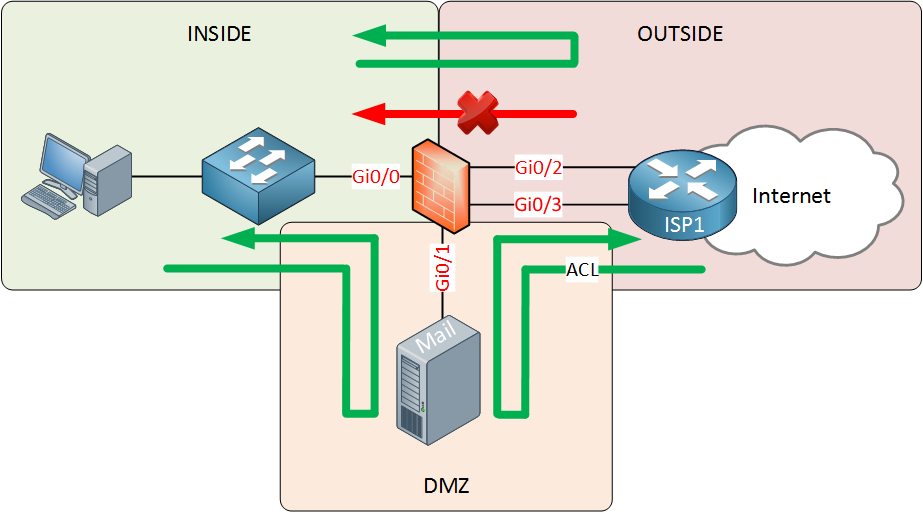
Introduction
In today’s digital age, safeguarding your business with firewalls has become more crucial than ever. Cybersecurity threats are constantly evolving, and businesses of all sizes face the risk of data breaches, ransomware attacks, and other malicious activities. This is where safeguarding your business with firewalls comes into play.

As an entrepreneur who has navigated these challenges firsthand, I can attest to the importance of having robust security measures in place. When I first started my online business, I underestimated the potential threats lurking in the digital landscape. It wasn’t until a close call with a phishing attack that I realized how vulnerable my data and customer information were. That experience pushed me to dive deep into the world of cybersecurity, particularly firewalls, which play a pivotal role in protecting networks.
Firewalls act as a barrier between your internal network and external threats. They monitor incoming and outgoing traffic and decide whether to allow or block specific traffic based on predetermined security rules. By implementing effective firewall security measures, you can significantly reduce the risk of unauthorized access and cyber attacks.
In this blog post, we will explore various aspects of firewalls, including how they work, the different types available, best practices for implementation, and their integration with other security measures. We’ll also discuss common limitations of firewalls and future trends in firewall technology. By the end of this article, you’ll have a comprehensive understanding of how firewalls can protect your business and why they are essential in today’s cybersecurity landscape.
As we delve deeper into this topic, remember that safeguarding your business with firewalls is not just about technology; it’s about creating a culture of security within your organization. Let’s get started by understanding what firewalls are and why they are essential for every business.
What Are Firewalls and Why Are They Essential?
Firewalls are like the security guards of your digital world. They serve as a protective barrier between your internal network and the outside internet, monitoring and controlling the traffic that flows in and out. When I first implemented a firewall for my business, I was amazed at how much peace of mind it provided. Understanding what firewalls are and why they are essential can help you appreciate their role in safeguarding your business with firewalls.
Definition of Firewalls
At its core, a firewall is a network security device that monitors and filters incoming and outgoing traffic based on established security rules. Think of it as a gatekeeper that decides who gets in and who stays out. Firewalls can be hardware-based, software-based, or a combination of both.
- Hardware Firewalls: These are standalone devices that connect to your network. They provide a robust layer of protection by filtering traffic before it reaches your internal systems.
- Software Firewalls: Installed on individual devices, software firewalls protect each computer or server on your network. They are particularly useful for smaller businesses or remote workers.
- Next-Generation Firewalls (NGFW): These advanced firewalls combine traditional firewall capabilities with additional features like intrusion prevention systems (IPS) and application awareness.
Importance of Firewalls
The importance of firewalls cannot be overstated. Here are some key reasons why they are essential for safeguarding your business with firewalls:
- Prevent Unauthorized Access: Firewalls block unauthorized users from accessing sensitive data and systems. This is crucial for protecting customer information, financial records, and proprietary data.
- Mitigate Cyber Threats: By monitoring traffic patterns, firewalls can identify and block potential threats such as malware, viruses, and denial-of-service attacks. During my early days in business, I experienced a DDoS attack that brought my website down for hours. Implementing a firewall afterward helped me mitigate similar threats in the future.
- Regulatory Compliance: Many industries have regulations that require businesses to implement specific security measures to protect customer data. Firewalls are often a key component of these compliance frameworks.
- Network Segmentation: Firewalls allow you to segment your network into different zones, which can help contain potential breaches. For example, if an attacker gains access to one part of your network, segmentation can prevent them from moving freely throughout your entire system.
