Introduction
Ransomware attacks have become a significant threat to businesses of all sizes. In recent years, these malicious attacks have surged, causing severe disruptions and financial losses. Understanding ransomware and how to protect against it is crucial for any business owner.
When I first encountered ransomware in my early days as an entrepreneur, I was shocked by its impact. A small tech company I worked with fell victim to a ransomware attack. They lost access to critical data and faced a hefty ransom demand. The experience taught me valuable lessons about cybersecurity and the importance of proactive measures.In this blog post, we will explore the ins and outs of ransomware attacks.
We will cover what ransomware is, how it works, and why businesses are targeted. Additionally, we will provide actionable tips on preventing ransomware and effective recovery strategies. By the end of this article, you will have a solid understanding of understanding ransomware and how to protect against it.

Image: A computer screen displaying a ransomware message
Ransomware attacks often begin with a simple click on a malicious link or an unsuspecting download. This can happen to anyone, regardless of their tech-savviness. Therefore, knowing how to identify potential threats is essential for preventing ransomware.
Moreover, the consequences of these attacks can be devastating. Businesses can face operational downtime, loss of customer trust, and even legal issues. For example, after that initial attack I witnessed, the company spent months recovering their data and reputation. They learned the hard way that being unprepared can lead to dire consequences.
As we delve deeper into this topic, remember that understanding ransomware and how to protect against it is not just about technical knowledge; it’s about creating a culture of security within your organization. This mindset will help you safeguard your business against future threats.
So, let’s get started! In the next section, we’ll define what ransomware is and explore its various forms.
What is Ransomware?
Ransomware is a type of malicious software designed to block access to a computer system or data until a ransom is paid. It’s a serious threat that can cripple businesses overnight. Understanding ransomware and how to protect against it starts with knowing what it is and how it operates.
The Different Types of Ransomware
There are several types of ransomware, each with its own method of attack. The most common types include:
- Crypto Ransomware: This type encrypts files on the victim’s system, making them inaccessible. The attacker demands payment for the decryption key. For example, when I consulted for a healthcare provider, they faced a crypto ransomware attack that locked patient records. The situation was dire, and they had to act fast.
- Locker Ransomware: Unlike crypto ransomware, locker ransomware locks users out of their devices entirely. Users see a screen that prevents them from accessing anything until the ransom is paid.
- Scareware: This type tricks users into believing their system is infected or compromised. It often displays fake alerts and demands payment to fix the supposed issues.
- Doxware: This variant threatens to publish sensitive information unless the ransom is paid. This can be particularly damaging for businesses that handle confidential data.
How Ransomware Works
Understanding ransomware and how to protect against it also involves knowing how these attacks typically occur. Most often, ransomware spreads through phishing emails or malicious downloads. For instance, an employee might receive an email that appears to be from a trusted source, containing an attachment that, when opened, installs ransomware on their system.
Once installed, the ransomware begins encrypting files on the infected device and often spreads to other connected systems or networks. The attackers then display a ransom note demanding payment in cryptocurrency, which is hard to trace.
Real-Life Example
A few years ago, I worked with a small marketing agency that experienced a crypto ransomware attack. One employee clicked on a phishing link in an email, which unleashed the malware across their network. They lost access to critical client files and were faced with a ransom demand of $50,000! Fortunately, they had robust backups and were able to restore their data without paying the ransom. This experience highlighted the importance of having preventive measures in place.

Image: A phishing email example
The Evolution of Ransomware Attacks
Ransomware has evolved significantly over the years. Initially, it was relatively simple and targeted individual users. However, today’s attackers are more sophisticated and often target large organizations with substantial financial resources. They may also employ double extortion tactics—first encrypting data and then threatening to leak sensitive information if the ransom isn’t paid.
This evolution emphasizes why understanding ransomware and how to protect against it is vital for any business today. As attacks become more complex, so must our strategies for prevention and recovery.In summary, knowing what ransomware is and how it operates lays the groundwork for effective protection strategies. In the next section, we will explore why businesses are targeted by these attacks and what makes them vulnerable.
How Does Ransomware Work?
