Introduction
In our increasingly digital world, social engineering scams have become a significant threat. These scams manipulate human psychology to deceive individuals into revealing sensitive information. Understanding how to recognize social engineering tactics is crucial for everyone, from individuals to large organizations.Imagine receiving an urgent email that appears to be from your bank, warning you about suspicious activity on your account. You feel a rush of anxiety and quickly click the link, providing your login details without a second thought. This scenario is a classic example of social engineering at work.
The Importance of Recognizing Social Engineering Tactics
Recognizing social engineering tactics can save you from financial loss and identity theft. According to the FBI, losses from social engineering scams reached over $1.8 billion in 2020 alone. This staggering figure highlights how vital it is to stay informed and vigilant.
In my experience as a digital transformation expert, I’ve seen firsthand how easily people can fall victim to these scams. A colleague once received a call from someone claiming to be from IT support. The caller asked for her password to fix an “urgent issue.” Thankfully, she paused and verified the request, ultimately avoiding a potential breach.
How Social Engineering Scams Work
Social engineering scams exploit our natural tendencies to trust others and act quickly in stressful situations. The scammers often create a sense of urgency or fear, compelling victims to act without thinking. For example, they might send an email that looks legitimate but contains malicious links. These links can lead to fake websites designed to capture your personal information. By recognizing social engineering tactics, you can identify these red flags before it’s too late.
Image: Social engineering attack cycle.
As we delve deeper into this topic, we will explore what social engineering scams are, how they operate, and most importantly, how you can protect yourself from becoming a victim. By enhancing your knowledge about preventing social engineering attacks, you empower yourself and those around you.
What Are Social Engineering Scams?
Social engineering scams are sophisticated attacks that exploit human psychology rather than technical vulnerabilities. These scams rely on manipulating people into divulging confidential information or taking actions that compromise their security. Recognizing social engineering tactics is crucial in today’s digital landscape, where these attacks are becoming increasingly common and complex.
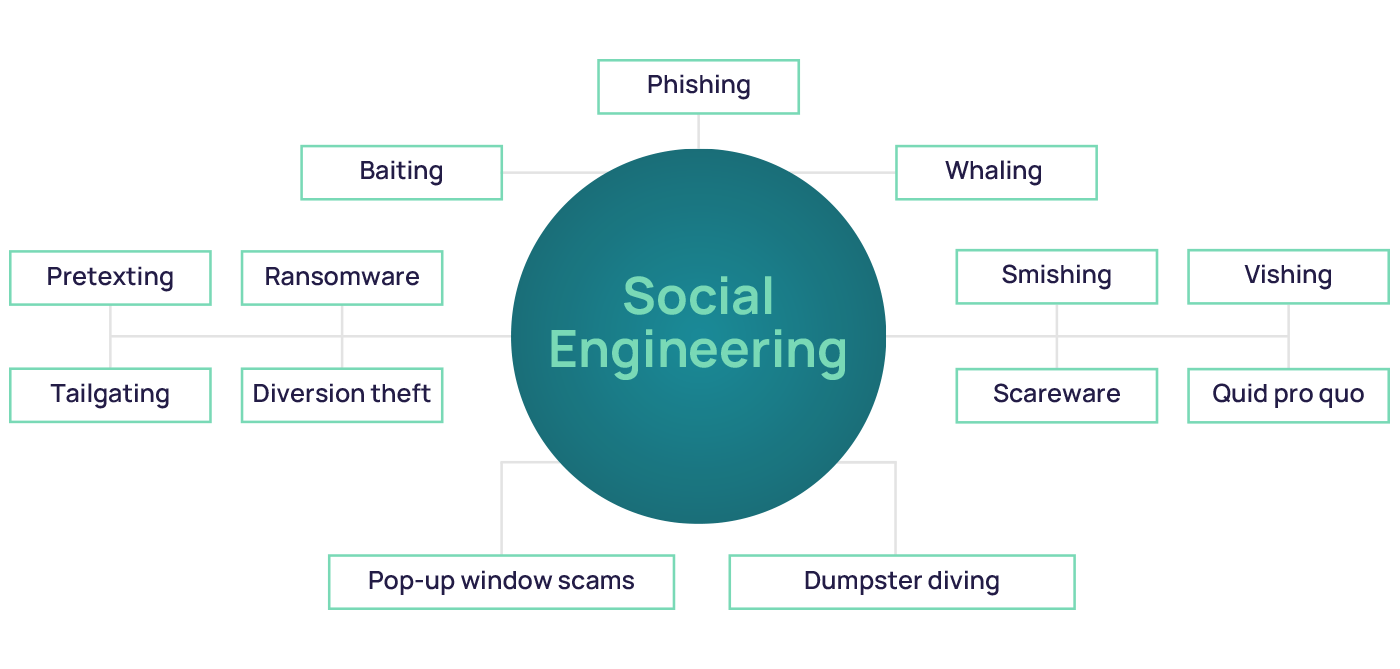
Types of Social Engineering Attacks
- Phishing: This is perhaps the most well-known form of social engineering. Phishers send emails or messages that appear to be from legitimate sources, tricking recipients into revealing sensitive information. Recognizing social engineering tactics in phishing attempts often involves spotting suspicious email addresses or urgent requests for personal data.
