Introduction
In recent years, the shift to remote work has transformed how we approach our professional lives. With the rise of digital technology, more individuals and organizations are embracing the flexibility and convenience of working from home. However, this transition has also brought significant challenges, particularly when it comes to securing remote work environments.
As remote work becomes the norm, cybersecurity threats have evolved and intensified. Cybercriminals are increasingly targeting remote workers, exploiting vulnerabilities in home networks and personal devices. This makes it essential for both employees and employers to prioritize home office cybersecurity.
In this comprehensive guide, we will explore essential tips and strategies for maintaining a secure remote work environment. From understanding the risks associated with remote work to implementing effective security measures, this article aims to equip you with the knowledge needed to protect your data and ensure a safe working experience. We will cover a range of topics, including:
- The common risks associated with remote work
- Best practices for securing your home office
- Essential tools for securing remote access
- The importance of employee training and ongoing education
- Future trends in remote work security
By the end of this article, you will have a solid understanding of how to effectively secure your remote work environment, enabling you to focus on productivity without compromising your data’s safety. Let’s dive in!
What Are the Risks of Remote Work?
As someone who has navigated the waters of remote work for several years, I can tell you that while the flexibility is fantastic, it comes with its own set of challenges—especially when it comes to securing remote work environments. Understanding these risks is the first step in protecting yourself and your data.
Increased Exposure to Cyber Threats
When you work from home, your exposure to cyber threats increases significantly. In a traditional office, there are layers of security in place—firewalls, IT support, and controlled access to sensitive information. However, at home, many of these protections are absent. For example, I once worked with a team member who connected to public Wi-Fi at a coffee shop. Within days, their laptop was compromised. This incident highlighted how quickly vulnerabilities can arise when securing remote access is not prioritized.
Vulnerability of Home Networks and Devices
Your home network may not be as secure as you think. Many people use default passwords for their routers or fail to update their firmware regularly. These oversights can lead to unauthorized access. I remember setting up my home office and realizing my router’s password was still the factory setting! After changing it and enabling WPA3 encryption, I felt a lot safer.
Additionally, personal devices often lack the robust security measures found in corporate environments. If you’re using your personal laptop for work without proper antivirus software or firewalls, you’re leaving yourself open to malware attacks. This is why home office cybersecurity should be a top priority for anyone working remotely.
Common Remote Work Security Risks
Here are some common security risks you should be aware of:
- Phishing Attacks: These are scams where attackers impersonate legitimate organizations to steal sensitive information. I’ve received countless emails that looked official but were actually traps. Always double-check email addresses and avoid clicking on suspicious links.
- Malware: This includes viruses and ransomware that can cripple your device or steal your data. Installing antivirus software is crucial for securing remote work environments effectively.
- Unsecured Wi-Fi Networks: Connecting to public Wi-Fi without a VPN can expose your data to hackers lurking on the same network. I learned this the hard way when I noticed strange activity on my accounts after using an unsecured network.
- Weak Passwords: Using simple or repeated passwords across multiple accounts makes it easy for attackers to gain access. A strong password strategy is essential for securing remote access.
- Lack of Updates: Failing to update software can leave vulnerabilities open for exploitation. Regularly updating your operating systems and applications is a simple yet effective way to enhance your home office cybersecurity.
Fully understanding the risks associated with remote work is crucial for anyone looking to maintain a secure environment. By being aware of potential threats—like phishing attacks, unsecured networks, and weak passwords—you can take proactive steps toward securing remote work environments effectively.

How Can You Secure Your Home Office Cybersecurity?
Securing your home office is not just about locking the door; it’s about creating a fortress around your digital workspace. As someone who has faced the challenges of securing remote work environments, I can share some practical tips that will help you enhance your home office cybersecurity.
Importance of a Secure Home Network
First things first: your home network is the backbone of your remote work setup. If it’s not secure, everything else is at risk. When I first transitioned to remote work, I didn’t think much about my home network. It wasn’t until I read about how easily hackers could infiltrate unsecured networks that I realized I needed to take action.
- Change Default Passwords: Many people overlook this simple step. Your router likely comes with a default password that’s easy for hackers to guess. Change it to something strong and unique. This is one of the easiest ways to bolster your home office cybersecurity.
- Enable WPA3 Encryption: If your router supports it, enable WPA3 encryption. This adds an extra layer of security that makes it much harder for unauthorized users to access your network. I upgraded my router specifically for this feature, and it gave me peace of mind.
- Guest Network: If you have visitors or family members who need Wi-Fi access, set up a guest network. This keeps your main network—and all the devices connected to it—more secure.
Recommendations for Securing Wi-Fi Connections
Securing your Wi-Fi connection is crucial when it comes to securing remote work environments. Here are some additional steps you can take:
- Use a VPN: A Virtual Private Network (VPN) encrypts your internet connection, making it much harder for anyone to intercept your data. I started using a VPN after realizing how vulnerable my information was on public networks. It’s a game-changer for securing remote access.