Understanding ransomware and how to protect against it requires a closer look at the mechanics behind these attacks. Ransomware operates through a series of steps that exploit vulnerabilities in a business’s cybersecurity defenses. By grasping how ransomware works, you can better prepare your organization to defend against it.
Infection Methods
Ransomware typically enters a system through various infection methods. The most common ways include:
- Phishing Emails: This is the most prevalent method. Attackers send emails that appear legitimate, tricking users into clicking on malicious links or downloading infected attachments. For example, I once received an email that looked like it was from a reputable service provider, but it contained a link to malware. Recognizing the signs of phishing is crucial for preventing ransomware.
- Malicious Downloads: Sometimes, ransomware can be hidden in software downloads from untrustworthy sources. Users might unknowingly download infected software, which then installs the ransomware on their systems.
- Exploiting Software Vulnerabilities: Cybercriminals often exploit vulnerabilities in software applications or operating systems. If a business does not regularly update its software, it may become an easy target for ransomware attacks.
- Remote Desktop Protocol (RDP) Attacks: Attackers can gain access to systems through unsecured RDP connections. Once inside, they can deploy ransomware across the network.
The Encryption Process
Once ransomware infiltrates a system, it begins the encryption process almost immediately. Understanding this process is crucial for understanding ransomware and how to protect against it. The malware scans for files—documents, images, databases—and encrypts them using complex algorithms. This makes the files inaccessible to users.During my time working with a financial services firm, I witnessed firsthand how quickly ransomware could encrypt files. Within minutes, critical client data was locked away, and the attackers displayed a ransom note demanding payment in exchange for the decryption key.
Ransom Demands
After encrypting the files, ransomware displays a ransom note on the infected device. This note typically includes:
- Instructions on how to pay the ransom.
- A deadline for payment.
- Threats about permanently losing access to files if payment isn’t made.
Most attackers prefer cryptocurrency for payments due to its anonymity. This makes tracking down the perpetrators nearly impossible.
Real-Life Example
A friend of mine who runs a small e-commerce business fell victim to a ransomware attack last year. The attackers gained access through a phishing email that appeared to be from a shipping provider. Within hours, they encrypted customer data and demanded $20,000 in Bitcoin.
Fortunately, my friend had implemented solid backup protocols and was able to restore his data without paying the ransom.This experience reinforced my belief in the importance of understanding ransomware and how to protect against it through employee training and robust cybersecurity measures.
Understanding how ransomware works is essential for businesses looking to protect themselves effectively. By recognizing infection methods and knowing what happens during an attack, organizations can implement strategies for preventing ransomware and ensure they are prepared if an attack occurs.
Why Are Businesses Targeted?
Understanding ransomware and how to protect against it involves recognizing why businesses are often the primary targets of these attacks. Ransomware attackers typically seek out organizations that can afford to pay the ransom, making certain types of businesses more appealing than others. Let’s explore the reasons behind this trend.
Financial Motivation
The most significant factor driving ransomware attacks is financial gain. Attackers know that many businesses, especially those in lucrative sectors like finance, healthcare, and e-commerce, have the resources to pay substantial ransoms. For instance, when I consulted for a healthcare provider, they were targeted because of the sensitive nature of their data and their ability to pay a ransom quickly.
In fact, according to a report from Cybersecurity Ventures, ransomware attacks are expected to cost businesses over $20 billion annually by 2025. This staggering figure highlights the financial motivation behind these attacks and underscores the importance of understanding ransomware and how to protect against it.
Lack of Cybersecurity Preparedness
Many businesses underestimate their vulnerability to cyber threats. Small and medium-sized enterprises (SMEs) often believe they are too insignificant to be targeted. However, this misconception makes them prime targets for attackers. Without robust cybersecurity measures in place, these businesses are easy prey for ransomware attacks.
During my early days as an entrepreneur, I worked with a small startup that had minimal cybersecurity protocols. They fell victim to a ransomware attack that locked them out of critical project files. This incident taught me that every business, regardless of size, must prioritize cybersecurity as part of their operational strategy.