Real-World Example
Let me share an experience from my own business journey. A few years ago, I was approached by a friend who ran a small e-commerce site. He had fallen victim to a cyber attack that compromised his customer database. After helping him recover, I emphasized the need for firewall security measures to protect his business going forward.
We set up a hardware firewall that not only blocked unwanted traffic but also monitored for suspicious activity in real-time. This proactive approach allowed him to focus on growing his business without constantly worrying about potential cyber threats.
Understanding what firewalls are and their importance is crucial for any business owner looking to protect their digital assets. By implementing effective firewall security measures, you can significantly enhance your organization’s cybersecurity posture. Remember, safeguarding your business with firewalls is not just about technology; it’s about creating a secure environment where you can thrive without fear of cyber attacks.
How Do Firewalls Work?
Understanding how firewalls work is essential for safeguarding your business with firewalls effectively. These security devices employ various methods to monitor and control network traffic, ensuring that only legitimate traffic is allowed while blocking potential threats. Let’s break down the core functionalities and mechanisms behind firewalls.
Core Functions of Firewalls
Firewalls operate primarily through two main functions: filtering and monitoring. Here’s how these functions work:
- Traffic Filtering: Firewalls analyze data packets that travel across your network. Each packet contains information such as the source IP address, destination IP address, and the type of data being sent. When a packet arrives, the firewall checks it against a set of predefined rules. If the packet meets the criteria (e.g., it comes from a trusted source), it is allowed through. If not, it’s blocked.
- Monitoring Traffic: Firewalls continuously monitor both incoming and outgoing traffic for unusual patterns or behaviors. This monitoring helps detect potential threats like malware or unauthorized access attempts. In my experience, having a firewall that actively monitors traffic has been invaluable in identifying and stopping attacks before they escalate.
Types of Filtering Techniques
Firewalls use various filtering techniques to enhance their effectiveness in safeguarding your business with firewalls:
- Packet Filtering: This is the most basic form of firewall protection. It examines packets at the network layer and allows or blocks them based on source/destination IP addresses and port numbers. While effective for simple filtering, it does not inspect the packet content.
- Stateful Inspection: A more advanced technique, stateful inspection keeps track of active connections and their states (e.g., established, closing). This means the firewall can make more informed decisions about whether to allow or block traffic based on its context.
- Application Layer Filtering: This method goes deeper by inspecting the actual data being transmitted. It analyzes application-level protocols (like HTTP or FTP) to identify malicious content or behaviors. For instance, if a user tries to download a file containing malware, an application-layer firewall can block that specific action.
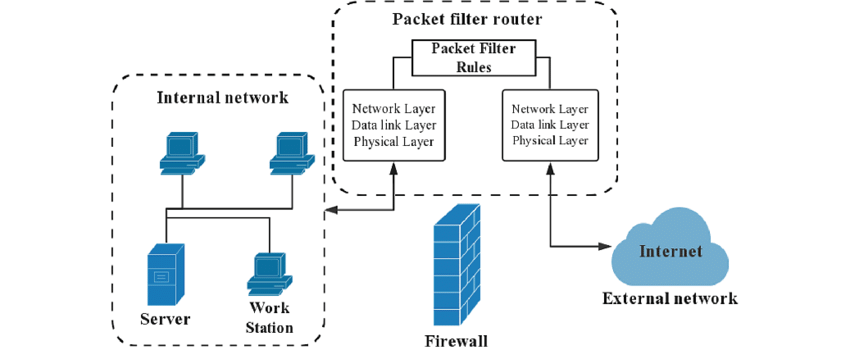
Firewall Security Measures
Implementing effective firewall security measures is crucial for maximizing protection. Here are some strategies I’ve found helpful:
- Set Up Rules and Policies: Establish clear rules that dictate what types of traffic are allowed or blocked. For example, you might want to block all incoming traffic from unknown sources while allowing outgoing traffic from your internal network.
- Regularly Update Firewall Firmware: Cyber threats are constantly evolving, so keeping your firewall’s firmware up to date is vital. Regular updates often include patches for known vulnerabilities.
- Conduct Regular Audits: Periodically review your firewall settings and rules to ensure they align with your current business needs and security posture. I recommend scheduling audits at least once every quarter.
Real-Life Application
Let me share another personal experience related to how firewalls work. A few years back, I was consulting for a small tech startup that had just launched its first product online. They were excited about their growth but were unaware of the potential risks associated with handling sensitive customer data.
I introduced them to a stateful inspection firewall that provided robust monitoring capabilities. Within weeks, we noticed unusual traffic patterns indicating a potential breach attempt from a suspicious IP address. Thanks to the firewall’s active monitoring, we were able to block the threat before any damage occurred.
Understanding how firewalls work is crucial for anyone looking to safeguard their business effectively. By employing various filtering techniques and implementing strong security measures, you can significantly enhance your network protection against cyber threats. Remember that safeguarding your business with firewalls is an ongoing process that requires vigilance and adaptability in today’s fast-paced digital landscape.