- Vishing (Voice Phishing): Scammers use phone calls to manipulate victims. They might impersonate bank officials or tech support to extract information. Recognizing social engineering tactics in vishing attacks requires being cautious of unsolicited calls and verifying the caller’s identity.
- Smishing (SMS Phishing): Similar to phishing but via text messages. Scammers might send links that, when clicked, install malware or lead to fake websites. Recognizing social engineering tactics in smishing involves being wary of unexpected texts asking you to click links or provide information.
- Pretexting: This involves creating a fabricated scenario to obtain information. For example, a scammer might pose as a co-worker to gain access to company data. Recognizing social engineering tactics in pretexting situations means verifying the identity of individuals requesting sensitive information, even if they seem familiar.
- Baiting: Attackers use the promise of an item or good to entice victims. This could be a free download that actually contains malware. Recognizing social engineering tactics in baiting scenarios involves being skeptical of “too good to be true” offers.
The Psychology Behind Social Engineering
Understanding the psychological principles that make these scams effective is key to recognizing social engineering tactics. Scammers often exploit:
- Authority: Impersonating figures of authority to gain trust.
- Scarcity: Creating a sense of urgency or limited availability.
- Social Proof: Using the idea that if others are doing it, it must be okay.
- Liking: Building rapport to make the victim more likely to comply.
The Importance of Awareness Training
Awareness training plays a crucial role in preventing social engineering attacks. By educating individuals about these tactics, organizations can create a human firewall against such threats. Effective awareness training programs should cover:
- Common types of social engineering attacks
- Red flags to watch out for
- Proper procedures for handling suspicious requests
- Regular updates on new and emerging threats
Real-World Example
In my consulting work, I once encountered a company that fell victim to a sophisticated pretexting attack. The scammer, posing as a new IT contractor, gained access to the building and several computers. By the time the deception was discovered, sensitive data had already been compromised. This incident underscores the importance of recognizing social engineering tactics and implementing robust awareness training programs.
Image: Social Engineering types.
Recognizing social engineering tactics is an essential skill in our digital age. By understanding the various types of attacks and the psychology behind them, we can better protect ourselves and our organizations. Remember, preventing social engineering attacks starts with awareness and vigilance. Stay informed, stay cautious, and don’t be afraid to verify.
Why Are Social Engineering Scams Effective?
Social engineering scams are alarmingly effective because they exploit fundamental aspects of human psychology. By understanding why these tactics work, you can better prepare yourself to recognize and avoid them. Recognizing social engineering tactics is not just about identifying the scams; it’s about understanding the reasons behind their success.
The Role of Trust
One of the primary reasons social engineering scams succeed is that they exploit our inherent trust in others. We are social beings, and we tend to believe what we’re told, especially when it comes from someone who appears authoritative or familiar. For instance, if you receive a call from someone claiming to be from your bank, you might instinctively trust them and provide personal information without verifying their identity. This highlights the importance of recognizing social engineering tactics that manipulate trust.
Creating a Sense of Urgency
Scammers often create a sense of urgency to push victims into making quick decisions. They might say your account will be locked unless you act immediately or that you’ve won a prize but must claim it right away. This tactic plays on our fear of loss and can lead to hasty actions without proper scrutiny. By recognizing social engineering tactics that involve urgency, you can take a step back and evaluate the situation more calmly.
Psychological Manipulation Techniques
Social engineers use various psychological techniques to manipulate their targets:
- Fear: Threatening consequences can make individuals act irrationally. For example, a scammer might claim that your account has been compromised, prompting you to provide sensitive information quickly.
- Reciprocity: If someone does something for us, we feel compelled to return the favor. Scammers might offer help or information, making victims feel obligated to comply with requests for personal data.
- Familiarity: Scammers often impersonate people we know or organizations we trust. This familiarity can cloud our judgment, making it harder to spot a scam. Recognizing social engineering tactics in these situations requires vigilance and verification.
The Impact of Technology
Technology has made it easier for scammers to execute their plans. With tools like caller ID spoofing and email phishing kits readily available, creating convincing scams is simpler than ever. This technological advancement means that even the most tech-savvy individuals need to remain aware and cautious.In my experience working with various organizations, I’ve seen how easily technology can be misused. For instance, an employee received an email that appeared to be from the CEO requesting immediate payment for a vendor invoice. The email looked legitimate, complete with company logos and email signatures. Thankfully, the employee took time to verify the request before acting, showcasing how recognizing social engineering tactics can prevent costly mistakes.
Importance of Awareness Training
To combat these effective tactics, awareness training is essential. Organizations should invest in regular training sessions that cover:
- The psychological principles behind social engineering
- Common scenarios where scams occur
- Strategies for verifying requests before taking action
By providing comprehensive awareness training, businesses can empower employees to recognize social engineering tactics effectively and reduce the risk of falling victim to scams.
