident Response Plans
Despite your best efforts, issues may still arise with vendors. Having an incident response plan in place is crucial for minimizing damage when things go wrong.
- Define Roles and Responsibilities: Clearly outline who is responsible for what during an incident involving a vendor breach or failure.
- Communication Protocols: Establish how information will be communicated between your organization and the vendor during an incident.
- Remediation Steps: Develop a step-by-step process for addressing incidents as they occur, including timelines for resolution and follow-up actions.
Effective strategies for monitoring and managing third-party vendors are critical for maintaining the integrity of your business operations. By establishing clear contracts, implementing continuous risk monitoring, conducting regular security assessments, fostering open communication, and developing incident response plans, you can significantly reduce risks associated with vendor relationships.
How Can Technology Enhance Vendor Risk Management?
In today’s fast-paced business environment, leveraging technology is essential for effective monitoring and managing third-party vendors. Technology not only streamlines processes but also enhances the accuracy of risk assessments and improves communication. Here’s how you can use technology to strengthen your vendor risk management practices.
1. Automated Risk Assessments
One of the most significant advantages of technology is the ability to automate risk assessments. Automated tools can help you evaluate vendors quickly and efficiently, allowing you to focus on more strategic tasks. For instance, I implemented a software solution that automatically collects data from vendors and assesses their compliance with security standards.
These tools often come with built-in templates for third-party security assessments, making it easier to ensure that all necessary criteria are evaluated. By automating these processes, you can significantly reduce the time spent on manual assessments while enhancing the accuracy of your evaluations.
2. Continuous Monitoring Solutions
Continuous monitoring is vital for monitoring and managing third-party vendors effectively. Technology enables real-time tracking of vendor performance and compliance. For example, I use a monitoring platform that alerts me to any changes in a vendor’s financial status or compliance standing.
These platforms can track various metrics, such as delivery times, service quality, and even customer feedback. By having access to this data in real-time, you can quickly identify potential issues and address them before they escalate into significant problems.
3. Centralized Vendor Management Systems
A centralized vendor management system (VMS) can be a game-changer for your organization. These systems allow you to manage all vendor-related information in one place, making it easier to track performance and compliance. I found that using a VMS helped streamline my vendor management processes significantly.
With a VMS, you can store contracts, assessment reports, and communication history for each vendor. This centralization not only enhances organization but also ensures that everyone in your team has access to the same information, which is crucial for effective monitoring and managing third-party vendors.
4. Enhanced Communication Tools
Effective communication is key when it comes to monitoring and managing third-party vendors. Technology offers various tools that facilitate better communication between your organization and its vendors. For instance, I use project management software that allows for real-time updates and discussions with my vendors.
These tools enable you to share documents, track progress on projects, and address concerns quickly. By fostering open lines of communication, you can build stronger relationships with your vendors and ensure that any issues are resolved promptly.
5. Data Analytics for Informed Decision-Making
Data analytics plays a crucial role in enhancing vendor risk management strategies. By analyzing data collected from various sources, you can gain valuable insights into vendor performance and potential risks. For example, I regularly analyze trends in vendor delivery times or compliance rates to identify patterns that may indicate underlying issues.
Using data analytics tools allows you to make informed decisions about which vendors to retain or terminate based on their performance history. This proactive approach is essential for effective monitoring and managing third-party vendors.
Technology is a powerful ally in enhancing your vendor risk management practices. By automating risk assessments, implementing continuous monitoring solutions, utilizing centralized vendor management systems, enhancing communication tools, and leveraging data analytics, you can significantly improve your ability to monitor and manage third-party vendors effectively.
Embracing these technological advancements will not only streamline your processes but also strengthen your overall business resilience.
What Should Be Included in a Vendor Risk Management Plan?
Creating a robust vendor risk management plan is essential for monitoring and managing third-party vendors effectively. A well-structured plan not only outlines your approach to vendor management but also helps you mitigate risks proactively. Here’s what should be included in your vendor risk management plan.
1. Due Diligence Processes
The first step in any effective vendor risk management plan is establishing thorough due diligence processes. This involves gathering information about potential vendors before entering into contracts. For instance, I always conduct background checks and review financial statements to assess a vendor’s stability. Your due diligence should include:
- Financial Assessments: Evaluate the financial health of the vendor to ensure they can meet their obligations.