Valuable Data
Businesses store vast amounts of valuable data, from customer information to proprietary research. Ransomware attackers know this and often target organizations with sensitive data that could cause significant disruption if lost or leaked. For example, companies in the legal or financial sectors often hold confidential client information that is crucial for their operations.
When I was involved with a law firm that experienced a ransomware attack, they lost access to case files and client communications. The attackers demanded a hefty ransom to restore access. This incident highlighted how valuable data can make businesses attractive targets for ransomware.
Operational Disruption
Ransomware attacks can cause significant operational disruptions. Attackers often choose targets based on how much chaos they can create if their demands are not met. For instance, hospitals and emergency services are frequently targeted because the inability to access patient data can have dire consequences.In my experience working with healthcare organizations, I’ve seen how critical it is for them to have effective strategies for preventing ransomware. The potential impact on patient care makes these institutions particularly vulnerable.

Image: statistics on ransomware attack costs
Understanding why businesses are targeted by ransomware is essential for developing effective protection strategies. Financial motivation, lack of preparedness, valuable data, and potential operational disruption all contribute to making organizations attractive targets for cybercriminals.
What Are the Consequences of Ransomware Attacks?
Understanding ransomware and how to protect against it is not just about prevention; it’s also crucial to grasp the severe consequences that these attacks can inflict on businesses. The impact of a ransomware attack can be devastating, affecting everything from operations to reputation. Let’s explore these consequences in detail.
Operational Downtime
One of the most immediate effects of a ransomware attack is operational downtime. When systems are compromised, businesses often lose access to critical data and applications. This can halt operations entirely, leading to lost revenue and productivity.For example, I once consulted for a manufacturing company that suffered a ransomware attack. Their production line came to a standstill for several days while they worked to restore access to their systems.
The financial losses were staggering, amounting to hundreds of thousands of dollars in just a few days of downtime. This experience reinforced the importance of understanding ransomware and how to protect against it through effective backup strategies.
Financial Losses
The financial implications of ransomware attacks can be severe. Beyond the ransom itself—often in the thousands or even millions of dollars—businesses incur additional costs related to recovery efforts, legal fees, and potential regulatory fines. According to a report from Coveware, the average ransom payment in 2021 was around $220,000, but many organizations faced costs that far exceeded this amount when considering recovery efforts.
In my experience with various clients, I’ve seen how quickly costs can escalate after an attack. One organization I worked with spent over $1 million recovering from an attack that initially demanded a $50,000 ransom. This highlights the need for businesses to invest in preventive measures rather than waiting until it’s too late.
Reputational Damage
Ransomware attacks can also lead to significant reputational damage. Customers expect businesses to protect their sensitive information. If a company falls victim to an attack, it can erode trust and lead to customer attrition.For instance, I remember working with a retail client who experienced a ransomware incident that exposed customer data. Despite restoring their systems without paying the ransom, they lost many customers who felt their information was no longer safe with them. Rebuilding that trust took years and required substantial investment in marketing and cybersecurity improvements.
Legal Repercussions
Businesses may face legal consequences following a ransomware attack, especially if sensitive customer data is compromised. Data protection regulations like GDPR and HIPAA impose strict requirements on how businesses handle personal information. Failing to meet these requirements can result in hefty fines and legal action.
In my consulting work, I’ve seen companies hit with lawsuits after failing to protect customer data during an attack. These legal repercussions can further strain resources and distract from core business operations.
Long-Term Impact on Business Strategy
Finally, the long-term impact of a ransomware attack can reshape a business’s strategy. After experiencing an attack, many organizations realize they need to invest more heavily in cybersecurity measures. This shift often involves reallocating budgets and resources away from growth initiatives toward security enhancements.
For example, after a significant ransomware incident, one tech startup I advised decided to implement comprehensive cybersecurity training for all employees. They recognized that human error was often the weakest link in their defenses. By prioritizing cybersecurity awareness and training, they aimed to prevent future incidents while maintaining their growth trajectory.