What Types of Firewalls Are Available?
When it comes to safeguarding your business with firewalls, understanding the different types of firewalls available is essential. Each type serves a unique purpose and can be tailored to meet the specific needs of your organization. Let’s explore the various types of firewalls, their features, and when to use each one.
1. Packet-Filtering Firewalls
Packet-filtering firewalls are the most basic type of firewall. They work at the network layer and examine packets of data as they attempt to enter or exit your network. These firewalls evaluate packets based on predetermined rules concerning IP addresses, port numbers, and protocols.
- Pros:
- Simple and easy to configure.
- Low latency since they do not inspect packet content.
- Cons:
- Limited protection against sophisticated attacks.
- Cannot analyze the context or state of connections.
I remember setting up a packet-filtering firewall for my first small business website. It was straightforward and provided a basic level of protection against unwanted traffic. However, as my business grew, I realized I needed more advanced security measures.
2. Stateful Inspection Firewalls
Stateful inspection firewalls take security a step further by keeping track of active connections. They monitor the state of network connections and make decisions based on the context of the traffic.
- Pros:
- More secure than packet-filtering firewalls.
- Can recognize established connections and allow return traffic.
- Cons:
- More complex to configure and manage.
- May introduce some latency due to connection tracking.
After experiencing a DDoS attack, I upgraded to a stateful inspection firewall for my business. This change allowed me to block malicious traffic while ensuring legitimate users could access my services without interruption.
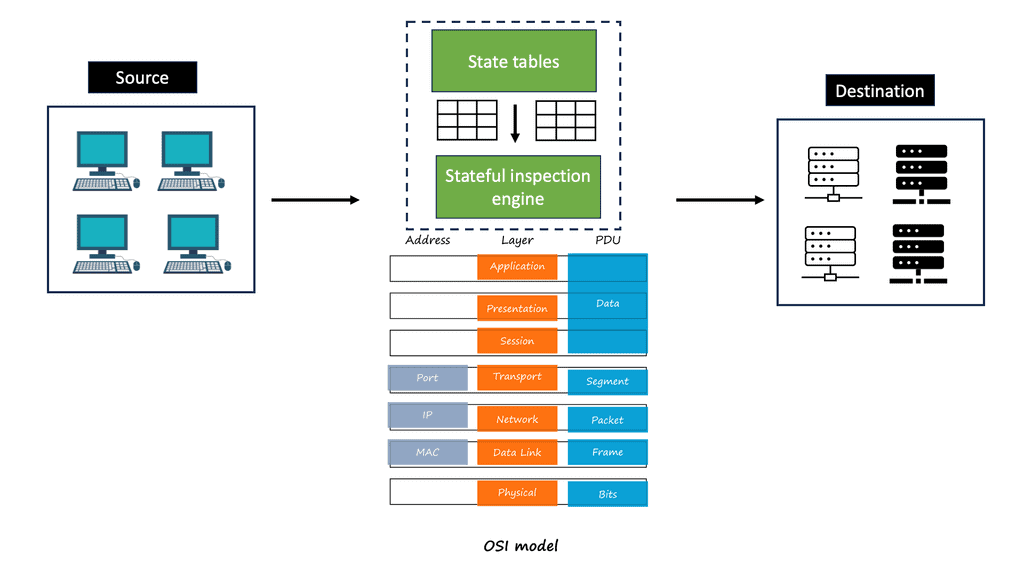
3. Application-Level Gateways (Proxy Firewalls)
Application-level gateways, also known as proxy firewalls, operate at the application layer. They act as intermediaries between users and the services they access, inspecting incoming and outgoing traffic for malicious content.
- Pros:
- Provides deep packet inspection for enhanced security.
- Can filter traffic based on specific applications (e.g., web browsing).
- Cons:
- Can slow down network performance due to extensive inspection.
- More resource-intensive than other firewall types.
In one instance, I worked with a client who had concerns about employees accessing unsafe websites during work hours. We implemented an application-level gateway that not only blocked unwanted sites but also monitored web traffic for potential threats.
4. Next-Generation Firewalls (NGFW)
Next-generation firewalls (NGFW) combine traditional firewall capabilities with additional features like intrusion prevention systems (IPS), application awareness, and advanced threat detection. They are designed to address modern cybersecurity challenges.
- Pros:
- Comprehensive protection against a wide range of threats.
- Ability to inspect encrypted traffic, which is increasingly common.
- Cons:
- Higher cost compared to traditional firewalls.
- Requires more expertise to configure and manage effectively.
When I transitioned my business to an NGFW, I noticed a significant improvement in our overall security posture. The ability to inspect encrypted traffic helped us identify hidden threats that traditional firewalls would have missed.