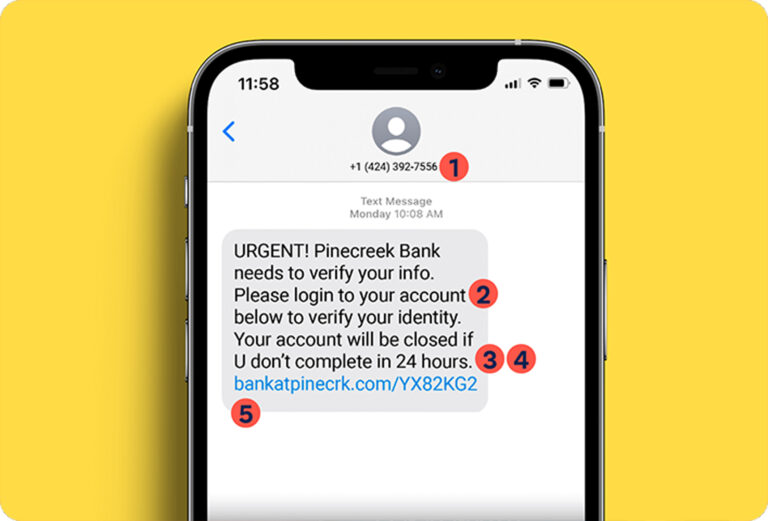
Image: Examples of urgent scam message.
Understanding why social engineering scams are effective is crucial in our fight against them. By recognizing the psychological manipulation at play and implementing strong awareness training, we can better protect ourselves and our organizations. Remember, knowledge is power when it comes to preventing social engineering attacks.
How to Recognize Social Engineering Tactics
Recognizing social engineering tactics is essential for safeguarding yourself and your organization from potential threats. Scammers are becoming increasingly sophisticated, but there are clear signs that can help you identify these deceptive practices. By learning to spot these red flags, you can significantly reduce the risk of falling victim to social engineering scams.
Key Indicators of Social Engineering Attempts
- Unusual Requests for Information
One of the most common tactics used by scammers is making unusual requests for personal or sensitive information. If someone asks for your password, account number, or social security number unexpectedly, this should raise a red flag. Always question the legitimacy of such requests. Recognizing social engineering tactics means being skeptical about unsolicited inquiries, especially when they involve sensitive data. - Sense of Urgency or Fear Tactics
Scammers often create a false sense of urgency to pressure you into acting quickly. For instance, they might claim that your account will be suspended unless you verify your information immediately. This tactic plays on fear and can lead to hasty decisions. When faced with urgent requests, take a moment to breathe and evaluate the situation. Recognizing social engineering tactics involves slowing down and asking yourself if the request seems reasonable. - Impersonation of Authority Figures
Scammers frequently impersonate authority figures, such as company executives or government officials, to gain trust. They may use official-sounding language and create fake email addresses that closely resemble legitimate ones. Always verify the identity of anyone requesting sensitive information, even if they seem familiar. This is a crucial step in recognizing social engineering tactics. - Poor Grammar and Spelling Mistakes
Many phishing emails contain spelling errors or awkward phrasing that can reveal their fraudulent nature. Legitimate organizations typically maintain high standards for communication. If you notice poor grammar or unusual language in a message, it’s a sign that it may not be genuine. - Links and Attachments
Be cautious with links and attachments in unsolicited emails or messages. Scammers often use malicious links that lead to fake websites designed to steal your information or install malware on your device. Hover over links (without clicking) to see the actual URL before proceeding. This practice is vital for recognizing social engineering tactics.
Real-Life Examples of Successful Scams
To illustrate how these tactics work in real life, let’s consider a few examples:
- A friend received an email that appeared to be from her bank, urging her to click a link to verify her account details due to “suspicious activity.” By recognizing social engineering tactics, she hesitated and called her bank directly instead of clicking the link. The bank confirmed it was a scam.
- In another case, an employee at a company received a call from someone claiming to be from IT support asking for their login credentials to perform maintenance on their computer. The employee was trained in awareness training, which helped them recognize the call as suspicious and refuse to provide any information.
The Importance of Verification
Whenever you encounter a request for sensitive information, always verify its legitimacy through independent channels. If you receive an email from your bank, don’t click on links; instead, visit their official website directly or call their customer service line.
The Role of Awareness Training
Implementing effective awareness training within organizations can empower employees to recognize these tactics more readily. Regular training sessions should cover:
- Common signs of social engineering attacks
- Procedures for verifying requests
- Best practices for handling suspicious communications
By fostering a culture of vigilance and knowledge, organizations can significantly enhance their defenses against social engineering scams.
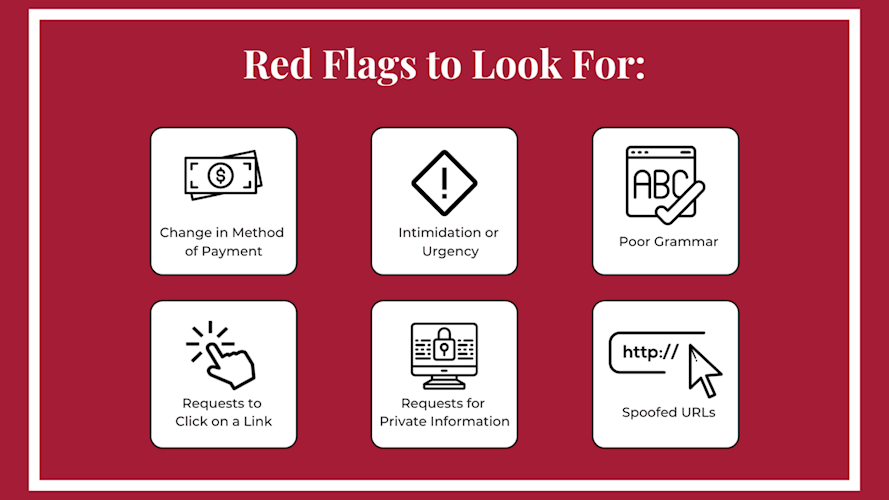
Image: A list of red flags to watch for when identifying potential scams.