- Compliance Checks: Confirm that the vendor adheres to relevant regulations and industry standards.
- Reputation Analysis: Research the vendor’s reputation by looking at customer reviews and past performance.
By implementing these due diligence processes, you can significantly reduce risks associated with new vendors.
2. Risk Assessment Protocols
Once you’ve selected a vendor, it’s crucial to have clear risk assessment protocols in place. This will guide how you evaluate and monitor vendors throughout your relationship. In my experience, having a structured approach makes it easier to identify and address potential issues. Your risk assessment protocols should include:
- Initial Risk Assessment: Conduct a comprehensive assessment of the vendor’s operations, security measures, and compliance status before onboarding.
- Ongoing Risk Evaluations: Schedule regular assessments to monitor changes in the vendor’s risk profile. I recommend conducting these evaluations at least annually or whenever significant changes occur.
By establishing these protocols, you can ensure that you are consistently monitoring and managing third-party vendors effectively.
3. Incident Response Plans
No matter how thorough your vendor risk management plan is, incidents can still occur. Therefore, having an incident response plan is vital for minimizing damage when issues arise. This plan should outline how your organization will respond to incidents involving vendors. Key components of an incident response plan include:
- Roles and Responsibilities: Clearly define who is responsible for managing incidents related to vendors.
- Communication Protocols: Establish how information will be communicated between your organization and the vendor during an incident.
- Remediation Steps: Outline the steps that need to be taken to resolve the issue and prevent future occurrences.
In my experience, having a well-documented incident response plan has made it easier to manage crises effectively when they arise.
4. Performance Metrics
To ensure that you are effectively monitoring and managing third-party vendors, it’s essential to establish performance metrics. These metrics will help you evaluate how well your vendors are meeting their obligations. Consider including the following performance metrics in your plan:
- Service Level Agreements (SLAs): Define specific performance targets that vendors must meet, such as delivery times or quality standards.
- Compliance Rates: Track how often vendors adhere to regulatory requirements.
- Customer Feedback: Gather feedback from internal teams or customers regarding their experiences with the vendor.
By regularly reviewing these metrics, you can identify trends and make informed decisions about whether to continue working with a particular vendor.
5. Review and Update Procedures
Finally, your vendor risk management plan should include procedures for regular reviews and updates. The business landscape is constantly changing, and so are the risks associated with vendors. I recommend scheduling annual reviews of your entire vendor risk management plan to ensure it remains relevant. During these reviews, consider:
- Assessing New Risks: Identify any new risks that may have emerged since the last review.
- Updating Policies: Revise policies based on lessons learned from past incidents or changes in regulations.
- Training Staff: Ensure that all relevant staff members are trained on updated procedures and best practices for monitoring and managing third-party vendors.
A comprehensive vendor risk management plan is crucial for effectively monitoring and managing third-party vendors. By including due diligence processes, risk assessment protocols, incident response plans, performance metrics, and review procedures, you can create a robust framework that protects your organization from potential threats while fostering strong relationships with your vendors.
How to Conduct Third-Party Security Assessments
Conducting third-party security assessments is a critical component of monitoring and managing third-party vendors effectively. These assessments help you evaluate the security posture of your vendors and identify potential vulnerabilities that could impact your organization. Here’s a step-by-step guide on how to conduct these assessments successfully.
1. Define Assessment Objectives
Before diving into the assessment process, it’s essential to define your objectives clearly. What do you want to achieve with the assessment? In my experience, having well-defined goals can guide the entire process and ensure that you focus on the most critical areas. Consider objectives such as:
- Evaluating the vendor’s compliance with security standards.
- Identifying potential vulnerabilities in their systems.
- Understanding their incident response capabilities.
By setting clear objectives, you can tailor your assessment to meet your organization’s specific needs.
2. Initial Assessment Criteria
The initial assessment is crucial for gaining a comprehensive understanding of a vendor’s security practices. When I first assess a vendor, I look at several key areas:
- Security Policies: Review the vendor’s security policies and procedures to ensure they align with industry standards.
- Compliance Certifications: Check for relevant certifications, such as ISO 27001 or SOC 2, which demonstrate the vendor’s commitment to security.