Comparison Table
To help you visualize the differences between these firewall types, here’s a comparison table summarizing their features:
| Firewall Type | Description | Best Use Case |
|---|---|---|
| Packet-filtering | Basic filtering based on IP and port | Small businesses with limited needs |
| Stateful inspection | Monitors active connections | Medium to large enterprises |
| Application-level gateways | Deep content inspection | Organizations needing high security |
| Next-generation firewalls | Combines multiple features, including IPS | Enterprises requiring advanced protection |
Choosing the right type of firewall is crucial for safeguarding your business with firewalls effectively. Each type offers unique advantages and disadvantages that should be considered based on your specific needs and resources. By understanding these options, you can make informed decisions that enhance your organization’s cybersecurity strategy.
How Can Firewalls Protect Your Business?
When it comes to safeguarding your business with firewalls, understanding how these security devices can protect your organization is crucial. Firewalls are not just a one-size-fits-all solution; they offer a variety of protective measures that can be tailored to meet your specific needs. Let’s explore the various ways firewalls can enhance your business’s cybersecurity and protect against potential threats.
Prevent Unauthorized Access
One of the primary functions of firewalls is to prevent unauthorized access to your network. By establishing strict rules about who can enter and exit your network, firewalls create a secure perimeter around your sensitive data.
- How It Works: Firewalls filter incoming and outgoing traffic based on predefined rules. For instance, if someone tries to access your internal network from an unrecognized IP address, the firewall will block that attempt. This was particularly useful for my business when we noticed suspicious login attempts from unknown locations. The firewall thwarted those attempts before any damage could occur.
Block Malicious Traffic
Firewalls are designed to identify and block malicious traffic before it reaches your network. This includes threats like malware, viruses, and other harmful software.
- Real-World Example: A few years ago, I received an alert from my firewall about an incoming packet that contained malware signatures. Thanks to the proactive measures of the firewall, this threat was blocked before it could infect any of our systems. This incident reinforced my belief in the importance of firewall security measures.
Monitor Network Traffic
Firewalls continuously monitor network traffic for unusual patterns or behaviors that may indicate a potential threat. This real-time monitoring is essential for identifying attacks as they happen.
- Importance of Monitoring: I recall a time when our firewall detected unusual outbound traffic during non-business hours. Upon investigation, we discovered that a malicious script had been trying to send sensitive data outside our network. The firewall’s monitoring capabilities allowed us to respond quickly and mitigate the threat before any data was lost.
Enable Virtual Private Networks (VPNs)
Many firewalls come equipped with VPN capabilities, which allow secure remote access to your network. This is particularly important for businesses with remote employees or multiple locations.
- Benefits of VPNs: By using a VPN through your firewall, you can encrypt data transmitted over the internet, ensuring that sensitive information remains secure even when accessed remotely. I implemented a VPN for my team when we transitioned to remote work during the pandemic, and it greatly enhanced our security posture while allowing employees to work from home safely.

Support Regulatory Compliance
For many businesses, especially those in regulated industries such as finance and healthcare, compliance with data protection regulations is critical. Firewalls play a vital role in meeting these compliance requirements.
- Example from Experience: When I was working with a healthcare startup, we needed to comply with HIPAA regulations regarding patient data protection. Implementing a robust firewall solution helped us ensure that unauthorized access was prevented and that we were following best practices for securing sensitive information.
Provide Network Segmentation
Firewalls allow for network segmentation, which means you can divide your network into smaller segments or zones. This segmentation helps contain potential breaches and limits attackers’ ability to move laterally across your network.
- Real-Life Application: In my own business, we segmented our network into different zones—one for customer data and another for internal operations. This way, even if an attacker gained access to one segment, they would not have free rein over the entire network.
Firewalls are essential tools for safeguarding your business with firewalls effectively. They provide multiple layers of protection against unauthorized access, malicious traffic, and potential breaches while supporting compliance efforts and enabling secure remote access. By understanding how firewalls work and implementing them strategically within your cybersecurity framework, you can significantly enhance your organization’s overall security posture.
What Are the Best Practices for Implementing Firewalls?
Implementing firewalls effectively is crucial for safeguarding your business with firewalls. A well-configured firewall can significantly enhance your cybersecurity posture and protect your organization from various threats. Here are some best practices to consider when implementing firewalls in your business.
1. Define Clear Security Policies
Before you even set up a firewall, it’s essential to define clear security policies. These policies should outline what types of traffic are allowed and what should be blocked. A well-defined policy is the backbone of safeguarding your business with firewalls.
- How to Create Policies: Start by identifying the types of data your business handles and the potential threats you face. For instance, if you handle sensitive customer information, your policy should restrict access to that data to only authorized personnel.
- Personal Experience: When I first set up a firewall for my business, I made the mistake of having vague policies. This led to confusion among my team about what was allowed and what wasn’t. After refining our security policies, we found it much easier to manage access and monitor traffic effectively.
2. Regularly Update Firewall Rules
Cyber threats are constantly evolving, and so should your firewall rules. Regularly updating these rules is crucial for safeguarding your business with firewalls against new vulnerabilities.
- Importance of Updates: Just like software updates on your devices, firewall rules need to be reviewed and updated regularly. This includes adding new rules for emerging threats and removing outdated ones that no longer apply.