Recognizing social engineering tactics is crucial in today’s digital landscape. By being aware of key indicators and implementing strong verification processes, you can protect yourself from falling victim to these scams. Remember, staying informed and participating in regular awareness training is essential for preventing social engineering attacks.
What Are the Common Techniques in Social Engineering?
Social engineering scams utilize a variety of techniques to manipulate individuals into revealing sensitive information or taking harmful actions. Understanding these common techniques is vital for recognizing social engineering tactics and protecting yourself from potential threats. By familiarizing yourself with these methods, you can become more vigilant and prepared.
1. Phishing
Phishing is one of the most prevalent techniques used in social engineering. Scammers send emails that appear to be from legitimate sources, such as banks or popular online services. These emails often contain links that lead to fake websites designed to capture your login credentials or personal information.To effectively combat phishing attempts, it’s essential to practice recognizing social engineering tactics. Look for signs like poor grammar, suspicious sender addresses, and urgent requests for action. If you receive an email claiming your account is compromised, don’t click on any links; instead, visit the official website directly.
2. Vishing (Voice Phishing)
Vishing involves phone calls where scammers impersonate legitimate organizations to extract sensitive information. They may pose as bank representatives, tech support agents, or even government officials. The goal is to instill fear or urgency, prompting victims to provide their personal details.To protect yourself from vishing attacks, always verify the caller’s identity before sharing any information. This is a crucial part of recognizing social engineering tactics. If someone calls claiming to be from your bank, hang up and call the official number listed on their website.
3. Smishing (SMS Phishing)
Smishing is similar to phishing but occurs via text messages. Scammers send texts that appear to be from legitimate sources, often containing links that lead to malicious websites or prompts to call a fake number.When you receive an unexpected text asking for personal information or urging you to click a link, remember that this could be a scam. Recognizing social engineering tactics in smishing requires skepticism and caution. Always verify the sender before responding or clicking on any links.
4. Pretexting
Pretexting involves creating a fabricated scenario to obtain information from a victim. Scammers might impersonate someone familiar, such as a co-worker or IT support staff member, to gain trust and extract sensitive data.To combat pretexting, it’s essential to verify requests for information through independent channels. If someone asks for your password or sensitive data under the guise of helping you, take a moment to assess the situation critically. This vigilance is key in recognizing social engineering tactics.
5. Baiting
Baiting involves enticing victims with the promise of something desirable—like free software or a prize—to trick them into providing personal information or downloading malware. This technique relies on curiosity and greed.To protect yourself from baiting scams, always be cautious about offers that seem too good to be true. If you receive an email or message offering free downloads or prizes, take time to research its legitimacy before acting. This approach will help you in recognizing social engineering tactics effectively.
Real-Life Example
In my work with various organizations, I encountered a case where employees received smishing texts claiming they had won gift cards. Many were tempted by the offer and clicked the links without thinking twice. Those who had undergone awareness training recognized the scam and avoided potential data breaches by not engaging with the messages.
The Importance of Awareness Training
To combat these common techniques effectively, organizations should prioritize awareness training for their employees. Training should cover:
- The different types of social engineering techniques
- How to identify red flags in communications
- Best practices for verifying requests for sensitive information
By educating individuals about these common techniques, businesses can create a culture of vigilance that helps prevent social engineering attacks.
Understanding the common techniques used in social engineering is crucial for recognizing social engineering tactics effectively. By being aware of phishing, vishing, smishing, pretexting, and baiting, you can better protect yourself and your organization from these threats. Remember that regular awareness training is essential for preventing social engineering attacks and fostering a proactive security culture.
How Can You Protect Yourself from Social Engineering Attacks?
Protecting yourself from social engineering attacks requires a proactive approach. By implementing effective strategies and remaining vigilant, you can significantly reduce the risk of falling victim to these deceptive tactics. Recognizing social engineering tactics is just the first step; knowing how to defend against them is equally important.
1. Verify Requests for Information
One of the most effective ways to protect yourself is to always verify any requests for sensitive information. Whether you receive an email, phone call, or text message, take the time to confirm the identity of the requester. If someone claims to be from your bank or a trusted organization, do not use the contact information provided in the communication. Instead, look up the official contact details and reach out directly.
This practice is crucial for recognizing social engineering tactics. For instance, if you receive an email asking for your login credentials, check with your IT department or customer service before responding.
2. Be Cautious with Links and Attachments
Always be wary of links and attachments in unsolicited communications. Scammers often use malicious links that lead to phishing sites or download malware onto your device. Before clicking on any link, hover over it to see the actual URL. If it looks suspicious, do not click it.Additionally, avoid downloading attachments from unknown sources. This simple precaution can help you avoid many social engineering traps. By practicing caution, you are actively recognizing social engineering tactics and protecting your data.
3. Use Strong Passwords and Two-Factor Authentication
Using strong passwords is essential for safeguarding your accounts against unauthorized access. Create complex passwords that include a mix of letters, numbers, and symbols. Avoid using easily guessable information like birthdays or names.Moreover, enable two-factor authentication (2FA) wherever possible.
This adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone. By adopting these practices, you can better protect yourself from social engineering attacks.