- Regularly Update Your Router’s Firmware: Manufacturers often release updates to fix security vulnerabilities in their devices. Make it a habit to check for updates regularly, as this is vital for maintaining strong home office cybersecurity.
Use of Firewalls and Intrusion Detection Systems
Firewalls act as barriers between your devices and potential threats from the internet. They monitor incoming and outgoing traffic and can block suspicious activity.
- Enable Built-In Firewalls: Most operating systems come with built-in firewalls that you should enable immediately. This adds another layer of protection when securing remote work environments.
- Consider Intrusion Detection Systems (IDS): For those who want an extra layer of security, IDS can monitor network traffic for suspicious activity and alert you if something seems off. While I haven’t implemented one myself yet, I’ve heard great things from colleagues who have.
Regular Software Updates and Patch Management
Keeping your software updated is essential for maintaining home office cybersecurity. Outdated software can have vulnerabilities that hackers exploit.
- Automatic Updates: Enable automatic updates on all devices whenever possible. This ensures you’re always running the latest versions with security patches applied.
- Third-Party Applications: Don’t forget about third-party applications; they also require regular updates. I once neglected an outdated app that became a gateway for malware into my system. Now, I make it a point to check all software regularly.
Securing your home office isn’t just about having the right tools; it’s about creating a comprehensive strategy for securing remote work environments effectively. By focusing on securing your home network, utilizing VPNs, enabling firewalls, and keeping software updated, you can significantly enhance your home office cybersecurity.
What Tools Are Essential for Securing Remote Access?
In the world of remote work, securing remote access is critical to maintaining the integrity of your data and protecting your organization from cyber threats. As someone who has navigated the complexities of securing remote work environments, I can share valuable insights on the essential tools you need to enhance your home office cybersecurity.
Virtual Private Networks (VPNs)
A Virtual Private Network (VPN) is one of the most effective tools for securing remote access. It creates a secure tunnel between your device and the internet, encrypting your data and masking your IP address.
- Why Use a VPN?: When I first started working remotely, I often connected to public Wi-Fi networks—like those in coffee shops or airports—without a second thought. After learning about the risks, I invested in a reliable VPN service. This tool not only protects my data but also allows me to access resources securely as if I were in the office.
- Choosing a VPN: Not all VPNs are created equal. Look for one that offers strong encryption, a no-logs policy, and multiple server locations. I personally use a VPN that has a user-friendly interface and excellent customer support, which makes it easier to troubleshoot any issues.
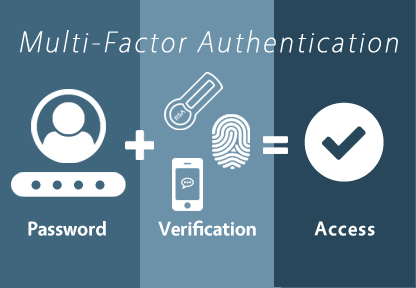
Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) adds an additional layer of security by requiring more than just a password to access accounts. This is crucial for securing remote work environments.
- How MFA Works: With MFA, you might enter your password and then receive a text message with a code you must also enter to gain access. This means that even if someone steals your password, they still can’t get into your accounts without that second factor.
- Implementing MFA: Many platforms now offer MFA options, including email providers and project management tools. I’ve enabled it on all my accounts, and it gives me peace of mind knowing that my sensitive information is better protected.
Secure Remote Desktop Protocols
Secure Remote Desktop Protocols (RDP) allow you to connect to another computer over the internet securely. This is especially useful for accessing work computers from home.
- Using RDP Safely: When I first started using RDP, I didn’t realize how important it was to secure it properly. Make sure to change default ports and use strong passwords when setting up RDP connections.
- Limit Access: Only allow specific IP addresses to connect via RDP if possible. This minimizes the risk of unauthorized access and is an essential step in securing remote access.
Endpoint Protection Software
Endpoint protection software is crucial for safeguarding all devices connected to your network. This includes computers, tablets, and smartphones used for work.
- Why You Need It: Many people underestimate the importance of endpoint protection until it’s too late. I once had a colleague who didn’t have any protection on their device, and they ended up with ransomware that locked them out of critical files.
- Choosing Endpoint Protection: Look for software that provides real-time threat detection, malware protection, and regular updates. My go-to solution has been incredibly effective at catching threats before they become serious issues.
Secure File-Sharing Practices
When working remotely, sharing files securely is vital for maintaining home office cybersecurity.
- Use Encrypted File Sharing Services: Avoid sending sensitive documents via email unless absolutely necessary. Instead, use encrypted services like Google Drive or Dropbox with added security features.
- Password-Protect Files: If you must share files via email, consider password-protecting them first. This extra step can help prevent unauthorized access even if the email gets intercepted.