- Real-World Example: I recall a time when a new type of malware emerged that exploited outdated firewall rules. We quickly updated our firewall settings to block this threat, preventing potential damage to our systems.
3. Conduct Regular Audits
Regular audits of your firewall settings can help ensure that they align with your current business needs and security posture. This practice is vital for safeguarding your business with firewalls effectively.
- How to Audit: Schedule audits at least once every quarter. During these audits, review the rules, logs, and configurations of your firewall. Look for any anomalies or unauthorized changes.
- Experience Insight: After conducting a thorough audit last year, I discovered several misconfigured rules that could have left us vulnerable. Fixing these issues not only improved our security but also gave me peace of mind knowing we were better protected.
4. Implement Multi-Layered Security
Firewalls should not be your only line of defense; they are most effective when used in conjunction with other security measures. This multi-layered approach is essential for safeguarding your business with firewalls and other security technologies.
- Combining Tools: Consider integrating firewalls with antivirus software, intrusion detection systems (IDS), and data loss prevention (DLP) solutions. This layered strategy provides comprehensive protection against various types of attacks.
- Personal Experience: In my own operations, I’ve found that combining firewalls with an IDS allowed us to detect potential breaches more quickly. The firewall blocked unauthorized access while the IDS alerted us to suspicious activity within our network.
5. Train Your Team
No matter how advanced your firewall is, human error can still lead to vulnerabilities. Training your team on cybersecurity best practices is crucial for safeguarding your business with firewalls effectively.
- Training Topics: Educate employees about recognizing phishing attempts, safe browsing habits, and the importance of adhering to security policies. Regular training sessions can help keep security top-of-mind.
- Real-Life Impact: After implementing regular training sessions in my company, we noticed a significant decrease in phishing-related incidents. Employees became more vigilant and understood how their actions could impact our overall security posture.
Following best practices for implementing firewalls is vital for safeguarding your business with firewalls effectively. By defining clear policies, regularly updating rules, conducting audits, employing multi-layered security strategies, and training your team, you can create a robust defense against cyber threats. Remember that cybersecurity is an ongoing process that requires vigilance and adaptability in today’s fast-paced digital landscape.
How Do Firewalls Integrate with Other Security Measures?
Integrating firewalls with other security measures is essential for safeguarding your business with firewalls effectively. A firewall alone cannot provide complete protection against all cyber threats; it must work in conjunction with other security technologies to create a robust defense strategy. Let’s explore how firewalls can be integrated with various security measures to enhance your overall cybersecurity posture.
Antivirus and Anti-Malware Software
One of the most common integrations is between firewalls and antivirus or anti-malware software. While firewalls block unauthorized access and monitor traffic, antivirus software scans for malicious files and programs.
- How They Work Together: Firewalls can prevent malware from entering your network, while antivirus software can detect and remove any malware that does manage to get through. This dual-layer approach is crucial for safeguarding your business with firewalls and ensuring that your systems remain clean.
- Personal Experience: In my early days of business, I relied solely on a firewall for protection. However, after experiencing a malware infection that slipped through, I realized the importance of integrating antivirus software. The combination of both tools provided comprehensive protection against a wide range of threats.
Intrusion Detection and Prevention Systems (IDPS)
Intrusion Detection and Prevention Systems (IDPS) are designed to monitor network traffic for suspicious activity and respond accordingly. Integrating an IDPS with your firewall enhances your ability to detect and respond to threats in real-time.
- Benefits of Integration: While firewalls block unauthorized access, IDPS can analyze traffic patterns and alert you to potential intrusions. This integration allows for quicker responses to threats, which is vital for safeguarding your business with firewalls.
- Real-World Example: I once consulted for a company that experienced repeated unauthorized access attempts. By integrating an IDPS with their firewall, we were able to identify the source of the attacks and implement measures to block them effectively.
Data Loss Prevention (DLP) Solutions
Data Loss Prevention (DLP) solutions help protect sensitive data from being lost, misused, or accessed by unauthorized users. When integrated with firewalls, DLP can provide an additional layer of security by monitoring data flows across your network.
- How DLP Enhances Firewall Protection: Firewalls can restrict access to certain data, while DLP solutions can monitor outgoing traffic for sensitive information being transmitted without authorization. This dual approach is essential for safeguarding your business with firewalls and protecting critical data.
- Personal Insight: In my organization, we implemented a DLP solution alongside our firewall after recognizing the need to protect customer data more effectively. This integration allowed us to track any unauthorized attempts to transmit sensitive information outside our network.
Security Information and Event Management (SIEM) Systems
Security Information and Event Management (SIEM) systems aggregate and analyze security data from various sources, including firewalls, IDPS, and antivirus software. Integrating SIEM with firewalls provides comprehensive visibility into your security landscape.
- Benefits of SIEM Integration: By collecting logs from firewalls and other security devices, SIEM systems can identify trends, detect anomalies, and generate alerts for potential threats. This holistic view is critical for safeguarding your business with firewalls as it allows you to respond proactively.