4. Educate Yourself and Others
Knowledge is a powerful tool in combating social engineering scams. Stay informed about the latest tactics used by scammers and share this knowledge with those around you. Regularly participate in awareness training programs offered by your organization or seek out online resources.By educating yourself and others about recognizing social engineering tactics, you create a more informed community that is less susceptible to scams.
5. Report Suspicious Activity
If you encounter a potential scam or suspicious activity, report it immediately. Many organizations have procedures in place for reporting phishing attempts or other fraudulent activities. By reporting these incidents, you help protect not only yourself but also others who may be targeted by the same scam.In my experience working with companies, I’ve seen how quickly information spreads when employees report suspicious emails or calls. This collective vigilance can significantly enhance an organization’s ability to defend against social engineering attacks.
Real-Life Example
I recall a situation where an employee received a call from someone claiming to be from IT support asking for their password to fix an issue with their computer. Thanks to awareness training, they recognized this as a potential vishing attack and refused to provide any information. Instead, they contacted their IT department directly using official channels to verify the request.
The Role of Awareness Training
Implementing regular awareness training sessions is vital for organizations aiming to reduce the risk of social engineering attacks. Training should cover:
- Strategies for verifying requests
- How to identify red flags in communications
- Best practices for handling sensitive information
By fostering a culture of awareness and vigilance through training, organizations can empower employees to recognize social engineering tactics effectively.
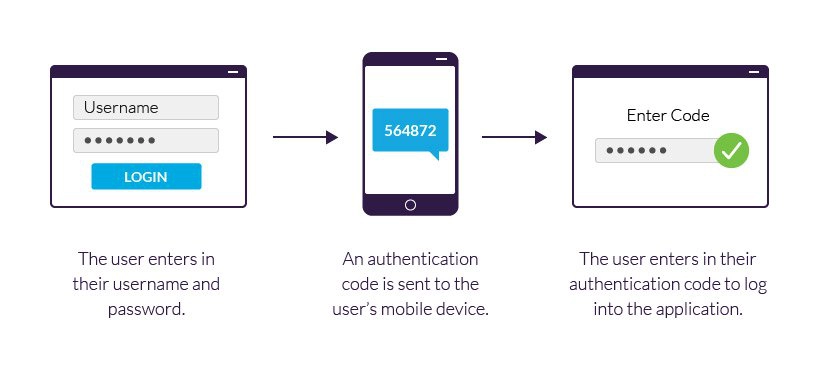
Image: 2-Factor authentication
Protecting yourself from social engineering attacks involves being proactive and informed. By verifying requests for information, being cautious with links and attachments, using strong passwords and two-factor authentication, educating yourself and others, and reporting suspicious activity, you can significantly enhance your defenses against these scams. Remember that recognizing social engineering tactics is just the beginning; taking action is what truly protects you from preventing social engineering attacks.
The Role of Awareness Training in Prevention
Awareness training is a cornerstone in the fight against social engineering scams. It equips individuals with the knowledge and skills necessary to recognize and respond to potential threats. By fostering a culture of awareness, organizations can significantly reduce their vulnerability to social engineering attacks. Understanding the importance of recognizing social engineering tactics is essential for everyone, from employees to management.
Why Awareness Training Matters
- Empowerment Through Knowledge
Awareness training empowers employees by providing them with the tools they need to identify and respond to social engineering attempts. When individuals understand the tactics used by scammers, they are more likely to remain vigilant and cautious. This knowledge helps create a proactive approach to security, making it easier for employees to spot red flags and suspicious behavior. - Building a Security Culture
Implementing regular awareness training fosters a culture of security within an organization. When employees prioritize security and understand their role in protecting sensitive information, they become active participants in preventing social engineering attacks. This collective effort enhances the overall security posture of the organization. - Reducing Human Error
Many successful social engineering attacks result from human error. Employees may inadvertently click on malicious links or provide sensitive information without verifying requests. By engaging in awareness training, organizations can reduce these mistakes by teaching employees how to think critically about requests for information and recognize potential scams.
Key Components of Effective Awareness Training
To be effective, awareness training should include several key components:
- Understanding Social Engineering Tactics
Training should cover the different types of social engineering techniques, such as phishing, vishing, smishing, pretexting, and baiting. Employees should learn how these tactics work and what signs to look for when assessing potential threats. - Real-Life Scenarios and Examples
Incorporating real-life examples of social engineering attacks can help employees relate to the material and understand its relevance. Discussing actual incidents that have occurred within the organization or industry can provide valuable insights into how scams operate. - Interactive Learning
Engaging training methods, such as interactive workshops or simulations, can enhance retention and understanding. Role-playing scenarios where employees practice recognizing and responding to social engineering attempts can be particularly effective. - Regular Updates
The landscape of social engineering is constantly evolving, with new tactics emerging regularly. To stay ahead of these threats, organizations should provide ongoing training that reflects the latest trends in social engineering scams. This ensures that employees remain informed and prepared.
Measuring Effectiveness
To gauge the effectiveness of awareness training programs, organizations should implement assessments or quizzes following training sessions. These evaluations can help determine whether employees have grasped key concepts related to recognizing social engineering tactics. Additionally, tracking incidents of social engineering attempts before and after training can provide insight into its impact on reducing vulnerabilities.