Equipping yourself with the right tools is essential for effectively securing remote access in today’s digital landscape. By utilizing VPNs, enabling Multi-Factor Authentication (MFA), using Secure Remote Desktop Protocols (RDP), implementing endpoint protection software, and practicing secure file-sharing methods, you can significantly enhance your home office cybersecurity.
How to Train Employees on Cybersecurity Best Practices?
Training employees on cybersecurity best practices is essential for securing remote work environments. Even the best tools and technologies can only do so much if the people using them aren’t aware of potential threats. As someone who has led training sessions in various organizations, I can share effective strategies that will help enhance your home office cybersecurity.
Importance of Ongoing Cybersecurity Education
Cyber threats are constantly evolving, and so should your training programs. Regular education ensures that employees are aware of the latest risks and how to mitigate them.
- Why Training Matters: I’ve seen firsthand how a lack of training can lead to costly mistakes. In one instance, a colleague fell for a phishing scam because they hadn’t been trained to recognize suspicious emails. This incident not only compromised their data but also put the entire organization at risk.
- Continuous Learning: Consider implementing a continuous learning program where employees receive regular updates on cybersecurity trends and threats. This could include monthly newsletters, webinars, or even short quizzes to reinforce learning.
Topics to Cover in Training Sessions
When planning your cybersecurity training, it’s essential to cover key topics that are relevant to securing remote work environments.
- Recognizing Phishing Attempts: Teach employees how to identify phishing emails and suspicious links. Use real-life examples from recent scams to make the training relatable. I often share anecdotes from my own experiences to illustrate these points.
- Password Management: Stress the importance of strong passwords and using password managers. I’ve found that many people still use simple passwords or repeat them across different accounts, which is a huge risk for securing remote access.
- Safe Browsing Practices: Educate employees on safe browsing habits, such as avoiding untrusted websites and being cautious with downloads. I once downloaded an application from an unverified source, which led to malware on my device—something I now make sure to warn others about.
- Data Protection Policies: Ensure that employees understand your organization’s data protection policies, including how to handle sensitive information securely. This is crucial for maintaining home office cybersecurity.
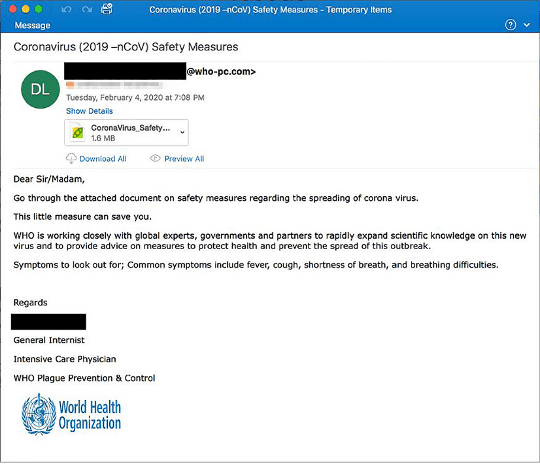
Regular Updates and Simulations for Practical Knowledge
Knowledge retention is key in cybersecurity training. Regular updates and practical simulations can help reinforce what employees learn.
- Phishing Simulations: Conduct simulated phishing attacks to test employees’ responses. This not only raises awareness but also helps identify areas where further training is needed. After running a simulation in my last organization, we were able to pinpoint several individuals who needed additional support.
- Feedback Mechanism: Establish a feedback mechanism where employees can report suspicious emails or activities without fear of repercussions. This encourages a culture of vigilance and accountability in securing remote work environments.
Encouraging a Culture of Security Awareness
Creating a culture of security awareness goes beyond formal training sessions; it requires ongoing engagement from everyone in the organization.
- Lead by Example: As a leader, demonstrate good cybersecurity practices yourself. Share your experiences and challenges openly; this humanizes the issue and encourages others to take it seriously.
- Recognition Programs: Consider implementing recognition programs for employees who demonstrate exemplary cybersecurity practices. A little acknowledgment can go a long way in motivating others to follow suit.
Training employees on cybersecurity best practices is crucial for effectively securing remote work environments. By focusing on ongoing education, covering relevant topics, conducting practical simulations, and fostering a culture of security awareness, you can significantly enhance your organization’s overall home office cybersecurity posture.
What Are the Best Practices for Device Security?
When it comes to securing remote work environments, device security is a critical component that should not be overlooked. Every device connected to your network can potentially be a gateway for cyber threats. As someone who has faced various challenges in this area, I can share effective best practices that will help you enhance your home office cybersecurity.
Endpoint Protection Software
One of the first steps in securing devices is to install endpoint protection software. This software acts as a shield against various cyber threats.
- Why You Need It: I’ve learned the hard way that relying solely on built-in security features isn’t enough. A few years ago, I neglected to install dedicated antivirus software on my laptop. It didn’t take long before I encountered malware that disrupted my work and compromised sensitive files.