- Past Breaches: Investigate any history of data breaches or security incidents. Understanding their past responses can provide insight into their current practices.
By focusing on these criteria, you can gauge whether the vendor meets your security requirements.
3. Ongoing Evaluation Methods
Once a vendor is onboarded, ongoing evaluations are essential for maintaining effective monitoring and managing third-party vendors. Regular assessments help you stay informed about any changes in the vendor’s security posture. Consider implementing the following ongoing evaluation methods:
- Regular Security Audits: Schedule annual or semi-annual audits to review the vendor’s security practices and compliance status.
- Vulnerability Scanning: Utilize automated tools to conduct regular vulnerability scans of the vendor’s systems. This can help identify weaknesses before they become significant issues.
- Performance Reviews: Incorporate security metrics into your regular performance reviews. This ensures that security remains a priority throughout the vendor relationship.
By consistently evaluating vendors, you can quickly identify any emerging risks and take appropriate action.
4. Reporting and Remediation Strategies
After conducting assessments, it’s crucial to have a structured reporting process in place. This ensures that findings are communicated effectively and that remediation strategies are implemented promptly.
- Assessment Reports: Create detailed reports summarizing the findings from each assessment. Include actionable recommendations for improvement.
- Communication with Vendors: Share assessment results with vendors and discuss any identified issues. Collaborate on developing remediation plans to address these vulnerabilities.
- Follow-Up Assessments: Schedule follow-up assessments to verify that remediation efforts have been implemented effectively. This step is vital for ensuring continuous improvement in vendor security practices.
In my experience, transparent communication with vendors about assessment findings fosters collaboration and accountability.
5. Documenting Findings
Documentation is key when it comes to third-party security assessments. Keep detailed records of all assessments, findings, and remediation efforts. This documentation serves multiple purposes:
- Compliance Evidence: It provides evidence of due diligence in case of regulatory inquiries or audits.
- Historical Reference: It allows you to track changes in vendor performance over time.
- Continuous Improvement: Reviewing past assessments helps identify trends and areas for improvement in your own risk management processes.
I always emphasize the importance of thorough documentation in my vendor management practices, as it can save time and resources down the line.
Conducting effective third-party security assessments is essential for successfully monitoring and managing third-party vendors. By defining assessment objectives, establishing initial criteria, implementing ongoing evaluations, developing reporting strategies, and documenting findings, you can significantly enhance your organization’s ability to identify and mitigate risks associated with vendors.
How to Foster Strong Relationships with Vendors
Fostering strong relationships with vendors is crucial for effective monitoring and managing third-party vendors. A healthy partnership not only enhances collaboration but also helps mitigate risks and improve overall performance. Here are some strategies I’ve found effective in building and maintaining strong vendor relationships.
1. Open Communication Channels
One of the most important aspects of any relationship is communication. Establishing open lines of communication with your vendors can lead to better understanding and cooperation. In my experience, regular check-ins can make a significant difference.
- Scheduled Meetings: I recommend setting up regular meetings—monthly or quarterly—to discuss ongoing projects, performance metrics, and any concerns. This creates a platform for both parties to share insights and feedback.
- Feedback Loops: Encourage vendors to provide feedback on your processes as well. This two-way communication fosters a sense of partnership and helps identify areas for improvement on both sides.
By prioritizing open communication, you can build trust and ensure that both parties are aligned on goals and expectations.
2. Set Clear Expectations
Setting clear expectations from the outset is essential for effective monitoring and managing third-party vendors. When both parties know what is expected, it reduces the likelihood of misunderstandings.
- Define Roles and Responsibilities: Clearly outline what each party is responsible for in the relationship. This includes deliverables, timelines, and quality standards.
- Service Level Agreements (SLAs): Implement SLAs that specify performance metrics, response times, and compliance requirements. I’ve found that having these agreements in place helps hold vendors accountable.
By establishing clear expectations, you create a framework that guides the relationship and minimizes conflicts.
3. Invest in Relationship Building
Building a strong relationship takes time and effort. Investing in your vendor relationships can lead to long-term benefits for both parties.