Personal Experience with Awareness Training
In my experience as a digital transformation consultant, I have seen firsthand how effective awareness training can be in preventing social engineering attacks. One organization I worked with implemented a comprehensive training program that included regular updates on emerging threats and interactive workshops. As a result, they reported a significant decrease in successful phishing attempts over six months.Employees became more confident in identifying suspicious emails and calls. They shared their knowledge with colleagues, creating a ripple effect that enhanced overall security awareness throughout the organization.

Image: Components of an effective cybersecurity awareness training program.
The role of awareness training in preventing social engineering attacks cannot be overstated. By equipping individuals with the knowledge to recognize social engineering tactics, organizations can create a culture of vigilance that significantly reduces their risk exposure. Remember that ongoing education is vital; staying informed about new threats is essential for preventing social engineering attacks effectively.
What Should You Do If You Suspect a Scam?
If you suspect that you are the target of a social engineering scam, it’s crucial to act quickly and thoughtfully. Knowing how to respond can help protect your personal information and prevent potential damage. Recognizing social engineering tactics is just the beginning; knowing the appropriate steps to take when faced with a potential scam is equally important.
1. Stay Calm and Assess the Situation
When you receive a suspicious email, phone call, or message, the first step is to remain calm. Panic can lead to hasty decisions that may compromise your security. Take a moment to assess the situation critically. Ask yourself:
- Is this request unusual?
- Does it create a sense of urgency?
- Can I verify the identity of the requester?
By staying composed and recognizing social engineering tactics, you can make more informed decisions.
2. Verify the Request
If you receive a request for sensitive information, do not respond immediately. Instead, take time to verify the legitimacy of the request. Here’s how:
- Do Not Use Provided Contact Information: If the request comes via email or phone, do not use any contact details provided in that communication. Instead, look up official contact information for the organization and reach out directly.
- Confirm with Colleagues or Superiors: If the request seems to come from someone within your organization, check with colleagues or supervisors to confirm its authenticity.
By taking these steps, you are actively practicing recognizing social engineering tactics and protecting yourself from potential scams.
3. Report the Incident
Reporting suspected scams is vital for both personal protection and organizational security. If you believe you’ve encountered a social engineering attempt:
- Notify Your IT Department: If you work for an organization, inform your IT department or security team immediately. They can take necessary actions to investigate and mitigate any potential threats.
- Report to Authorities: Many countries have government agencies dedicated to handling fraud and scams. In the U.S., for example, you can report incidents to the Federal Trade Commission (FTC) or the Internet Crime Complaint Center (IC3).
By reporting incidents, you contribute to broader efforts to combat social engineering attacks and help protect others from falling victim.
4. Change Your Passwords
If you suspect that your personal information may have been compromised, change your passwords immediately. Use strong, unique passwords for each of your accounts and consider enabling two-factor authentication (2FA) wherever possible. This step is crucial in safeguarding your accounts against unauthorized access.
In my experience working with various organizations, I’ve seen how quickly compromised credentials can lead to further attacks if not addressed promptly. By changing passwords and implementing security measures, you can significantly reduce your risk.
5. Monitor Your Accounts
After suspecting a scam, it’s essential to monitor your financial accounts and online profiles closely. Look for any unauthorized transactions or unusual activity. If you notice anything suspicious, report it to your bank or service provider immediately.Regularly reviewing your accounts helps you catch potential issues early on and reinforces your ability to recognize social engineering tactics in the future.
Real-Life Example
I once assisted a client who received an email that appeared to be from their accounting department requesting sensitive financial information. Thanks to their training in awareness training, they recognized this as a potential phishing attempt. They took immediate action by verifying the request with their supervisor before responding. This quick verification process helped them avoid sharing sensitive data with scammers.
The Importance of Awareness Training
To effectively respond when faced with a suspected scam, ongoing awareness training is essential. Organizations should ensure that employees are familiar with procedures for reporting suspicious activity and know how to verify requests for information.Training should cover:
- Steps to take when encountering suspicious communications
- How to report incidents internally and externally
- Best practices for securing personal information
By implementing robust awareness training, organizations can empower employees to respond effectively when they suspect a scam.
Knowing what to do if you suspect a scam is crucial for protecting yourself and your organization from social engineering attacks. By staying calm, verifying requests, reporting incidents, changing passwords, and monitoring accounts, you can safeguard your personal information effectively. Remember that being proactive in recognizing social engineering tactics is key in preventing potential damage from these scams.
Case Studies: Notable Social Engineering Scams
Examining real-life case studies of social engineering scams provides valuable insights into how these tactics operate and the consequences of falling victim to them. By analyzing these incidents, we can better understand the importance of recognizing social engineering tactics and implementing effective preventive measures. Here are a few notable cases that highlight the effectiveness of social engineering and the lessons learned.
1. The Google and Facebook Scam
Between 2013 and 2015, a Lithuanian man managed to defraud tech giants Google and Facebook out of over $100 million through a sophisticated social engineering scheme. The scammer impersonated a legitimate hardware company, using fake invoices and email addresses that closely resembled those of the actual business.
Key Takeaways:
- Recognizing social engineering tactics is crucial, even for large organizations. Despite their resources, both companies fell victim to the scam because they did not verify the authenticity of the invoices.
- This incident underscores the importance of implementing strict verification processes for financial transactions, especially when dealing with large sums.