- Choosing the Right Software: Look for endpoint protection that offers real-time threat detection, malware protection, and regular updates. My current solution has proven effective at catching threats before they escalate, and it provides peace of mind knowing my devices are monitored continuously.
Regular Software Updates and Patch Management
Keeping your software updated is crucial for maintaining home office cybersecurity. Outdated software can leave vulnerabilities that hackers can exploit.
- Automatic Updates: Enable automatic updates on all devices whenever possible. This ensures you’re always running the latest versions with security patches applied. I set my devices to update overnight so that I don’t have to worry about interruptions during work hours.
- Third-Party Applications: Don’t forget about third-party applications; they also require regular updates. I’ve made it a habit to check all software periodically, especially after hearing about vulnerabilities in popular applications.
Strong Password Policies
Using strong passwords is one of the simplest yet most effective ways to secure your devices.
- Password Complexity: Encourage employees to create complex passwords that include a mix of letters, numbers, and symbols. I often share my own password creation strategies during training sessions—like using phrases or acronyms—to make it easier for others to remember strong passwords.
- Password Managers: Consider recommending password managers to help employees store and generate strong passwords securely. After starting to use one myself, I found it much easier to maintain unique passwords across different accounts, significantly improving my securing remote access efforts.
Device Encryption
Encrypting your devices adds an extra layer of security by making your data unreadable without the correct decryption key.
- Why Encrypt?: If your device is lost or stolen, encryption ensures that sensitive data remains protected from unauthorized access. I once misplaced my laptop at a conference, but because it was encrypted, I felt relieved knowing my data was safe.
- How to Encrypt: Most operating systems offer built-in encryption options (like BitLocker for Windows or FileVault for macOS). Make sure these features are enabled on all devices used for work.
Secure Remote Access
When accessing work systems remotely, ensuring secure connections is vital for maintaining home office cybersecurity.
- Use Secure Connections: Always connect to secure networks when accessing sensitive information or company resources. Avoid using public Wi-Fi without a VPN; I learned this lesson after experiencing slow speeds and potential security risks while working from a café.
- Limit Remote Access: Only allow remote access to essential personnel and regularly review permissions. This helps minimize risks associated with unauthorized access and is an important step in securing remote access.
Implementing best practices for device security is essential for effectively securing remote work environments. By utilizing endpoint protection software, keeping software updated, enforcing strong password policies, enabling device encryption, and ensuring secure remote access, you can significantly enhance your overall home office cybersecurity posture.
How to Manage Data Safely While Working Remotely?
Managing data safely while working remotely is crucial for maintaining the integrity of your information and ensuring compliance with regulations. As someone who has dealt with data management challenges in remote environments, I can share effective strategies that will help you enhance your home office cybersecurity while securing remote work environments.
Importance of Data Management
Data management is not just about storage; it’s about protecting sensitive information from unauthorized access and breaches. When I first started working remotely, I underestimated the importance of having a solid data management plan. It wasn’t until I faced a near-miss with a data breach that I realized how critical it was to prioritize this aspect of securing remote work environments.
- Identify Sensitive Data: The first step in managing data safely is to identify what constitutes sensitive information within your organization. This could include personal identifiable information (PII), financial records, or proprietary business data. Knowing what needs protection is essential for effective home office cybersecurity.
- Data Classification: Implement a data classification system to categorize information based on its sensitivity. This will help you determine the appropriate security measures needed for each type of data. For example, I once worked with a team that classified their data into three categories: public, internal, and confidential. This made it easier to apply specific security protocols tailored to each category.
Data Encryption
Encrypting your data is one of the most effective ways to protect it from unauthorized access. Encryption transforms your data into unreadable code that can only be deciphered with the correct key.
- Why Encrypt Your Data?: If your device is lost or stolen, encryption ensures that sensitive data remains protected. I learned this lesson the hard way when a colleague’s unencrypted laptop was stolen from their car, leading to a significant breach of sensitive client information.
- How to Encrypt Data: Most operating systems and cloud storage services offer built-in encryption options. For instance, services like Google Drive and Dropbox provide encryption for files stored in the cloud, which is vital for securing remote work environments.
Secure File Sharing Practices
When working remotely, sharing files securely is crucial for maintaining home office cybersecurity.
- Use Encrypted File Sharing Services: Avoid sending sensitive documents via email unless absolutely necessary. Instead, use encrypted services like Google Drive or OneDrive with added security features. I’ve found that using these platforms not only keeps my files safe but also allows for easy collaboration with team members.
- Password-Protect Files: If you must share files via email, consider password-protecting them first. This extra step can help prevent unauthorized access even if the email gets intercepted. It’s a simple yet effective measure for enhancing your data management practices while securing remote work environments.