- Experience Insight: After implementing a SIEM system in my own operations, I was able to identify patterns in attempted breaches that we hadn’t noticed before. This insight helped us adjust our firewall rules and improve our overall security strategy.
Cloud Security Solutions
As businesses increasingly move their operations to the cloud, integrating cloud security solutions with traditional firewalls has become essential. Cloud-based firewalls offer flexibility while maintaining strong security protocols.
- How Cloud Security Enhances Firewalls: Cloud security solutions can extend the protective capabilities of on-premises firewalls by monitoring cloud applications and services used by your organization. This integration is vital for safeguarding your business with firewalls, especially if you rely on cloud storage or SaaS applications.
- Real-Life Application: In my experience working with a tech startup that heavily relied on cloud services, integrating cloud security solutions with their existing firewall provided them with enhanced visibility into their cloud environment while ensuring compliance with data protection regulations.
Integrating firewalls with other security measures is crucial for safeguarding your business with firewalls effectively. By combining firewalls with antivirus software, IDPS, DLP solutions, SIEM systems, and cloud security solutions, you can create a comprehensive defense strategy that addresses various cyber threats. Remember that cybersecurity is not just about having one tool; it’s about creating a multi-layered approach that adapts to the evolving threat landscape.
What Are the Limitations of Firewalls?
While firewalls are a critical component of any cybersecurity strategy, they are not a panacea. Understanding the limitations of firewalls is essential for safeguarding your business with firewalls effectively. By recognizing these limitations, you can implement additional security measures to ensure comprehensive protection. Let’s explore some of the key limitations of firewalls and how they can impact your business.
Inability to Prevent Insider Threats
One of the most significant limitations of firewalls is their inability to protect against insider threats. These threats come from individuals within your organization, such as employees or contractors, who may intentionally or unintentionally compromise security.
- Why It Matters: Firewalls primarily focus on external threats, monitoring traffic coming in and out of your network. However, if an employee inadvertently downloads malware or intentionally steals sensitive data, the firewall may not detect this activity.
- Personal Experience: I once had a colleague who accidentally downloaded a malicious file while working from home. Our firewall didn’t flag the download because it originated from an internal source. This incident highlighted the importance of training employees on safe practices and implementing additional security measures alongside firewalls.

Limited Visibility into Encrypted Traffic
As more organizations use encryption to protect their data, firewalls face challenges in inspecting encrypted traffic. While encryption is essential for protecting sensitive information, it can also create blind spots for firewalls.
- How This Affects Security: If a firewall cannot inspect encrypted traffic, it may allow malicious content to pass through undetected. Cybercriminals often exploit this limitation by hiding malware within encrypted packets.
- Real-World Example: In my own experience, we encountered a situation where our firewall allowed encrypted malware to infiltrate our network. After this incident, we invested in a next-generation firewall that included features for decrypting and inspecting encrypted traffic, significantly enhancing our security posture.
Dependence on Proper Configuration
Firewalls are only as effective as their configuration. Misconfigured firewalls can create vulnerabilities that cybercriminals can exploit, undermining the very purpose of safeguarding your business with firewalls.
- Common Configuration Issues: Some common misconfigurations include overly permissive rules that allow too much traffic or failing to update rules in response to changing threats. Regular audits and updates are essential to maintain optimal firewall performance.
- Experience Insight: I once worked with a client who had a firewall configured with overly broad rules that allowed unnecessary access to sensitive data. After conducting an audit and tightening their rules, we were able to close several security gaps that could have been exploited.
Lack of Contextual Awareness
Firewalls typically operate based on predefined rules and do not possess contextual awareness of user behavior or network activity. This limitation means they may not be able to distinguish between legitimate and malicious actions effectively.
- Impact on Security: For example, if an employee accesses sensitive data during unusual hours, a traditional firewall may not flag this as suspicious activity unless there are specific rules in place to do so.
- Real-Life Application: To address this limitation in my own business, we implemented user behavior analytics (UBA) alongside our firewall. UBA solutions analyze user behavior patterns and alert us to any anomalies that could indicate a potential breach.
Vulnerability to Advanced Threats
As cyber threats become more sophisticated, traditional firewalls may struggle to keep up with advanced attack techniques such as polymorphic malware or zero-day exploits.
- Why This Is Important: Advanced persistent threats (APTs) often employ multiple tactics to bypass traditional security measures, including firewalls. Relying solely on firewalls can leave your organization vulnerable to these sophisticated attacks.
- Personal Experience: After experiencing an APT targeting our industry, we realized that our existing firewall was not enough. We supplemented our firewall with advanced threat detection systems that could identify and respond to complex attacks more effectively.
While firewalls play a vital role in safeguarding your business with firewalls, it’s essential to recognize their limitations. By understanding these weaknesses—such as their inability to prevent insider threats, limited visibility into encrypted traffic, dependence on proper configuration, lack of contextual awareness, and vulnerability to advanced threats—you can take proactive steps to enhance your overall security strategy. Implementing additional layers of protection will help ensure that your business remains secure in an increasingly complex cybersecurity landscape.