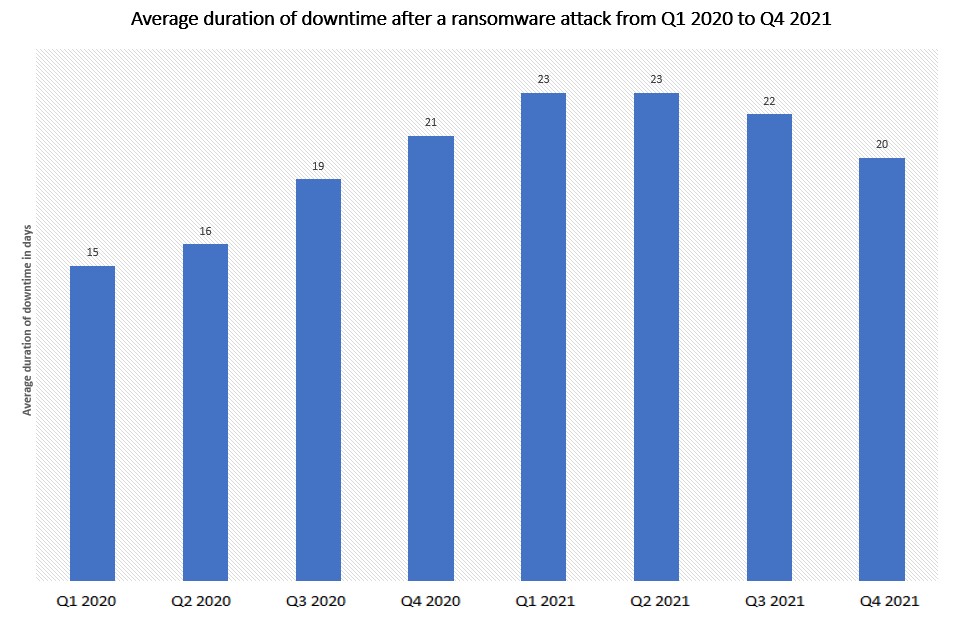
Image: statistics on operational downtime due to ransomware
The consequences of ransomware attacks are profound and far-reaching. From operational downtime and financial losses to reputational damage and legal repercussions, the impact can be devastating for any business. Understanding these consequences is vital for developing effective strategies for preventing ransomware and ensuring your organization is prepared for potential threats.
How Can Businesses Protect Against Ransomware?
Understanding ransomware and how to protect against it is essential for every business today. With the increasing frequency and sophistication of ransomware attacks, implementing effective protective measures is no longer optional; it’s a necessity. Here are some actionable strategies that businesses can adopt to safeguard themselves against these threats.
Employee Training and Awareness
One of the most effective ways to prevent ransomware is through comprehensive employee training. Human error is often the weakest link in cybersecurity. By educating employees about the dangers of phishing emails and suspicious downloads, businesses can significantly reduce their risk of falling victim to ransomware.
In my experience, I’ve seen firsthand how training can make a difference. At a mid-sized company I worked with, we implemented regular cybersecurity training sessions. Employees learned how to recognize phishing attempts and the importance of not clicking on unknown links. As a result, they reported suspicious emails instead of opening them, which helped prevent a potential ransomware attack.
Regular Software Updates and Patch Management
Keeping software up to date is another critical component of understanding ransomware and how to protect against it. Cybercriminals often exploit vulnerabilities in outdated software to gain access to systems. Regularly updating operating systems, applications, and security software can help close these gaps.
For example, I once consulted for a financial institution that had neglected software updates for several months. They experienced a ransomware attack that exploited an unpatched vulnerability in their system. After this incident, they established a strict update schedule, ensuring that all software was regularly reviewed and updated.
Strong Password Policies
Implementing strong password policies is vital for preventing unauthorized access to systems. Weak passwords are easy targets for attackers. Businesses should enforce the use of complex passwords and encourage employees to change them regularly.
In my own business, we adopted a policy requiring passwords to be at least 12 characters long and include a mix of letters, numbers, and symbols. Additionally, we implemented two-factor authentication (2FA) for all critical systems. This extra layer of security makes it significantly harder for attackers to gain access, thus enhancing our defenses against ransomware.
Data Backups and Recovery Plans
Having robust data backup strategies is one of the most effective ways to protect against ransomware attacks. Regularly backing up critical data ensures that even if files are encrypted by ransomware, businesses can restore their information without paying the ransom.