Implementing Data Loss Prevention (DLP) Tools
Data Loss Prevention (DLP) tools are designed to monitor and control data transfers within and outside your organization.
- Why Use DLP Tools?: DLP tools help prevent sensitive information from being shared inappropriately or leaked outside the organization. In my experience, implementing DLP tools has been invaluable in ensuring compliance with industry regulations and safeguarding sensitive data.
- Choosing DLP Solutions: Look for DLP solutions that offer real-time monitoring and alerts for suspicious activities involving sensitive data. These tools can significantly enhance your ability to manage data safely while working remotely and are essential for effectively securing remote work environments.
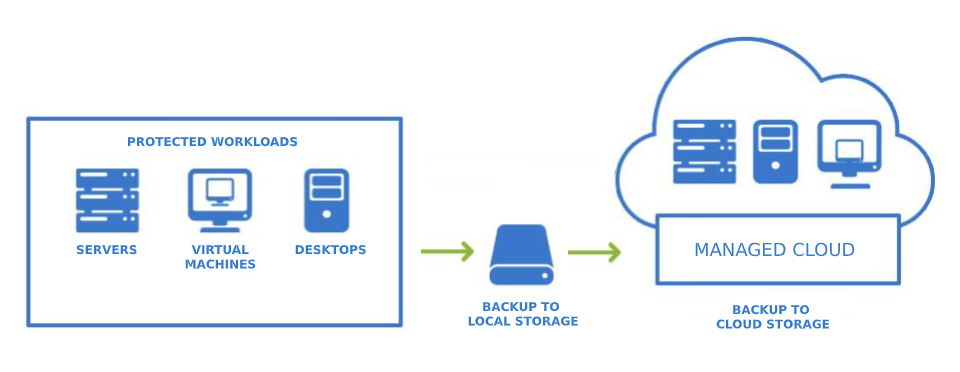
Regular Backups
Regularly backing up your data is another crucial aspect of safe data management.
- Why Backup Matters: In case of hardware failure or cyber incidents like ransomware attacks, having backups ensures that you don’t lose critical information. I’ve had my fair share of close calls where backups saved me from losing hours of work due to unexpected issues.
- Backup Solutions: Use both local and cloud-based backup solutions for redundancy. I personally use an external hard drive for local backups and a cloud service for off-site backups, giving me peace of mind knowing my data is secure in multiple locations.
Effectively managing data while working remotely is essential for maintaining robust home office cybersecurity and ensuring compliance with regulations surrounding sensitive information. By prioritizing data identification and classification, implementing encryption, utilizing secure file-sharing practices, employing DLP tools, and conducting regular backups, you can significantly enhance your efforts in securing remote work environments.
What Policies Should Organizations Implement?
Implementing robust policies is essential for securing remote work environments effectively. These policies provide a framework that guides employees in maintaining home office cybersecurity and helps organizations mitigate risks associated with remote work. Drawing from my experience as a tech-savvy entrepreneur, I can share key policies that every organization should consider.
Creating Guidelines for Acceptable Remote Work Practices
Establishing clear guidelines for acceptable remote work practices is crucial for ensuring that employees understand their responsibilities regarding data security.
- Define Remote Work Expectations: Clearly outline what is expected from employees while working remotely. This includes guidelines on how to handle sensitive information and the importance of using secure networks. I once worked with a company that provided a detailed handbook on remote work practices, which significantly improved compliance among employees.
- Regular Updates: As threats evolve, it’s essential to regularly update these guidelines to address new risks. Make it a point to review and revise your policies at least once a year or whenever significant changes occur in the threat landscape.
Role-Based Access Control (RBAC)
Implementing Role-Based Access Control (RBAC) is an effective way to limit access to sensitive information based on an employee’s role within the organization.
- Why Use RBAC?: RBAC ensures that employees only have access to the data necessary for their job functions, reducing the risk of unauthorized access. I’ve seen organizations suffer breaches simply because too many employees had access to sensitive data they didn’t need.
- Regular Reviews: It’s important to regularly review access permissions and adjust them as roles change within the organization. This proactive approach is vital for securing remote work environments and maintaining home office cybersecurity.
Incident Response Plan
Having an incident response plan in place prepares your organization to act swiftly in the event of a security breach.
- Why an Incident Response Plan Matters: An incident response plan outlines the steps to take when a security incident occurs, minimizing damage and recovery time. I once experienced a minor breach where having a plan in place allowed us to contain the issue quickly and effectively.
- Regular Drills: Conduct regular drills to ensure that all employees know their roles in the event of a security incident. This not only prepares them but also fosters a culture of vigilance around securing remote work environments.
Data Protection Policies
Establishing clear data protection policies is essential for safeguarding sensitive information.
- What Should Be Included?: Your data protection policy should outline how sensitive data should be handled, stored, and shared. It should also specify consequences for non-compliance. In my experience, having a well-defined policy helps employees understand the importance of protecting sensitive data while working remotely.