- Social Interactions: Consider organizing informal gatherings or team-building activities. These interactions help humanize the relationship and strengthen bonds beyond business transactions.
- Recognition: Acknowledge your vendors’ achievements and contributions. Whether it’s through a simple thank-you note or public recognition, showing appreciation fosters goodwill.
In my experience, taking the time to invest in relationships pays off in terms of loyalty and commitment from vendors.
4. Collaborate on Problem-Solving
When issues arise, collaborating with your vendors to find solutions can strengthen your partnership. Instead of approaching problems as adversaries, work together to address challenges.
- Joint Problem-Solving Sessions: When a vendor faces a challenge that impacts your business, host joint problem-solving sessions. This collaborative approach often leads to innovative solutions that benefit both parties.
- Share Resources: If possible, share resources or information that could help the vendor overcome obstacles. This demonstrates your commitment to their success.
I’ve found that working together during tough times can turn challenges into opportunities for growth in the relationship.
5. Monitor Performance Together
Regularly monitoring vendor performance together can enhance accountability and transparency in the relationship.
- Joint Performance Reviews: Schedule joint performance reviews where both parties can assess how well they are meeting expectations outlined in SLAs. This creates an opportunity for constructive feedback.
- Set Improvement Goals: Collaboratively set goals for improvement based on performance reviews. This shared responsibility fosters a sense of partnership and commitment to success.
By involving vendors in the performance monitoring process, you create a collaborative environment where everyone is invested in achieving success.
Fostering strong relationships with vendors is essential for effective monitoring and managing third-party vendors. By prioritizing open communication, setting clear expectations, investing in relationship building, collaborating on problem-solving, and monitoring performance together, you can create partnerships that are not only productive but also resilient against potential risks.
Image: Effective Vendor management
What Are the Regulatory Considerations for Vendor Risk Management?
When it comes to monitoring and managing third-party vendors, understanding regulatory considerations is crucial. Compliance with industry regulations not only protects your organization but also helps maintain trust with customers and partners. Here’s a look at the key regulatory aspects you should consider in your vendor risk management strategy.
1. Understanding Relevant Regulations
Different industries have specific regulations that govern vendor relationships. Familiarizing yourself with these regulations is essential for effective vendor risk management.
- Data Protection Regulations: For organizations handling sensitive customer data, regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) impose strict requirements on data handling. I learned this firsthand when my company had to adapt our vendor contracts to comply with GDPR, ensuring that all vendors were also compliant.
- Financial Regulations: If you’re in the financial sector, regulations like the Gramm-Leach-Bliley Act (GLBA) require organizations to protect consumer information. This means that your vendors must also adhere to similar standards.
- Healthcare Regulations: For healthcare organizations, the Health Insurance Portability and Accountability Act (HIPAA) mandates strict compliance regarding patient data. When working with vendors in this space, it’s vital to ensure they understand and comply with HIPAA requirements.
By understanding these regulations, you can better assess the risks associated with your vendors and ensure compliance across your supply chain.
2. Due Diligence and Vendor Selection
Regulatory considerations should be integrated into your due diligence processes when selecting vendors. This means evaluating not just their capabilities but also their compliance status.
- Compliance Checks: During the vendor selection process, conduct thorough compliance checks to ensure that potential vendors meet relevant regulatory requirements. I always ask for documentation proving their compliance status, such as certifications or audit reports.
- Risk Assessment: Incorporate regulatory risks into your overall vendor risk assessment protocols. This includes evaluating how a vendor’s non-compliance could impact your organization.
By prioritizing compliance during the selection process, you can mitigate risks associated with working with non-compliant vendors.
3. Contractual Obligations
Your contracts with vendors should clearly outline their responsibilities regarding compliance with relevant regulations. This is a critical aspect of monitoring and managing third-party vendors effectively.
- Incorporate Compliance Clauses: Ensure that contracts include clauses that require vendors to comply with applicable laws and regulations. This creates a legal obligation for them to adhere to these standards.
- Audit Rights: Include provisions that grant your organization the right to audit the vendor’s compliance practices periodically. This ensures that you can verify their adherence to regulatory requirements.
In my experience, having well-defined contractual obligations helps hold vendors accountable for their compliance efforts.