During my tenure at a tech startup, we established an automated backup system that saved our data daily. When we faced a minor ransomware scare due to an employee’s mistake, we were able to restore our data from backups without any disruption to our operations. This experience reinforced the importance of having solid ransomware recovery strategies in place.
Incident Response Planning
Every business should have an incident response plan specifically tailored for ransomware attacks. This plan should outline steps to take when an attack occurs, including isolating infected systems, notifying stakeholders, and engaging cybersecurity professionals.
In one instance, I worked with a healthcare provider that had developed an incident response plan before they faced an actual attack. When the attack occurred, they followed their plan meticulously. This preparation allowed them to respond quickly, minimizing damage and downtime.

Image: strong password examples
Protecting against ransomware requires a multi-faceted approach that includes employee training, regular software updates, strong password policies, data backups, and incident response planning. Understanding ransomware and how to protect against it is crucial for any organization looking to safeguard its data and maintain operational integrity.
In the next section, we will discuss effective ransomware recovery strategies that businesses can implement if they fall victim to an attack.
What Are Effective Ransomware Recovery Strategies?
Understanding ransomware and how to protect against it is essential, but it’s equally important to know what to do if your business falls victim to an attack. Having effective ransomware recovery strategies in place can make the difference between a minor setback and a catastrophic loss. Here are some key strategies that can help businesses recover from ransomware incidents.
Immediate Response Steps
When a ransomware attack occurs, the first step is to respond quickly. Understanding ransomware and how to protect against it means knowing how to act in an emergency. Here’s what you should do immediately:
- Isolate Infected Systems: Disconnect any infected devices from the network to prevent the ransomware from spreading. This includes unplugging network cables and disabling Wi-Fi connections.
- Assess the Situation: Determine the extent of the infection. Identify which systems and files have been affected. This assessment will help you decide on the best course of action.
- Notify Stakeholders: Inform your IT team and key stakeholders about the incident. Transparency is crucial in these situations, as it allows for coordinated efforts in responding to the attack.
- Engage Cybersecurity Professionals: If your organization lacks in-house expertise, consider hiring external cybersecurity experts who specialize in ransomware recovery. Their experience can be invaluable in navigating the complexities of recovery.
Data Restoration from Backups
One of the most effective ransomware recovery strategies is restoring data from backups. If your business has implemented regular backup protocols, you can recover lost files without paying the ransom.For example, when I advised a small law firm that had been attacked, they were able to restore their client files from backups taken just hours before the attack occurred. This quick recovery saved them from paying a ransom and minimized disruption to their operations.To ensure successful data restoration:
- Verify that your backups are complete and up-to-date.
- Test your backup restoration process regularly to ensure it works effectively.
- Keep backups stored securely offline or in a cloud environment that is not directly connected to your main network.
Communication with Stakeholders
Effective communication during a ransomware incident is critical. Keeping stakeholders informed can help maintain trust and transparency. Here’s how to manage communication:
- Notify Employees: Inform employees about the situation and provide clear instructions on what they should do next.
- Update Customers: If customer data has been compromised, notify affected clients promptly and explain what steps you are taking to address the issue.
- Engage Law Enforcement: Consider reporting the incident to law enforcement agencies. They may be able to assist with investigations or provide guidance on how to proceed.
Evaluate Payment Options
In some cases, businesses may consider paying the ransom, especially if they lack adequate backups or if critical operations are severely impacted. However, this decision should not be taken lightly. Understanding ransomware and how to protect against it includes knowing the risks associated with paying ransoms:
- There’s no guarantee that paying will result in data recovery.
- Paying may encourage further attacks on your organization or others.
- It can also complicate legal issues regarding data breaches.
If you do decide to pay, consult with legal counsel and cybersecurity experts first.
Post-Incident Review
After recovering from a ransomware attack, conduct a thorough post-incident review. This evaluation should include:
- Analyzing how the attack occurred.
- Identifying weaknesses in your security posture.
- Developing an updated incident response plan based on lessons learned.