Future Trends in Firewall Technology
As the cybersecurity landscape continues to evolve, so too does the technology behind firewalls. Staying informed about future trends in firewall technology is essential for safeguarding your business with firewalls effectively. Here are some key trends that are shaping the future of firewall technology and how they can enhance your security posture.
Artificial Intelligence and Machine Learning
Artificial intelligence (AI) and machine learning (ML) are becoming increasingly integrated into firewall technologies. These advanced systems can analyze vast amounts of data to identify patterns and detect anomalies that traditional firewalls may miss.
- Benefits of AI/ML Integration: By leveraging AI and ML, firewalls can adapt to new threats in real-time, improving their ability to block malicious traffic. This dynamic approach enhances the overall effectiveness of safeguarding your business with firewalls.
- Personal Experience: I recently implemented an AI-driven firewall solution in my organization. The system continuously learns from network traffic patterns and automatically adjusts its rules to block emerging threats, significantly reducing our response time to potential attacks.

Cloud-Based Firewalls
As more businesses migrate to cloud environments, cloud-based firewalls are gaining popularity. These firewalls provide flexibility and scalability while maintaining strong security protocols.
- Why Cloud Firewalls Matter: Cloud-based firewalls can protect data across multiple locations and devices, making them ideal for organizations with remote workers or distributed teams. This capability is crucial for safeguarding your business with firewalls as you adapt to modern work environments.
- Real-World Application: In my experience working with a remote-first company, we transitioned to a cloud-based firewall that allowed us to secure our data without compromising performance. This solution provided seamless protection for our employees, regardless of where they worked.
Zero Trust Security Model
The Zero Trust security model operates on the principle of “never trust, always verify.” This approach requires strict identity verification for every person and device attempting to access resources on a network, regardless of whether they are inside or outside the network perimeter.
- Integration with Firewalls: Firewalls will increasingly incorporate Zero Trust principles by requiring authentication and authorization for all traffic, effectively enhancing security measures. This is vital for safeguarding your business with firewalls, especially as remote work becomes more common.
- Experience Insight: After adopting a Zero Trust model in my organization, we saw a significant reduction in unauthorized access attempts. By integrating this approach with our existing firewall, we ensured that every user had the appropriate permissions before accessing sensitive data.
Enhanced Visibility and Reporting
Future firewall technologies will focus on providing enhanced visibility into network activity and more robust reporting capabilities. This increased transparency is essential for identifying potential threats quickly.
- Importance of Visibility: Enhanced visibility allows security teams to monitor traffic patterns, detect anomalies, and respond proactively to potential breaches. This capability is critical for safeguarding your business with firewalls, as it enables organizations to stay ahead of emerging threats.
- Personal Experience: I implemented a next-generation firewall that offered advanced reporting features, allowing us to generate detailed logs of all network activity. This visibility helped us identify unusual behavior patterns that could indicate a potential breach.
Integration with Other Security Solutions
As cybersecurity threats become more sophisticated, the integration of firewalls with other security solutions will become increasingly important. This includes collaboration with intrusion detection systems (IDS), endpoint protection platforms (EPP), and Security Information and Event Management (SIEM) systems.
- Benefits of Integration: By integrating firewalls with other security solutions, organizations can create a more comprehensive defense strategy that addresses multiple attack vectors. This holistic approach is essential for safeguarding your business with firewalls as part of a multi-layered security framework.
- Real-Life Application: In my organization, we successfully integrated our firewall with an IDS and SIEM system, which allowed us to correlate data from multiple sources and respond more effectively to potential threats. This integration enhanced our overall security posture significantly.
Staying informed about future trends in firewall technology is crucial for safeguarding your business with firewalls effectively. By embracing advancements such as artificial intelligence, cloud-based solutions, the Zero Trust security model, enhanced visibility, and integration with other security measures, you can better protect your organization against evolving cyber threats. As technology continues to advance, adapting your firewall strategy will be key to maintaining a secure digital environment.
Final Thoughts: Strengthening Your Cybersecurity Posture with Firewalls
As we wrap up our exploration of firewalls, it’s essential to emphasize the critical role they play in safeguarding your business with firewalls. In today’s digital landscape, where cyber threats are increasingly sophisticated and prevalent, having a robust firewall strategy is not just an option—it’s a necessity. Let’s summarize the key takeaways and discuss actionable steps you can take to strengthen your cybersecurity posture.
Recognize the Importance of Firewalls
Firewalls serve as the first line of defense against cyber threats. They monitor incoming and outgoing traffic, block unauthorized access, and protect sensitive data from malicious attacks. Understanding their importance is crucial for safeguarding your business with firewalls effectively.
- Personal Experience: When I first implemented a firewall in my business, I noticed an immediate improvement in our security posture. The peace of mind that came from knowing our network was protected allowed me to focus on growth rather than constantly worrying about potential breaches.