4. Ongoing Monitoring and Reporting
Regulatory compliance is not a one-time effort; it requires ongoing monitoring and reporting. Establishing processes for continuous oversight is essential for effective vendor risk management.
- Regular Compliance Audits: Schedule regular audits of your vendors’ compliance practices to ensure they continue to meet regulatory requirements. I recommend conducting these audits at least annually or whenever significant changes occur in regulations or vendor operations.
- Reporting Mechanisms: Set up reporting mechanisms that require vendors to report any incidents of non-compliance promptly. This proactive approach allows you to address issues before they escalate into larger problems.
By implementing ongoing monitoring and reporting processes, you can maintain a strong focus on regulatory compliance in your vendor relationships.
5. Training and Awareness
Ensuring that both your team and your vendors are aware of regulatory requirements is crucial for effective monitoring and managing third-party vendors.
- Training Programs: Implement training programs for your internal staff on relevant regulations and best practices for vendor management. This ensures everyone understands their role in maintaining compliance.
- Vendor Education: Provide resources or training for your vendors on compliance expectations and best practices. Educating them can help prevent non-compliance issues from arising in the first place.
In my experience, fostering a culture of compliance within both your organization and among your vendors leads to better outcomes for everyone involved.
Understanding regulatory considerations is vital for effective monitoring and managing third-party vendors. By familiarizing yourself with relevant regulations, conducting thorough due diligence, incorporating compliance clauses into contracts, establishing ongoing monitoring processes, and promoting training and awareness, you can significantly enhance your organization’s ability to manage vendor risks while ensuring compliance across the board.

Image: Vendor Risk Management Best Practices
Strengthening Your Vendor Relationships for Better Security
In the ever-evolving landscape of business, strengthening your vendor relationships is not just beneficial; it’s essential for effective monitoring and managing third-party vendors. A strong partnership can lead to improved security, better compliance, and enhanced overall performance. Here are some strategies to fortify those relationships while ensuring that security remains a top priority.
1. Prioritize Mutual Goals
Establishing mutual goals with your vendors can create a sense of shared purpose. When both parties are aligned on objectives, it fosters collaboration and strengthens the relationship.
- Joint Security Initiatives: Consider launching joint initiatives focused on improving security practices. For instance, I collaborated with a key vendor to develop a shared cybersecurity training program for both teams. This not only improved our security posture but also built trust between our organizations.
- Performance Metrics: Set shared performance metrics that both parties are responsible for achieving. This encourages accountability and ensures that everyone is working toward the same outcomes.
By prioritizing mutual goals, you create a collaborative environment that enhances both security and partnership.
2. Foster Transparency
Transparency is crucial in building trust and ensuring effective monitoring and managing third-party vendors. When vendors feel comfortable sharing information, it leads to better decision-making and risk management.
- Open Dialogue: Encourage open dialogue about challenges and risks. For example, I always invite my vendors to share any concerns they may have about their operations or security practices. This openness allows us to address potential issues proactively.
- Information Sharing: Share relevant information about your organization’s security practices and policies with your vendors. This helps them understand your expectations and enables them to align their practices accordingly.
By fostering transparency, you create a culture of trust that benefits both parties.
3. Invest in Training and Development
Investing in training and development for both your team and your vendors can significantly enhance security practices. A well-informed team is better equipped to manage risks effectively.
- Vendor Training Programs: Offer training sessions for your vendors on best practices in cybersecurity and compliance. This not only strengthens their capabilities but also reinforces your commitment to security.
- Internal Training: Ensure that your internal teams are trained on vendor management best practices and the importance of security in vendor relationships. Regular workshops or seminars can keep everyone informed about the latest trends and regulations.
In my experience, investing in training fosters a culture of continuous improvement that benefits everyone involved.
4. Implement Regular Security Reviews
Regular security reviews are essential for maintaining strong vendor relationships while ensuring effective monitoring and managing third-party vendors. These reviews help identify vulnerabilities and areas for improvement.
- Joint Security Audits: Conduct joint security audits with your vendors to assess their practices and identify potential risks. This collaborative approach allows both parties to learn from each other’s experiences.
- Feedback Mechanisms: Establish feedback mechanisms where both parties can provide input on security practices. This creates an opportunity for constructive discussions about improvements.