In my experience working with various organizations, these reviews are crucial for improving defenses against future attacks. They allow businesses to adapt their strategies based on real-world incidents.
Having effective ransomware recovery strategies is vital for any business facing an attack. By responding quickly, restoring data from backups, communicating effectively with stakeholders, evaluating payment options carefully, and conducting post-incident reviews, organizations can minimize damage and recover more efficiently.
How to Stay Informed About Ransomware Threats?
Understanding ransomware and how to protect against it requires ongoing education and awareness. The cybersecurity landscape is constantly evolving, with new threats emerging regularly. Staying informed about ransomware threats is crucial for businesses to adapt their strategies and enhance their defenses. Here are several effective ways to keep your organization updated on the latest ransomware developments.
Subscribe to Cybersecurity News and Alerts
One of the best ways to stay informed is by subscribing to reputable cybersecurity news sources and alerts. Websites like Krebs on Security, Threatpost, and the Cybersecurity & Infrastructure Security Agency (CISA) provide timely updates on the latest ransomware attacks, vulnerabilities, and security best practices.
In my experience, I’ve found that staying updated through these sources helps businesses anticipate potential threats. For example, when a new strain of ransomware was reported in the news, I alerted my clients to review their security protocols immediately. This proactive approach allowed them to implement additional safeguards before they could be targeted.
Join Cybersecurity Communities
Engaging with cybersecurity communities can provide valuable insights into emerging threats. Online forums, social media groups, and professional organizations often share information about recent attacks and prevention strategies. Platforms like LinkedIn and Reddit have active groups where professionals discuss the latest trends in cybersecurity.
I’ve personally benefited from participating in these communities. They offer a wealth of knowledge from experienced professionals who share real-world experiences and solutions. This collaborative environment fosters learning and keeps you informed about understanding ransomware and how to protect against it.
Attend Webinars and Conferences
Webinars and conferences focused on cybersecurity are excellent opportunities for learning from experts in the field. Many organizations host events that cover the latest trends in ransomware attacks, prevention techniques, and recovery strategies. Attending these events can enhance your knowledge base and provide networking opportunities with industry peers.
For instance, I attended a cybersecurity conference last year where experts discussed the rise of double extortion ransomware attacks. The insights gained from that event helped me advise my clients on how to bolster their defenses against this evolving threat.
Implement Threat Intelligence Tools
Investing in threat intelligence tools can help businesses stay ahead of potential ransomware attacks. These tools collect data from various sources to identify emerging threats and vulnerabilities specific to your industry. By analyzing this data, organizations can proactively adjust their security measures.
I once worked with a client who implemented a threat intelligence platform that provided real-time alerts about potential vulnerabilities in their systems. This proactive approach allowed them to patch weaknesses before they could be exploited by attackers.
Conduct Regular Security Audits
Regular security audits are essential for identifying vulnerabilities within your organization’s systems. These audits should assess your current security posture, including software updates, password policies, employee training programs, and backup procedures.
In my consulting practice, I recommend conducting audits at least annually or after any significant changes in operations or technology. This practice ensures that your organization remains vigilant against evolving threats while reinforcing preventing ransomware measures.
Staying informed about ransomware threats is crucial for any business looking to enhance its cybersecurity posture. By subscribing to news sources, engaging with communities, attending webinars, implementing threat intelligence tools, and conducting regular security audits, organizations can better prepare themselves against potential attacks.
Conclusion: Safeguarding Your Business Against Ransomware
In today’s digital landscape, understanding ransomware and how to protect against it is more critical than ever. As we’ve explored throughout this article, ransomware attacks pose significant threats to businesses of all sizes, leading to operational disruptions, financial losses, and reputational damage. However, by implementing proactive measures and effective recovery strategies, organizations can significantly reduce their risk and enhance their resilience against these cyber threats.
Key Takeaways
- Understanding Ransomware: Knowing what ransomware is and how it operates is the first step in protecting your business. Familiarize yourself with the different types of ransomware and their methods of attack.
- Prevention Strategies: Employee training, regular software updates, strong password policies, and robust data backup systems are essential components of a comprehensive defense strategy. These measures are crucial for preventing ransomware attacks.