2. The Target Data Breach
In 2013, hackers gained access to Target’s systems and stole credit card information from over 40 million customers. The breach began with a phishing email sent to a third-party vendor. Once the hackers obtained credentials from this vendor, they infiltrated Target’s network.
Key Takeaways:
- This case highlights how recognizing social engineering tactics can prevent breaches. Target’s reliance on third-party vendors without adequate security measures created vulnerabilities.
- Organizations should ensure that all partners undergo rigorous security assessments and provide awareness training to their employees about potential phishing threats.
3. The Ubiquiti Networks Incident
In 2015, Ubiquiti Networks, a tech company, lost $46.7 million due to a business email compromise (BEC) scam. Scammers impersonated company executives and instructed employees to transfer funds to overseas accounts. The employees acted quickly, believing they were following legitimate orders.
Key Takeaways:
- This incident demonstrates how critical it is for employees to be trained in recognizing social engineering tactics like BEC scams.
- Organizations should implement multi-step verification processes for large transactions, including direct confirmation with executives before executing fund transfers.
4. The Deepfake Scam
In 2020, a UK-based energy firm was scammed out of €220,000 (approximately $243,000) by fraudsters using deepfake technology. The scammers created a voice clone of the CEO and instructed an employee to transfer funds to a supplier in Hungary. The employee believed they were following legitimate orders.
Key Takeaways:
- This case emphasizes the need for heightened awareness regarding emerging technologies used in social engineering attacks. Recognizing social engineering tactics now includes being cautious about voice impersonation.
- Organizations should adopt comprehensive training programs that cover advanced threats like deepfakes and ensure employees know how to verify requests through multiple channels.
Lessons Learned from These Cases
These notable cases illustrate several key lessons for both individuals and organizations:
- Verification is Essential: Always verify requests for sensitive information or financial transactions through independent channels.
- Implement Strong Security Policies: Establish clear protocols for handling sensitive data and financial transactions.
- Continuous Awareness Training: Regularly update training programs to include new threats and ensure employees are equipped to recognize social engineering tactics effectively.
- Encourage Reporting: Foster an environment where employees feel comfortable reporting suspicious activity without fear of repercussions.
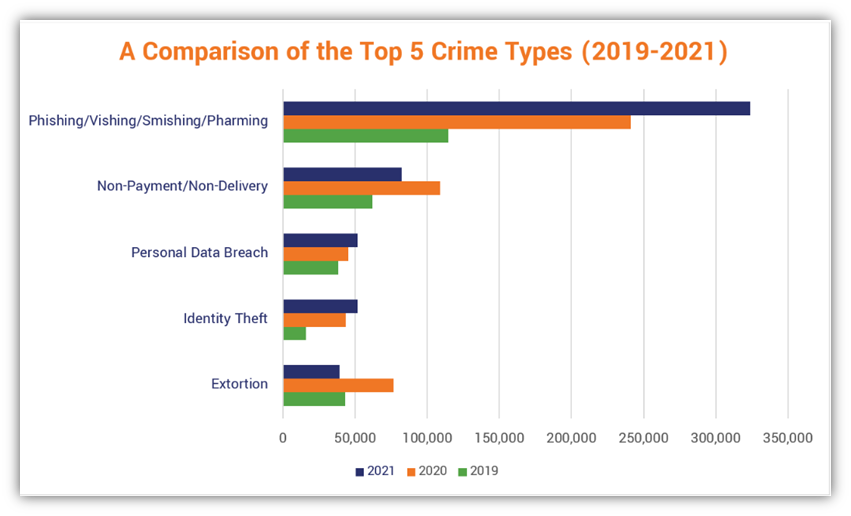
Image: A comparison of top 5 cyber crimes.
Studying notable social engineering scams helps us understand how these tactics can lead to significant financial losses and reputational damage. By learning from these incidents, we can enhance our ability to recognize social engineering tactics and implement effective strategies for prevention. Remember that vigilance, verification, and ongoing awareness training are key components in safeguarding against these evolving threats.
Empowering Yourself Against Scams
In a world where social engineering scams are increasingly sophisticated and prevalent, empowering yourself with knowledge and tools is essential for protection. Understanding how to recognize social engineering tactics can significantly reduce your risk of falling victim to these deceptive practices. This section will summarize key strategies and provide actionable steps to help you stay safe.
1. Educate Yourself Continuously
The first step in empowering yourself against scams is to commit to ongoing education. Stay informed about the latest trends in social engineering and cybersecurity. Follow reputable sources, such as cybersecurity blogs, news outlets, and government websites that provide updates on emerging threats.
- Recognizing social engineering tactics requires awareness of the various methods scammers use. Regularly reviewing educational materials will help you stay ahead of potential threats.
- Participate in webinars and workshops focused on cybersecurity awareness. These sessions can provide valuable insights into current scams and effective prevention strategies.
2. Practice Vigilance
Always be vigilant when it comes to your personal information. Whether you’re online or offline, take the time to assess any requests for sensitive data critically. Here are some tips for maintaining vigilance:
- Question Unsolicited Requests: If you receive an unexpected email or call asking for personal information, don’t act immediately. Take a moment to verify the request through official channels.
- Be Wary of Urgency: Scammers often create a sense of urgency to pressure you into making quick decisions. If someone claims you must act now, pause and evaluate the situation carefully.
By practicing vigilance, you enhance your ability to recognize social engineering tactics before they can cause harm.