Choose the Right Type of Firewall
Selecting the right type of firewall for your organization is vital. Whether it’s a packet-filtering firewall, stateful inspection firewall, application-level gateway, or next-generation firewall, each has its strengths and weaknesses.
- Actionable Advice: Assess your business needs and choose a firewall that aligns with your security requirements. For example, if you handle sensitive customer data, consider investing in a next-generation firewall that offers advanced threat detection capabilities.
Implement Best Practices
To maximize the effectiveness of your firewalls, follow best practices such as defining clear security policies, regularly updating rules, conducting audits, and training your team on cybersecurity awareness. These practices are essential for safeguarding your business with firewalls effectively.
- Experience Insight: After implementing regular training sessions for my team on cybersecurity best practices, we saw a noticeable decrease in security incidents. Educating employees about potential threats and safe practices is key to creating a culture of security within your organization.
Integrate with Other Security Measures
Firewalls should not operate in isolation. Integrating them with other security measures—such as antivirus software, intrusion detection systems (IDS), data loss prevention (DLP) solutions, and Security Information and Event Management (SIEM) systems—creates a multi-layered defense strategy.
- Real-World Example: In my organization, integrating our firewall with an IDS allowed us to detect potential breaches more quickly and respond proactively. This layered approach significantly enhanced our overall security posture.
Stay Informed About Emerging Threats
The cybersecurity landscape is constantly evolving, with new threats emerging regularly. Staying informed about these threats and understanding how they can impact your business is crucial for safeguarding your business with firewalls effectively.
- Actionable Steps: Subscribe to cybersecurity newsletters, attend industry conferences, and participate in online forums to stay updated on the latest trends and threats. This knowledge will empower you to make informed decisions about your security strategy.
Strengthening your cybersecurity posture involves recognizing the critical role that firewalls play in protecting your organization from cyber threats. By understanding their importance, choosing the right type of firewall, implementing best practices, integrating with other security measures, and staying informed about emerging threats, you can create a robust defense strategy that ensures the safety of your business.
Remember that safeguarding your business with firewalls is not just about technology; it’s about fostering a culture of security within your organization where everyone understands their role in protecting sensitive information. As you move forward, prioritize cybersecurity as an integral part of your business strategy to thrive in today’s digital world.
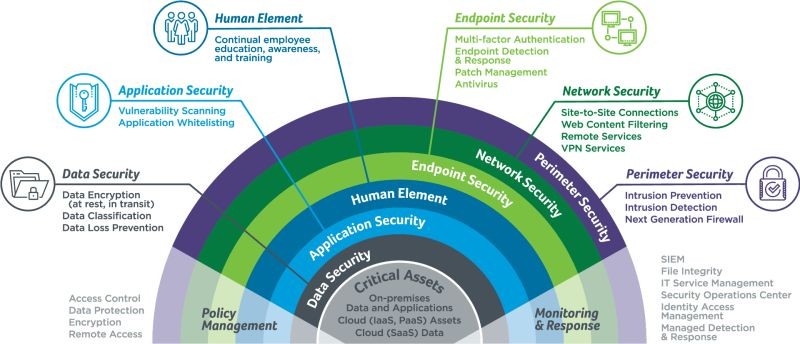
Frequently Asked Questions (F.A.Q.s)
- What is the primary function of a firewall?
- Firewalls monitor and control incoming and outgoing network traffic based on predetermined security rules to prevent unauthorized access.
- How do I know which type of firewall is best for my business?
- Assess your specific needs based on factors like data sensitivity, network size, and available resources to determine which type of firewall offers the best protection.
- Can a firewall prevent all cyber attacks?
- No, while firewalls are essential for blocking many types of attacks, they cannot prevent all cyber threats—especially those originating from inside the organization.
- What are the differences between hardware and software firewalls?
- Hardware firewalls are standalone devices that protect entire networks; software firewalls are installed on individual devices to protect them specifically.
- How often should I update my firewall settings?
- Regular updates should be conducted at least quarterly or whenever there are significant changes in your network or emerging threats.
- What are some common mistakes when configuring a firewall?
- Common mistakes include overly permissive rules, failing to update settings regularly, and neglecting to conduct audits for misconfigurations.
- Do I need a firewall if I have antivirus software?
- Yes, both firewalls and antivirus software serve different purposes; using both provides layered protection against various types of cyber threats.
- How can I monitor my firewall’s effectiveness?
- Regularly review logs generated by your firewall for unusual activity and conduct audits to ensure compliance with established security policies.
- What should I do if my firewall blocks legitimate traffic?
- Review the firewall rules to identify why legitimate traffic is being blocked and adjust settings accordingly while ensuring that security is not compromised.
- Are next-generation firewalls worth the investment for small businesses?
- Yes! Next-generation firewalls offer advanced features such as threat intelligence and deep packet inspection that can significantly enhance security for businesses of all sizes.
This concludes our comprehensive blog post on firewalls! If you have any further questions or need additional information on any specific section or topic related to this article, feel free to ask!