- Training on Policies: Ensure that all employees receive training on these policies during onboarding and at regular intervals thereafter. This reinforces their importance and keeps data protection top of mind.
Regular Audits and Compliance Checks
Conducting regular audits and compliance checks helps ensure that your organization adheres to established policies and identifies areas for improvement.
- Why Audits Are Important: Regular audits can reveal gaps in your security posture and help you address them before they become significant issues. I’ve participated in several audits that led to valuable insights about our security practices, allowing us to tighten our controls effectively.
- Compliance with Regulations: Ensure that your policies comply with relevant regulations (like GDPR or HIPAA) that govern data protection in your industry. This is crucial for maintaining trust with clients and stakeholders while also safeguarding against legal repercussions.
Implementing effective policies is essential for successfully securing remote work environments and enhancing your overall home office cybersecurity posture. By creating guidelines for acceptable remote work practices, utilizing Role-Based Access Control (RBAC), establishing an incident response plan, developing data protection policies, and conducting regular audits, organizations can significantly reduce their risk exposure in today’s digital landscape.
How Can Employers Support Their Remote Workforce?
Supporting your remote workforce is essential for maintaining productivity and security, especially when it comes to securing remote work environments. As someone who has navigated the complexities of remote team management, I can share effective strategies that employers can implement to enhance home office cybersecurity and foster a supportive work culture.
Providing Secure Tools and Resources
One of the most critical ways employers can support their remote workforce is by providing secure tools and resources that facilitate safe and efficient work.
- Invest in Security Software: Equip employees with reliable security software, including antivirus programs, VPNs, and endpoint protection tools. In my experience, when I transitioned to remote work, having access to these tools made a world of difference in my ability to protect sensitive data while securing remote work environments.
- Cloud-Based Collaboration Tools: Use cloud-based collaboration tools that prioritize security. Platforms like Microsoft Teams or Slack offer built-in security features that help protect sensitive information during communication and file sharing. I’ve found that using these tools not only improves collaboration but also enhances our overall home office cybersecurity.
Encouraging Open Communication
Creating an environment where employees feel comfortable discussing security concerns is vital for securing remote work environments.
- Regular Check-Ins: Schedule regular one-on-one check-ins with team members to discuss any challenges they may face while working remotely. This creates a supportive atmosphere where employees can voice their concerns about cybersecurity without fear of judgment.
- Feedback Mechanism: Establish a feedback mechanism for reporting suspicious activities or potential vulnerabilities. When I implemented this in my team, it led to quicker identification of potential threats, enhancing our overall security posture.
Offering Cybersecurity Training
Providing ongoing cybersecurity training is essential for keeping employees informed about the latest threats and best practices.
- Regular Training Sessions: Schedule regular training sessions focused on topics like phishing awareness, password management, and secure file-sharing practices. I’ve seen how effective training can empower employees to recognize threats and take proactive measures in securing remote work environments.
- Interactive Learning Opportunities: Consider using interactive learning methods such as quizzes or simulations to engage employees actively. For instance, conducting phishing simulations has proven effective in reinforcing awareness among team members while also making learning fun.
Promoting Work-Life Balance
Supporting your remote workforce also means promoting a healthy work-life balance, which can indirectly impact security.
- Flexible Hours: Allow flexible working hours to accommodate personal responsibilities. When employees feel supported in their personal lives, they are less likely to experience burnout, which can lead to careless security practices. I’ve noticed that teams with flexible schedules tend to be more engaged and vigilant about their cybersecurity responsibilities.
- Encourage Breaks: Remind employees to take regular breaks to recharge mentally and physically. A well-rested employee is more likely to remain alert and recognize potential security threats while working remotely.
Providing Access to IT Support
Ensuring that your remote workforce has access to IT support is crucial for addressing technical issues promptly.
- Dedicated IT Helpdesk: Set up a dedicated IT helpdesk that employees can contact for immediate assistance with security-related issues or technical difficulties. I’ve found that having quick access to support significantly reduces downtime and enhances overall productivity while also contributing to securing remote work environments.
- Resource Library: Create a resource library with guides and FAQs related to cybersecurity best practices. This empowers employees to find answers independently while reinforcing the importance of maintaining strong home office cybersecurity.
Employers play a vital role in supporting their remote workforce by providing secure tools, encouraging open communication, offering ongoing training, promoting work-life balance, and ensuring access to IT support. By focusing on these strategies, organizations can significantly enhance their efforts in securing remote work environments, ultimately leading to a more productive and secure workplace.
What Are the Future Trends in Remote Work Security?
As the landscape of remote work continues to evolve, so too do the strategies for securing remote work environments. Staying ahead of emerging trends is crucial for organizations aiming to enhance their home office cybersecurity. Drawing from my experience and observations in the tech industry, I can share some key trends that will shape the future of remote work security.