By implementing regular security reviews, you can ensure that both you and your vendors remain vigilant against potential threats.
5. Celebrate Successes Together
Recognizing achievements can significantly strengthen vendor relationships. Celebrating successes fosters goodwill and encourages continued collaboration on security initiatives.
- Acknowledgment of Milestones: When a vendor meets or exceeds performance metrics, make sure to acknowledge their efforts publicly or privately. A simple thank-you note or recognition during meetings can go a long way in building rapport.
- Joint Celebrations: Consider hosting joint celebrations when significant milestones are achieved—whether it’s successful project completion or compliance certification. These events reinforce the partnership and create positive memories.
In my experience, celebrating successes together enhances motivation and strengthens the bond between organizations.
Strengthening your vendor relationships is essential for effective monitoring and managing third-party vendors while enhancing security practices. By prioritizing mutual goals, fostering transparency, investing in training, implementing regular security reviews, and celebrating successes together, you can build robust partnerships that not only protect your organization but also drive mutual success.
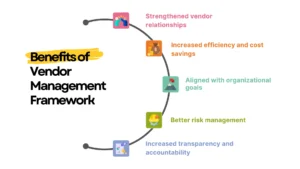
Image: Benefits of vendor management Framework.
FAQ Section
1. What is the primary goal of vendor risk management?
The primary goal of vendor risk management is to identify, assess, and mitigate risks associated with third-party vendors. This process ensures that vendors comply with regulatory requirements and meet your organization’s standards for security and performance. Effective vendor risk management helps protect your business from potential financial losses, reputational damage, and compliance issues.
2. How often should I conduct third-party security assessments?
You should conduct third-party security assessments at least annually. However, if a vendor undergoes significant changes—such as a merger, acquisition, or a major update to their systems—it’s wise to perform an assessment at that time. Additionally, regular assessments (quarterly or bi-annually) for critical vendors can help you stay ahead of emerging risks.
3. What tools are available for monitoring vendor performance?
There are various tools available for monitoring and managing third-party vendors effectively. Vendor management systems (VMS) can centralize information and track performance metrics. Additionally, automated risk assessment tools can help evaluate compliance and security posture. Some popular options include Coupa, Ariba, and RiskWatch.
4. How can I ensure my vendors comply with industry regulations?
To ensure vendor compliance with industry regulations, incorporate compliance checks into your due diligence processes during vendor selection. Include compliance clauses in contracts and conduct regular audits to verify adherence. Establish clear communication channels for reporting any compliance issues promptly.
5. What steps should I take if a vendor poses a significant risk?
If a vendor poses a significant risk, first assess the nature and extent of the risk. Engage in open communication with the vendor to discuss your concerns and explore remediation options. If necessary, develop an action plan that outlines steps for improvement or consider terminating the relationship if the risks cannot be mitigated.
6. How do I establish clear guidelines in vendor contracts?
To establish clear guidelines in vendor contracts, define roles and responsibilities explicitly. Include service level agreements (SLAs) that specify performance metrics and compliance requirements. Ensure that the contract outlines consequences for non-compliance or failure to meet expectations.
7. What are the common signs that a vendor may be a weak link?
Common signs that a vendor may be a weak link include inconsistent communication, frequent delays in service delivery, lack of transparency regarding their operations or financial status, and previous incidents of non-compliance or security breaches. Regular performance reviews can help identify these issues early on.
8. Can technology fully replace human oversight in vendor risk management?
While technology can significantly enhance monitoring and managing third-party vendors, it should not fully replace human oversight. Automated tools can streamline processes and provide valuable data insights, but human judgment is essential for interpreting results, making strategic decisions, and fostering relationships with vendors.
9. How do I educate my team about vendor risk management best practices?
Educating your team about vendor risk management best practices can be achieved through regular training sessions, workshops, and sharing resources on industry standards. Encourage team members to stay updated on regulations and trends by attending conferences or webinars related to vendor management.
10. What should I do if my vendor experiences a data breach?
If your vendor experiences a data breach, immediately communicate with them to understand the situation’s scope and impact on your organization. Follow your incident response plan to assess potential risks to your data and customer information. Work with the vendor to implement remediation strategies and keep stakeholders informed about the situation.