- Effective Recovery Plans: In the event of an attack, having a well-defined incident response plan can help your organization respond swiftly and effectively. Data restoration from backups and clear communication with stakeholders are vital for minimizing damage.
- Staying Informed: Continuous education is key to maintaining a strong cybersecurity posture. Subscribe to cybersecurity news, engage with professional communities, attend relevant events, and implement threat intelligence tools to stay ahead of emerging threats.
- Regular Audits: Conducting regular security audits will help you identify vulnerabilities within your systems and reinforce your defenses against potential ransomware attacks.
Final Thoughts
As an experienced entrepreneur and cybersecurity advocate, I cannot stress enough the importance of being proactive in your approach to cybersecurity. Ransomware attacks can happen to anyone, but with the right knowledge and strategies in place, you can safeguard your business against these threats.Investing time and resources into understanding ransomware and how to protect against it will pay off in the long run. By fostering a culture of security within your organization, you not only protect your data but also build trust with your clients and stakeholders.
Additional Resources
For further learning on ransomware protection and cybersecurity best practices, consider exploring the following resources:
- Cybersecurity & Infrastructure Security Agency (CISA)
- Krebs on Security Blog
- SANS Institute Cybersecurity Training
By staying informed and prepared, you can ensure that your business remains resilient in the face of evolving cyber threats.
FAQ Section
1. What is ransomware?
Ransomware is a type of malicious software that encrypts files on a victim’s computer or network, making them inaccessible until a ransom is paid to the attacker. It often spreads through phishing emails or vulnerabilities in software.
2. How can I prevent ransomware attacks?
To prevent ransomware attacks, implement the following strategies:
- Employee Training: Educate staff about recognizing phishing emails and suspicious links.
- Regular Software Updates: Keep all software and operating systems up to date to close security vulnerabilities.
- Strong Password Policies: Use complex passwords and change them regularly.
- Data Backups: Regularly back up critical data to offline or cloud storage that is not directly connected to your network.
3. What should I do if my business is attacked by ransomware?
If your business is attacked by ransomware, follow these steps:
- Isolate Infected Systems: Disconnect affected devices from the network to prevent the spread.
- Assess the Situation: Determine which files and systems are affected.
- Notify Stakeholders: Inform your IT team and key personnel about the incident.
- Engage Cybersecurity Professionals: If needed, contact experts who specialize in ransomware recovery.
4. Is paying the ransom a good idea?
Paying the ransom is generally not recommended. There’s no guarantee that paying will result in data recovery, and it may encourage further attacks on your organization or others. Evaluate your options carefully and consult with cybersecurity professionals before making a decision.
5. How often should I back up my data?
It’s advisable to back up your data regularly, ideally daily or weekly, depending on how frequently your data changes. Ensure that backups are stored securely offline or in a separate cloud environment to protect against ransomware attacks.
6. What are common signs of a ransomware infection?
Common signs of a ransomware infection include:
- Unexpected pop-ups or messages demanding payment for file access.
- Files with unusual extensions or names.
- Inability to open files that were previously accessible.
- Sudden system slowdowns or crashes.
7. Can I recover files without paying the ransom?
Yes, if you have reliable backups of your data, you can restore files without paying the ransom. Additionally, some decryption tools are available for specific types of ransomware that can help recover files without payment.
8. What role does employee training play in preventing ransomware?
Employee training is crucial in preventing ransomware because it helps staff recognize phishing attempts and avoid risky behaviors that could lead to infections. A well-informed workforce can act as a strong first line of defense against cyber threats.
9. How do I create an incident response plan for ransomware?
To create an effective incident response plan for ransomware:
- Outline immediate response steps (e.g., isolating infected systems).
- Define communication protocols for notifying stakeholders.
- Develop recovery procedures for restoring data from backups.
- Assign roles and responsibilities to team members during an incident.
10. Are there specific industries more vulnerable to ransomware attacks?
Yes, certain industries are more frequently targeted by ransomware attacks due to their valuable data and potential operational disruptions. These include healthcare, finance, education, and government sectors, where sensitive information can be particularly lucrative for attackers.