The Rise of Zero Trust Security Models
One of the most significant trends in remote work security is the adoption of Zero Trust security models. This approach operates on the principle that no one—inside or outside the organization—should be trusted by default.
- Why Zero Trust?: The traditional perimeter-based security model is becoming obsolete as more employees work remotely. By implementing a Zero Trust model, organizations can ensure that every access request is thoroughly vetted, which is essential for securing remote work environments. I’ve seen companies successfully reduce their risk exposure by adopting this model.
- Continuous Monitoring: Zero Trust requires continuous monitoring and verification of user identities and device health. This proactive approach helps organizations identify potential threats before they escalate, significantly enhancing home office cybersecurity.

Increased Use of Artificial Intelligence (AI)
Artificial Intelligence (AI) is becoming a game-changer in the realm of cybersecurity, particularly for securing remote work environments.
- Threat Detection: AI can analyze vast amounts of data to identify patterns and anomalies that may indicate a security threat. I’ve witnessed organizations leverage AI to enhance their threat detection capabilities, allowing them to respond more quickly to potential breaches.
- Automated Responses: AI-driven tools can automate responses to common security incidents, reducing the burden on IT teams and allowing them to focus on more complex issues. This trend is particularly beneficial for organizations with limited resources dedicated to cybersecurity.
Enhanced Focus on Employee Training and Awareness
As threats become more sophisticated, organizations are placing greater emphasis on employee training and awareness as part of their strategy for securing remote work environments.
- Ongoing Education: Companies are increasingly recognizing that employees are often the first line of defense against cyber threats. Regular training sessions focused on current threats and best practices are becoming standard practice. I’ve seen how regular training not only empowers employees but also fosters a culture of vigilance around home office cybersecurity.
- Gamification of Training: To make training more engaging, some organizations are turning to gamification techniques. By incorporating elements like quizzes, competitions, and rewards, companies can boost participation and retention rates among employees.
Secure Access Service Edge (SASE)
Secure Access Service Edge (SASE) is another emerging trend that combines networking and security into a single cloud-based service.
- Why SASE?: SASE offers a comprehensive solution for organizations looking to manage network traffic securely while accommodating remote workers. By integrating security functions like secure web gateways and firewalls with WAN capabilities, SASE simplifies the process of securing remote work environments.
- Scalability: As organizations grow and adapt to changing workforce dynamics, SASE provides a scalable solution that can easily accommodate new users and devices without compromising security.
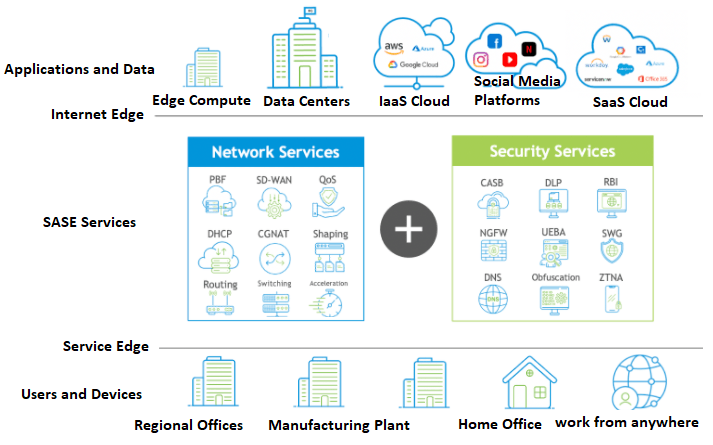
Greater Emphasis on Data Privacy Regulations
With increasing concerns about data privacy, organizations must stay compliant with evolving regulations such as GDPR and CCPA.
- Compliance as a Priority: As remote work becomes more prevalent, ensuring compliance with data privacy regulations will be essential for maintaining trust with clients and stakeholders. I’ve seen companies invest in compliance training programs to educate employees about their responsibilities regarding data protection while working remotely.
- Data Protection Technologies: Organizations are increasingly adopting technologies designed specifically for data protection, such as Data Loss Prevention (DLP) tools and encryption solutions. These technologies play a vital role in enhancing home office cybersecurity while ensuring compliance with regulations.
The future of remote work security will be shaped by trends such as Zero Trust models, AI integration, enhanced employee training, SASE adoption, and increased focus on data privacy regulations. By staying informed about these trends and adapting strategies accordingly, organizations can significantly improve their efforts in securing remote work environments, ensuring a safer and more productive workplace for everyone involved.
Final Thoughts on Maintaining a Secure Remote Work Environment
As we wrap up our discussion on securing remote work environments, it’s essential to recognize that maintaining a secure remote work environment is an ongoing process. The landscape of cybersecurity is constantly evolving, and organizations must adapt their strategies to stay ahead of emerging threats. Drawing from my experiences and insights, here are some key takeaways that can help you enhance your home office cybersecurity.