3. Implement Strong Security Practices
Adopting strong security practices is crucial for protecting yourself from social engineering attacks:
- Use Strong Passwords: Create complex passwords that include a mix of letters, numbers, and symbols. Avoid using easily guessable information like birthdays or names.
- Enable Two-Factor Authentication (2FA): Whenever possible, activate 2FA on your accounts. This adds an extra layer of security by requiring a second form of verification.
- Regularly Update Software: Keep your operating system, applications, and antivirus software up to date to protect against vulnerabilities that scammers may exploit.
These practices not only strengthen your defenses but also help you feel more confident in your ability to prevent social engineering attacks.
4. Share Knowledge with Others
Empower those around you by sharing what you’ve learned about social engineering scams. Discussing these topics with friends, family, or colleagues can help raise awareness and create a more informed community.
- Encourage open conversations about cybersecurity and share resources that have helped you understand recognizing social engineering tactics.
- If you work in an organization, advocate for regular awareness training sessions that cover the latest threats and best practices for prevention.
By fostering a culture of knowledge-sharing, you contribute to a safer environment for everyone.
5. Know When to Seek Help
If you suspect that you have been targeted by a scam or have fallen victim to one, know when to seek help:
- Report Incidents: If you receive suspicious communications or believe your personal information has been compromised, report it immediately to your IT department (if applicable) or relevant authorities.
- Seek Professional Guidance: If you’re unsure about how to handle a potential scam or need assistance with securing your accounts, consider consulting a cybersecurity professional.
Knowing when to seek help is crucial in mitigating potential damage from social engineering attacks.
Empowering yourself against scams is an ongoing process that involves education, vigilance, strong security practices, knowledge-sharing, and knowing when to seek help. By committing to these strategies and continuously working on recognizing social engineering tactics, you can significantly reduce your risk of falling victim to these deceptive schemes. Remember that awareness is your first line of defense in preventing social engineering attacks. Stay informed, stay cautious, and take proactive steps to protect yourself and those around you.
FAQ Section
1. What is social engineering?
Social engineering is a manipulation technique that exploits human psychology to trick individuals into divulging confidential information or performing actions that compromise security. Scammers often use social engineering tactics to gain access to sensitive data, such as passwords or financial information.
2. How can I identify a phishing email?
To identify a phishing email, look for several red flags:
- Suspicious Sender: Check the sender’s email address for slight misspellings or unusual domains.
- Urgent Language: Phishing emails often create a sense of urgency, prompting you to act quickly.
- Generic Greetings: Legitimate organizations usually address you by name, while phishing emails may use generic terms like “Dear Customer.”
- Poor Grammar and Spelling: Many phishing emails contain grammatical errors or awkward phrasing.
3. What should I do if I receive a suspicious call?
If you receive a suspicious call:
- Do Not Share Personal Information: Never provide sensitive information over the phone unless you are certain of the caller’s identity.
- Hang Up and Verify: If the caller claims to be from a legitimate organization, hang up and call back using official contact information.
- Report the Call: Inform your IT department or local authorities about the suspicious call.
4. Are social engineering scams only digital?
No, social engineering scams can occur both digitally and in person. While many scams take place through emails, phone calls, or text messages (phishing, vishing, and smishing), they can also involve face-to-face interactions where scammers impersonate trusted individuals to gain access to sensitive information.
5. How does AI contribute to social engineering scams?
AI can enhance social engineering scams by enabling scammers to create more convincing phishing emails and deepfake audio or video impersonations. With advanced technology, scammers can simulate voices or appearances of trusted individuals, making it more challenging for victims to recognize fraudulent attempts.
6. What are the signs of vishing?
Signs of vishing include:
- Caller ID Spoofing: The caller’s number may appear legitimate but is actually fake.
- Urgent Requests: The caller may pressure you to provide personal information quickly.
- Unusual Questions: If the caller asks for sensitive information that you wouldn’t normally share over the phone, it could be a scam.
7. How can businesses train employees on recognizing scams?
Businesses can train employees on recognizing scams by:
- Implementing Regular Awareness Training: Conduct workshops and training sessions focused on identifying social engineering tactics.
- Providing Real-Life Examples: Share case studies of actual scams within the industry to illustrate potential threats.
- Encouraging Reporting: Create an environment where employees feel comfortable reporting suspicious activity without fear of repercussions.
8. What legal actions can I take against scammers?
If you fall victim to a scam, you can take several legal actions:
- Report to Authorities: File a complaint with local law enforcement or relevant government agencies (e.g., FTC in the U.S.).
- Notify Your Bank or Financial Institution: If financial information was compromised, inform your bank immediately.
- Consider Legal Counsel: If significant losses occurred due to fraud, consulting with a legal professional may be beneficial.
9. Can social engineering affect my personal life?
Yes, social engineering can impact your personal life significantly. Scammers may target individuals through various channels, leading to identity theft, financial loss, and emotional distress. Being aware of social engineering tactics is essential for protecting your personal information.
10. What resources are available for further learning about social engineering?
Several resources are available for further learning about social engineering:
- Online Courses: Platforms like Coursera and Udemy offer courses on cybersecurity and social engineering.
- Books and Articles: Numerous books focus on cybersecurity awareness and social engineering tactics.
- Webinars and Workshops: Many organizations host webinars that discuss current trends in cybersecurity and prevention strategies.