Proactive Approach to Security
Taking a proactive approach to security is vital for securing remote work environments effectively. This means not only implementing security measures but also continuously evaluating and updating them.
- Regular Security Audits: Conduct regular security audits to identify vulnerabilities in your systems and processes. I’ve found that these audits often reveal gaps that can be easily addressed, significantly improving overall security posture.
- Stay Informed: Keep abreast of the latest cybersecurity trends and threats. Subscribing to industry newsletters or following cybersecurity blogs can provide valuable insights that help you anticipate potential risks to your remote work setup.
Foster a Culture of Security Awareness
Creating a culture of security awareness among employees is crucial for securing remote work environments. When everyone in the organization understands the importance of cybersecurity, they are more likely to take it seriously.
- Encourage Open Dialogue: Foster an environment where employees feel comfortable discussing security concerns or reporting suspicious activities. I’ve seen how open communication can lead to quicker identification of potential threats and better overall security.
- Recognize Good Practices: Acknowledge and reward employees who demonstrate good cybersecurity practices. This not only motivates others to follow suit but also reinforces the importance of maintaining strong security measures in a remote work setting.
Leverage Technology Wisely
Employing the right technology is essential for enhancing home office cybersecurity.
- Invest in Robust Security Tools: Ensure that your organization is equipped with the latest security tools, such as endpoint protection, VPNs, and DLP solutions. These tools play a significant role in securing remote work environments and protecting sensitive data from unauthorized access.
- Utilize Cloud Solutions: Cloud-based solutions often come with built-in security features that can simplify the management of remote work environments. I’ve found that using reputable cloud services not only enhances security but also improves collaboration among team members.
Regular Training and Education
Ongoing training and education are critical components of maintaining a secure remote work environment.
- Continuous Learning Opportunities: Provide employees with regular training sessions focused on current threats and best practices for securing remote work environments. This ensures that everyone remains informed about potential risks and knows how to respond effectively.
- Simulations and Drills: Conduct phishing simulations and other drills to keep employees engaged and aware of potential threats. These practical exercises help reinforce learning while also preparing employees for real-world scenarios.
In conclusion, maintaining a secure remote work environment requires a multifaceted approach that includes proactive security measures, fostering a culture of awareness, leveraging technology wisely, and providing ongoing training. By focusing on these areas, organizations can significantly enhance their efforts in securing remote work environments, ensuring both productivity and safety for their workforce.
Frequently Asked Questions (F.A.Q.s)
What are the most common cybersecurity threats in remote work?
Common threats include phishing attacks, malware, ransomware, and unsecured Wi-Fi networks. These risks can compromise sensitive data and disrupt business operations, making it essential to be vigilant and proactive in securing remote work environments.
How can I secure my home Wi-Fi network effectively?
To secure your home Wi-Fi, change the default password, enable WPA3 encryption, and regularly update your router’s firmware. Additionally, consider setting up a guest network for visitors to keep your main network secure while securing remote work environments.
What is a VPN, and why is it important for remote work?
A Virtual Private Network (VPN) encrypts your internet connection, making it more secure when accessing sensitive information remotely. Using a VPN is crucial for securing remote access and protecting your data from potential threats.
How often should I update my passwords?
It’s best to update your passwords every three to six months or immediately if you suspect a breach. Use strong, unique passwords for each account to enhance your home office cybersecurity.
What should I do if I suspect a phishing attack?
If you suspect a phishing attack, do not click on any links or download attachments. Report the email to your IT department or security team and delete it immediately. Educating employees on recognizing phishing attempts is vital for securing remote work environments.
How can I safely share files while working remotely?
Use encrypted file-sharing services like Google Drive or Dropbox with added security features. Always password-protect sensitive files before sharing them via email to enhance the security of your data.
What are the best practices for using personal devices for work?
Implement a Bring Your Own Device (BYOD) policy that includes guidelines for securing personal devices. Encourage employees to use endpoint protection software, enable device encryption, and regularly update their operating systems to maintain home office cybersecurity.
Why is employee training essential for cybersecurity?
Employee training is crucial because human error is often the weakest link in cybersecurity. Regular training sessions help employees recognize threats and understand best practices for securing remote work environments, ultimately reducing the risk of breaches.
How can organizations ensure compliance with remote work policies?
Regular audits and compliance checks can help ensure that employees adhere to established remote work policies. Providing ongoing training and clear communication about expectations also reinforces compliance within the organization.
What are the signs that my home network has been compromised?
Signs of a compromised network may include slow internet speeds, unexpected pop-ups, unfamiliar devices connected to your network, or unusual activity on your accounts. If you notice any of these signs, take immediate steps to secure your network and investigate further. This FAQ section aims to address common concerns regarding securing remote work environments and provide actionable insights for enhancing home office cybersecurity.